GlassWorm Worm Discovered in OpenVSX and VS Code

Koi Security researchers have uncovered a large-scale supply chain attack targeting both OpenVSX and the Visual Studio Code Marketplace. The attackers are distributing self-replicating malware known as GlassWorm, which has already been installed roughly 35,800 times.
Infected Extensions
Researchers identified twelve compromised extensions — eleven hosted on OpenVSX and one on Microsoft’s VS Code Marketplace:
- codejoy.codejoy-vscode-extension@1.8.3, 1.8.4
- l-igh-t.vscode-theme-seti-folder@1.2.3
- kleinesfilmroellchen.serenity-dsl-syntaxhighlight@0.3.2
- JScearcy.rust-doc-viewer@4.2.1
- SIRILMP.dark-theme-sm@3.11.4
- CodeInKlingon.git-worktree-menu@1.0.9, 1.0.91
- ginfuru.better-nunjucks@0.3.2
- ellacrity.recoil@0.7.4
- grrrck.positron-plus-1-e@0.0.71
- jeronimoekerdt.color-picker-universal@2.8.91
- srcery-colors.srcery-colors@0.3.9
- cline-ai-main.cline-ai-agent@3.1.3 (VS Code Marketplace)
How GlassWorm Operates
GlassWorm conceals its malicious payload using invisible Unicode characters—a tactic that makes it nearly undetectable in code reviews. It also exhibits worm-like behavior, spreading autonomously by using stolen credentials to infect other extensions tied to compromised developer accounts.
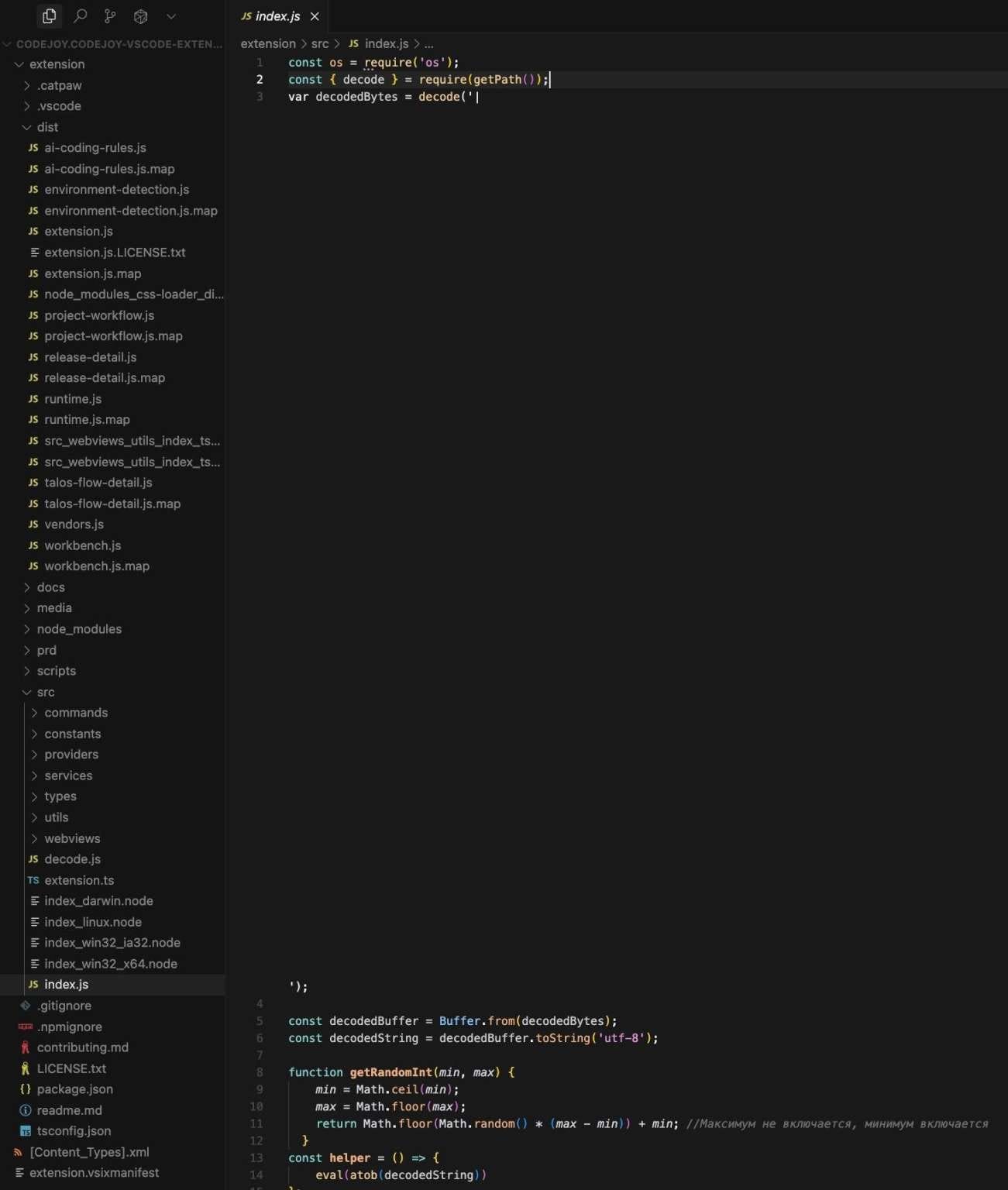
Its command-and-control (C2) infrastructure is unusually complex:
- Primary C2: Solana blockchain transactions containing Base64-encoded payload URLs.
