Google Sues Developers of Lighthouse Phishing Kit

Google has filed a lawsuit against the operators of Lighthouse, a phishing-as-a-service (PhaaS) platform that cybercriminals worldwide use to steal bank card data. The attackers primarily operate through SMS messages, impersonating the United States Postal Service (USPS) and the E-ZPass toll payment system.
Scale of the Operation
According to Google's estimates, Lighthouse has affected over one million people across 120 countries. In the United States alone, from July 2023 to October 2024, attackers stole data from approximately 115 million payment cards.
In its lawsuit, Google demands complete dismantling of the platform's infrastructure, citing violations of federal racketeering, fraud, and computer crime laws.
How Lighthouse Works
Lighthouse offers a turnkey solution for cybercriminals. The platform provides ready-made phishing templates and all the infrastructure needed to conduct bulk SMS campaigns.
In a typical attack, threat actors impersonate well-known services like USPS or E-ZPass and send messages demanding immediate payment of a non-existent debt—for example, an allegedly unpaid toll road fee. Links in these SMS messages direct victims to fake websites mimicking legitimate toll road or postal service sites, where users are prompted to enter their card details to pay the fabricated "debt."
The hackers also impersonate banks, medical organizations, payment systems, law enforcement agencies, and social media platforms. By sending phishing messages via iMessage and RCS, the fraudsters bypass many spam filters that would catch traditional SMS-based attacks.
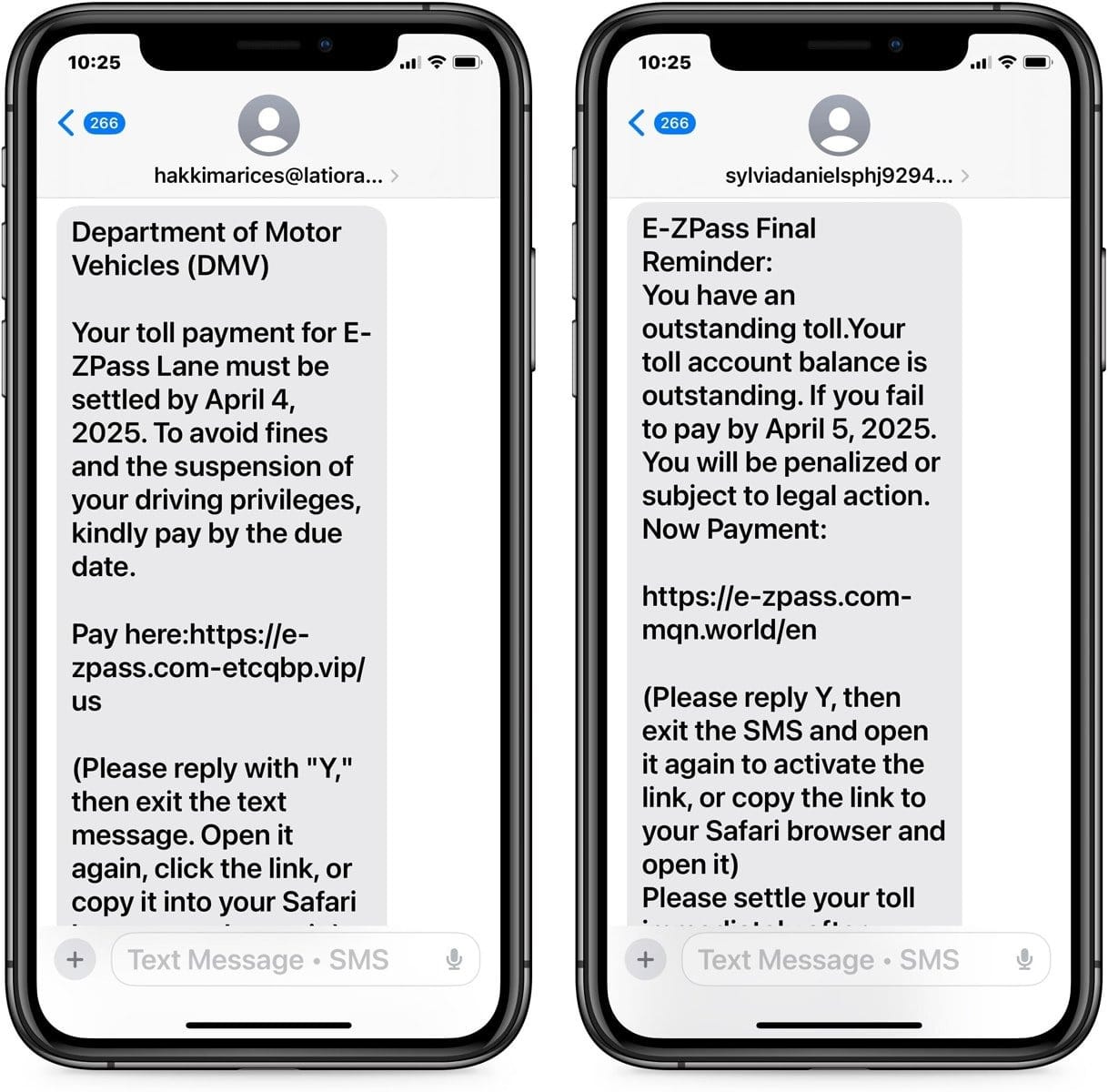
Abuse of Google's Brand
The threat actors actively exploit Google's branding to gain victims' trust. The company discovered at least 107 phishing templates that incorporated Google's logos and interface elements on fraudulent login pages.
"They unlawfully exploit the reputation of Google and other brands by placing our trademarks on fraudulent resources," Google stated in its filing.
