Google Uncovers BadAudio Malware in APT24 Espionage Campaigns

Researchers from the Google Threat Intelligence Group (GTIG) have revealed details of a three-year espionage campaign conducted by the Chinese threat group APT24. The hackers deployed previously undocumented malware called BadAudio in their operations.
APT24 (also tracked as Pitty Tiger) targets government institutions and organizations across multiple sectors—including healthcare, construction and engineering, mining, non-profit organizations, and telecommunications—primarily in the United States and Taiwan. According to Google, the group specializes in stealing intellectual property, specifically information that gives organizations a competitive advantage in their industries.
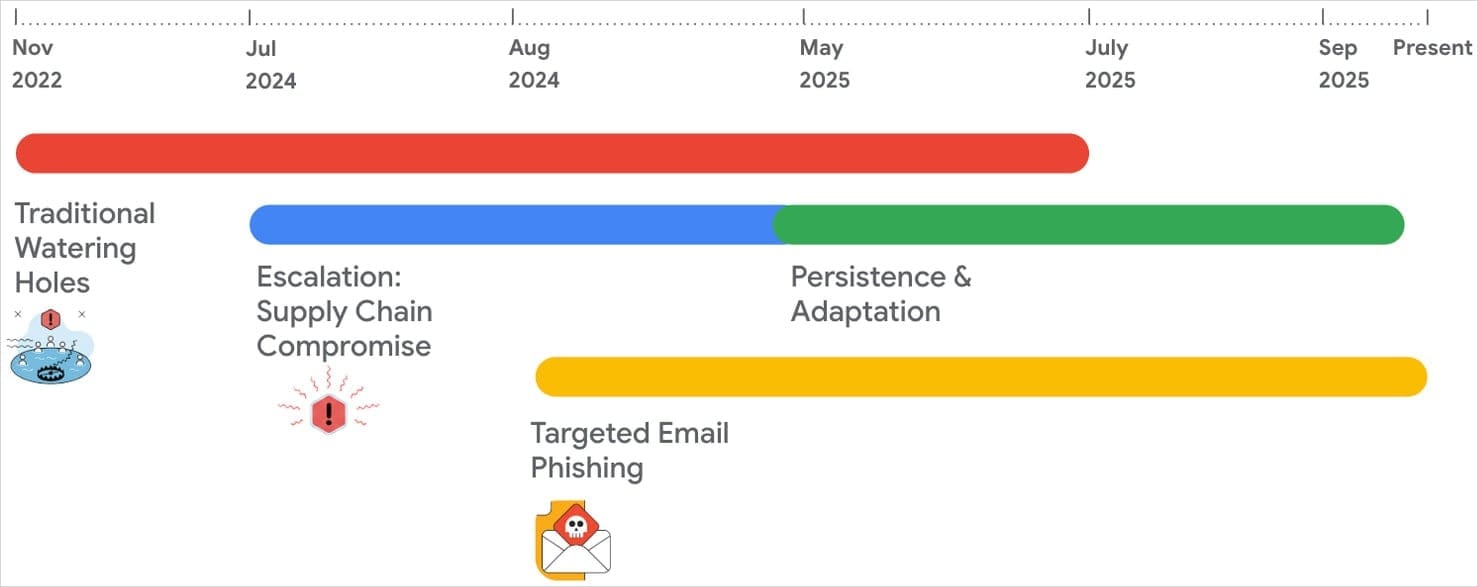
Multiple Infection Vectors
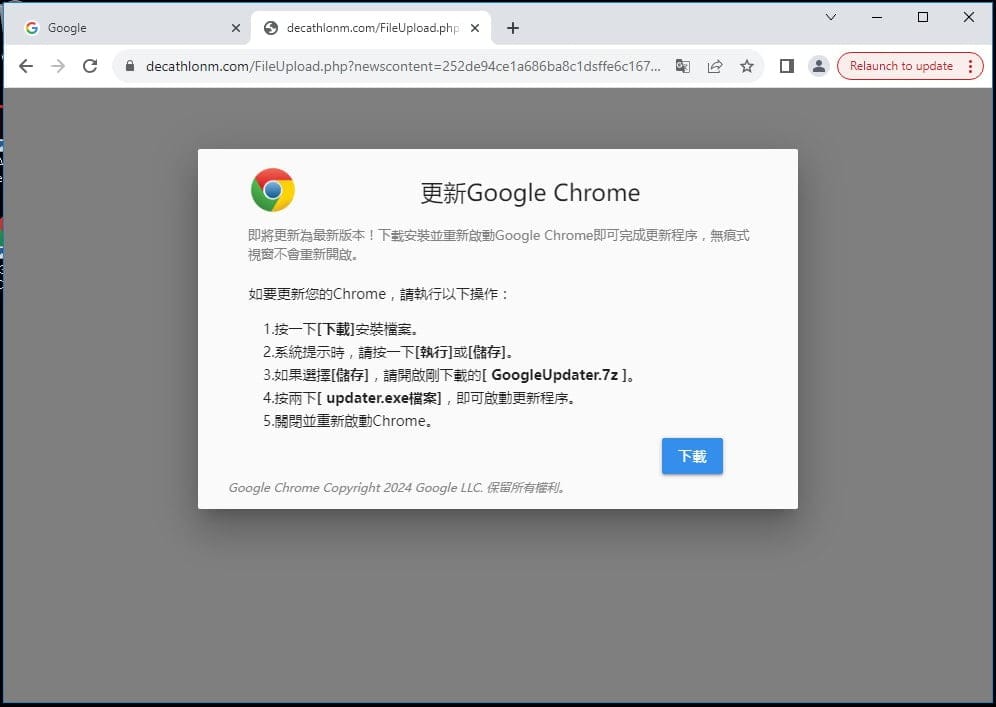
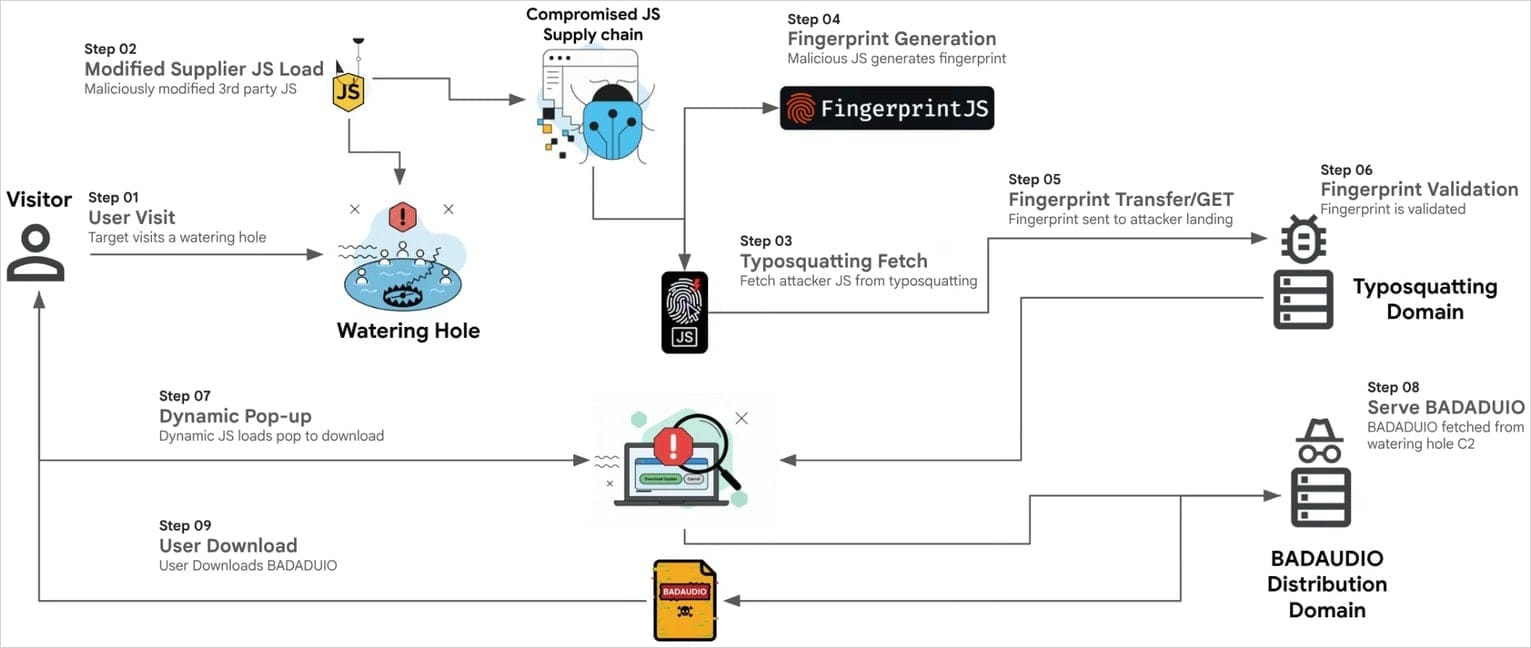
Since 2022, the malware has reached victims through several attack methods, including targeted phishing, supply chain compromises, and watering hole attacks. Between November 2022 and September 2025, APT24 compromised over 20 legitimate websites across various domains by injecting malicious JavaScript into their code. The script fingerprinted visitors (targeting only Windows systems) and displayed a fake pop-up window claiming that a software update was required. The window actually triggered the download of BadAudio malware.
Supply Chain Attacks
Researchers report that starting in July 2024, the threat actors repeatedly breached an unnamed Taiwanese marketing company that provides JavaScript libraries to its clients. The attackers injected malicious code into a popular library and registered a domain impersonating a legitimate CDN. This campaign ultimately compromised over 1,000 domains.
