Grafana Patches Critical Vulnerability Allowing Administrator Impersonation

Grafana Labs developers have issued a warning about a critical vulnerability, CVE-2025-41115 (rated 10 out of 10 on the CVSS scale), in Grafana Enterprise. The flaw allows attackers to impersonate an administrator or another internal account through the creation of a new user.
Exploitation Requirements
The vulnerability can only be exploited when the SCIM provisioning (System for Cross-domain Identity Management) feature is enabled. Specifically, both the enableSCIM flag and the user_sync_enabled option must be set to true.
Under these conditions, a malicious or compromised SCIM client can create a user with a numeric externalId that maps to an internal account, including administrator accounts.
Technical Details
The externalId is a SCIM account attribute used by identity providers to track users. Grafana directly mapped this value to its internal user.uid, meaning a numeric externalId (such as "1") could be interpreted as an existing internal account. This created opportunities for administrator impersonation, user impersonation, and privilege escalation.
According to official Grafana documentation, SCIM provisioning is currently in Public Preview status with limited support, so not all users have this feature enabled.
Affected Versions and Patches
CVE-2025-41115 affects Grafana Enterprise versions 12.0.0 through 12.2.1 (only when SCIM is enabled). Grafana OSS users are not affected, and Grafana Cloud (including Amazon Managed Grafana and Azure Managed Grafana) has already been patched.
Administrators of self-managed installations should update to versions 12.3.0, 12.2.1, 12.1.3, or 12.0.6 immediately. Disabling SCIM can serve as a temporary mitigation measure.
Discovery and Response
The vulnerability was discovered during an internal audit on November 4, 2025, and a patch was released within 24 hours. Grafana Labs representatives state they conducted an investigation and determined the vulnerability was not exploited in Grafana Cloud.
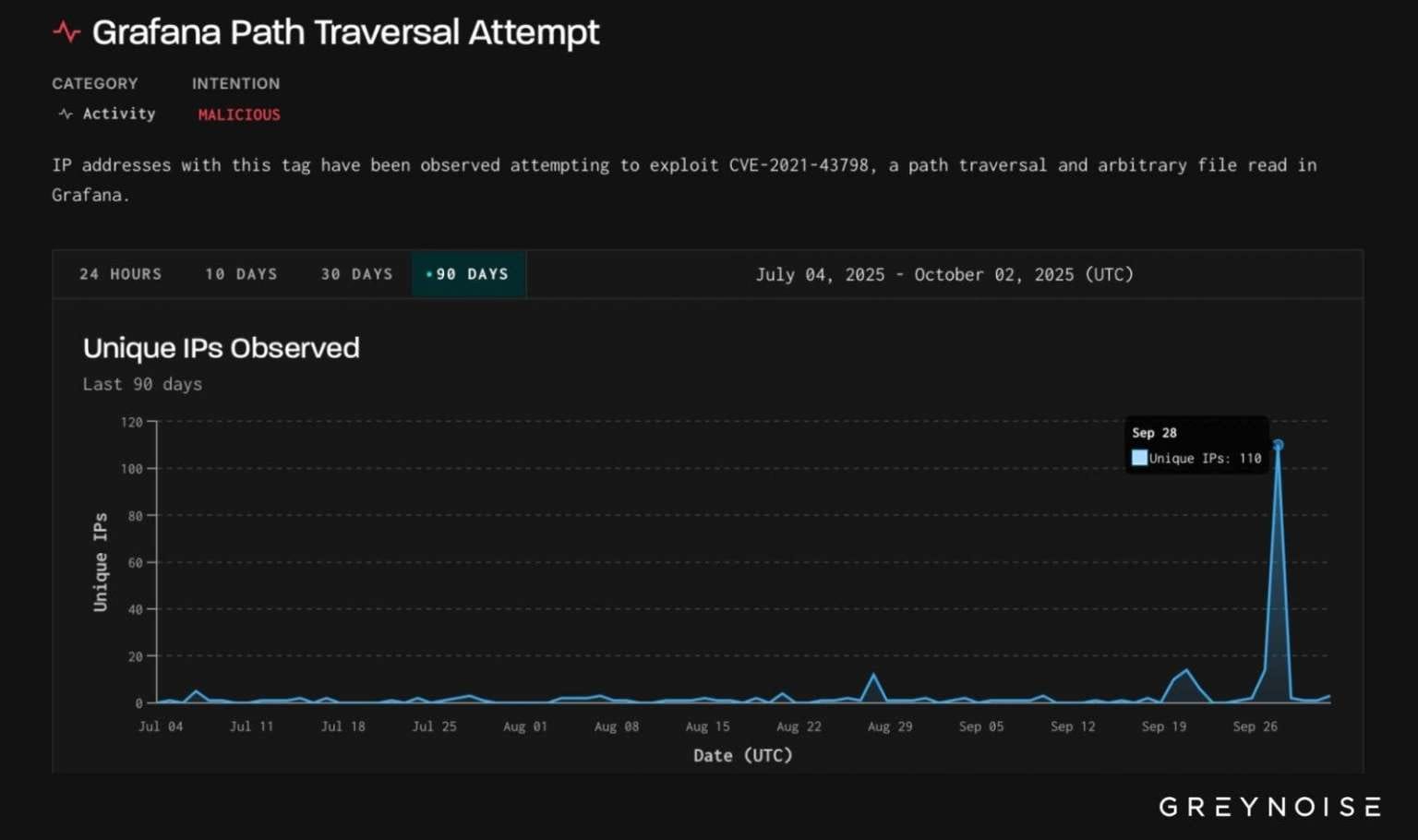
Last month, analysts from cybersecurity company GreyNoise warned about unusually high scanning activity targeting an old path traversal vulnerability in Grafana. This suggests threat actors may have been searching for accessible instances in anticipation of the new vulnerability's disclosure.
"Customers received fixes in advance, and we also worked under embargo with cloud providers licensed for Grafana Cloud Pro to protect their environments prior to the public disclosure of the issue," Grafana Labs CISO Joe McManus told the media. "Importantly, Grafana OSS users are not affected. We strongly recommend all affected customers update to the latest patched version as soon as possible."