- Backup C2: Google Calendar event titles carrying encoded URLs.
- Fallback: Direct connection to attacker-controlled IP address
217.69.3[.]218.
Capabilities and Objectives
Once installed, GlassWorm attempts to steal:
- GitHub, npm, and OpenVSX credentials
- Cryptocurrency wallet data from 49 popular extensions
It then deploys a SOCKS proxy to route malicious traffic through the victim’s machine and installs hidden VNC (HVNC) clients for covert remote access.
The final stage payload, named ZOMBI, is heavily obfuscated JavaScript that enrolls infected systems into a botnet.
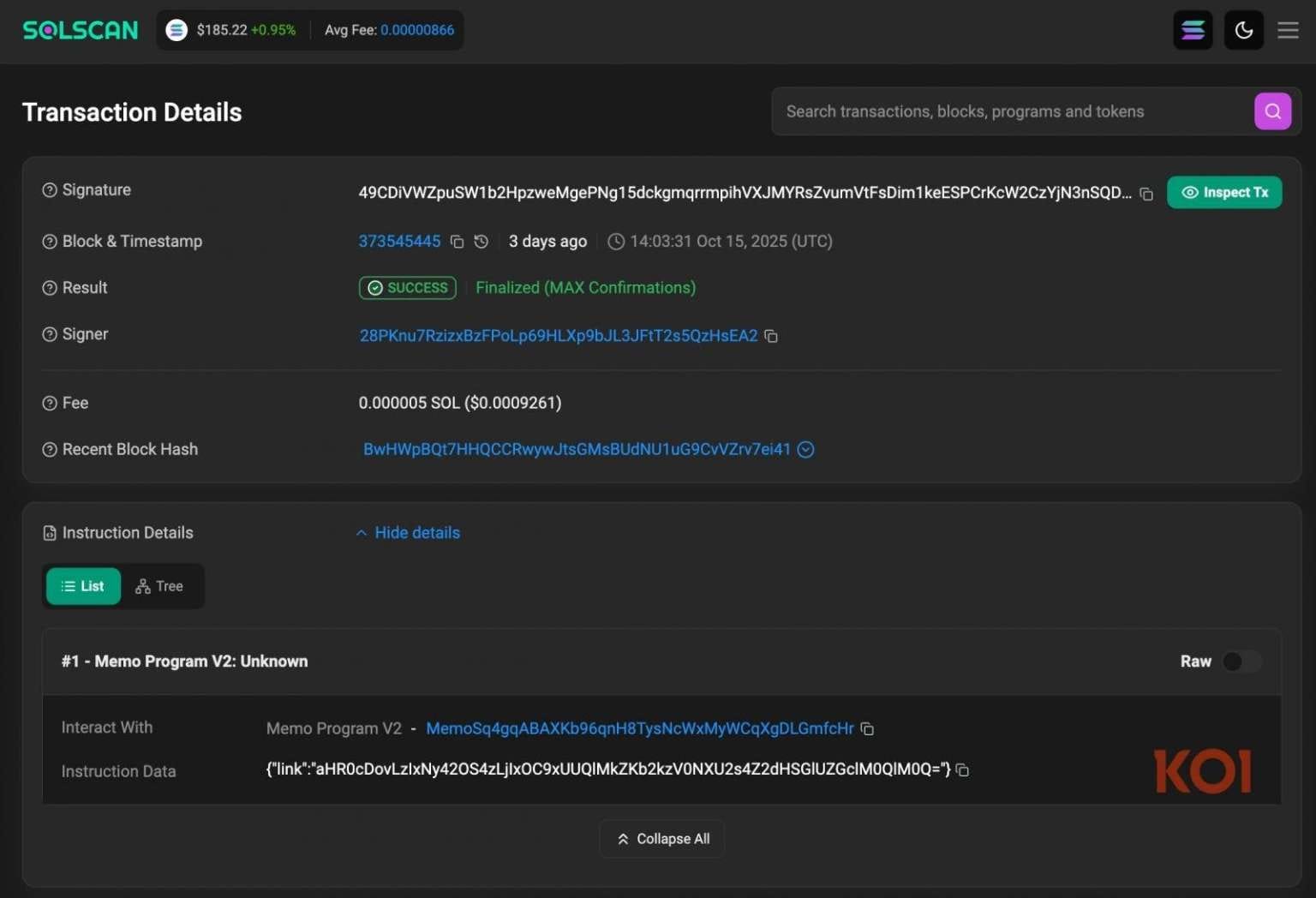
The malware also employs BitTorrent Distributed Hash Table (DHT) for decentralized command distribution, increasing its persistence and making takedowns more difficult.
Why It’s Serious
“This situation is particularly serious because VS Code extensions update automatically,” researchers explained. “When CodeJoy released version 1.8.3 with the invisible malware, every user who had the extension installed received the infected version automatically — no warnings, no prompts, no user action required.”
Response and Current Status
At the time of Koi Security’s report, four infected extensions remained available on OpenVSX. Microsoft, after being alerted, promptly removed the malicious extension from its marketplace. Some affected developers, such as those behind vscode-theme-seti-folder and git-worktree-menu, have since released clean versions.
Broader Context
Last month, a similar worm named Shai-Hulud targeted the npm ecosystem, compromising 187 packages. That malware used the TruffleHog scanner to extract secrets and API keys.
Koi Security describes GlassWorm as “one of the most sophisticated supply chain attacks to date and the first documented case of a self-replicating worm targeting VS Code.”
The researchers warn that GlassWorm’s infrastructure remains active and the campaign may still be ongoing.