Between late 2024 and July 2025, APT24 targeted the same Taiwanese firm again. This time, the threat actors injected obfuscated JavaScript into a modified JSON file. When executed, the script collected information about website visitors and transmitted a base64-encoded report to a command-and-control server.
Phishing Campaign
Parallel to the supply chain attacks, APT24 launched targeted email phishing campaigns starting in August 2024. The hackers impersonated animal rescue organizations in these messages, which contained hidden tracking pixels to confirm when recipients opened the emails.
Researchers note that in some attacks, Google Drive and OneDrive were used for data collection instead of the hackers' own servers, although such abuse was frequently blocked. In at least one instance, researchers observed the deployment of a Cobalt Strike beacon via BadAudio.
Technical Analysis of BadAudio
BadAudio is a heavily obfuscated loader that exploits the DLL search order hijacking technique, which allows the malicious payload to be loaded by legitimate applications.
The malware uses a sophisticated obfuscation method that fragments linear code into disconnected blocks controlled by a central "dispatcher." This approach complicates both automated and manual analysis.
After execution, BadAudio collects basic system data—hostname, username, and architecture information—encrypts it with a hardcoded AES key, and transmits it to the attackers' server. An encrypted payload is then downloaded, decrypted, and executed in memory via DLL sideloading.
Low Detection Rates
Researchers emphasize that of the eight discovered BadAudio samples, only two are detected by more than 25 antivirus engines on VirusTotal. The remaining samples (created on December 7, 2022) are flagged by a maximum of five security solutions, highlighting the malware's effectiveness at evading detection.