Attribution and Business Model
Cisco Talos researchers previously linked Lighthouse to a Chinese threat actor operating under the alias Wang Duo Yu. He sells and supports various phishing kits through Telegram channels.
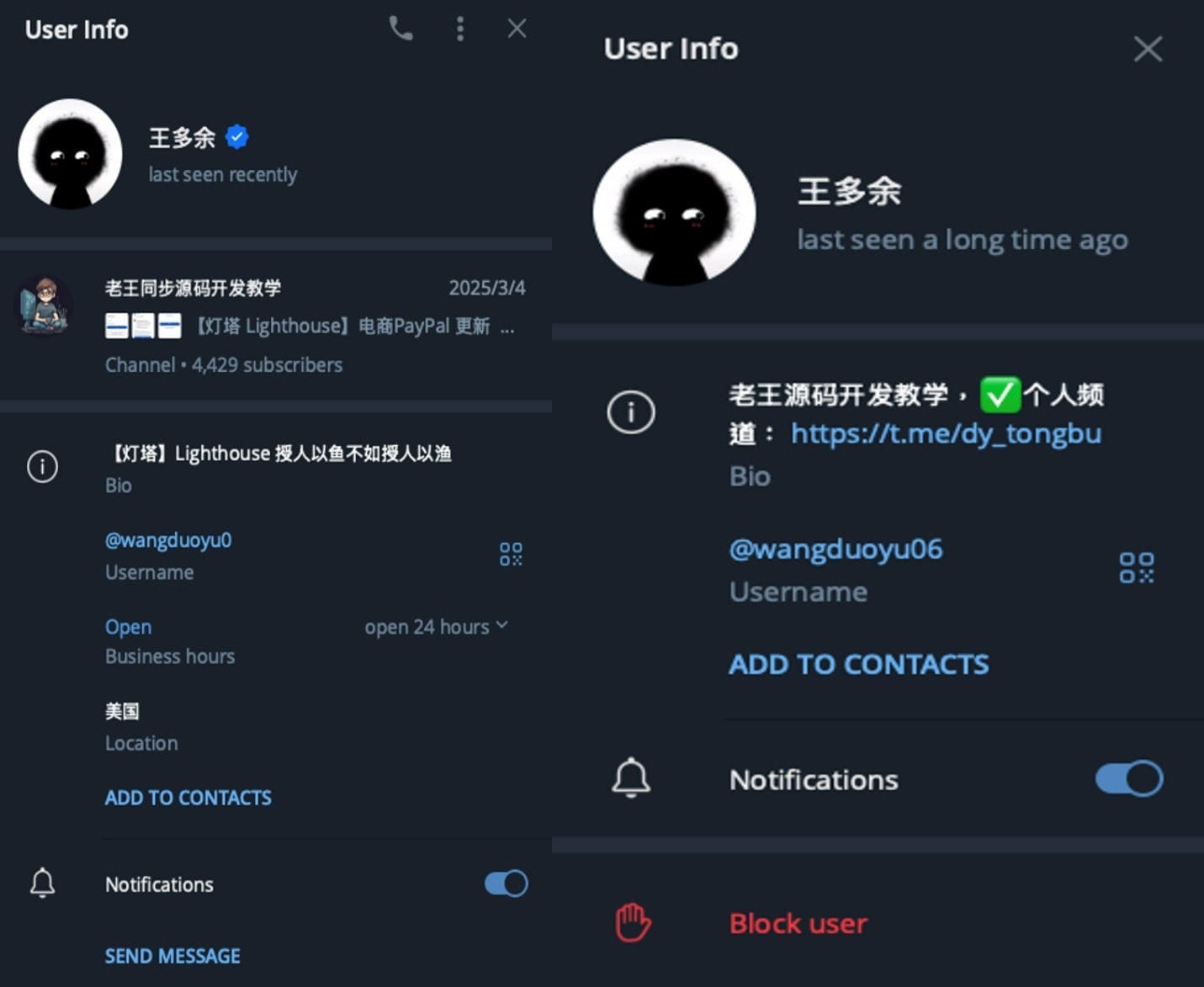
Since October 2024, several hacker groups using his tools have conducted large-scale campaigns in Washington, Florida, Pennsylvania, Virginia, Texas, Ohio, Illinois, and Kansas—all involving fake E-ZPass unpaid invoice notifications.
Netcraft researchers note that Lighthouse operates as a purely commercial venture, with subscriptions ranging from $88 per week to $1,588 per year. The platform provides customizable templates designed to steal not only payment card data but also login credentials, passwords, and two-factor authentication codes.
Cybersecurity journalist Brian Krebs believes the group behind Lighthouse previously operated under the name Smishing Triad but underwent a "rebranding" in March 2025 and adopted the Lighthouse name.
Legal Strategy and Precedent
The lawsuit represents more than a symbolic gesture. Even without knowing the exact identities of Lighthouse's operators and creators, large companies can use court orders to obtain warrants for seizing domains and the right to demand technical information—such as IP addresses, logs, and payment details—from providers, registrars, and hosting companies. This process helps de-anonymize threat actors.
This tactic has proven effective before. Microsoft has successfully employed similar legal strategies in recent years against the ONNX and RaccoonO365 phishing services, using civil lawsuits to disrupt criminal infrastructure and gather intelligence on operators.
Significance
Google's legal action against Lighthouse highlights how major technology companies are increasingly using civil litigation as a tool to combat cybercrime. By targeting the infrastructure and business model of PhaaS platforms, these lawsuits can disrupt criminal operations even when prosecuting individual attackers remains challenging due to jurisdictional limitations.
The case also underscores the professionalization of cybercrime, where services like Lighthouse democratize sophisticated attacks by providing everything criminals need to launch phishing campaigns—lowering the technical barrier to entry and enabling widespread fraud.


