GlassWorm Malware Resurfaces in 24 Malicious Packages

GlassWorm malware has infiltrated Visual Studio Code extension repositories for the third time. Threat actors uploaded 24 new malicious packages to OpenVSX and the Microsoft Visual Studio Marketplace, despite two previous campaigns earlier this year.
Security researchers first identified GlassWorm in October 2025. The malware steals credentials from GitHub, npm, and OpenVSX, along with cryptocurrency wallet data and information from 49 different extensions. GlassWorm conceals malicious JavaScript code using invisible Unicode characters.
The malware functions as a worm, self-propagating through stolen credentials. After compromising a developer's account, GlassWorm infects other extensions the victim has access to. Attackers use the Solana blockchain to manage their botnet, with Google Calendar serving as a backup command-and-control channel.
The second GlassWorm campaign appeared in November, when operators deployed three new Visual Studio Code extensions on OpenVSX. The malware accumulated over 10,000 downloads despite enhanced security measures OpenVSX implemented after the first attack.
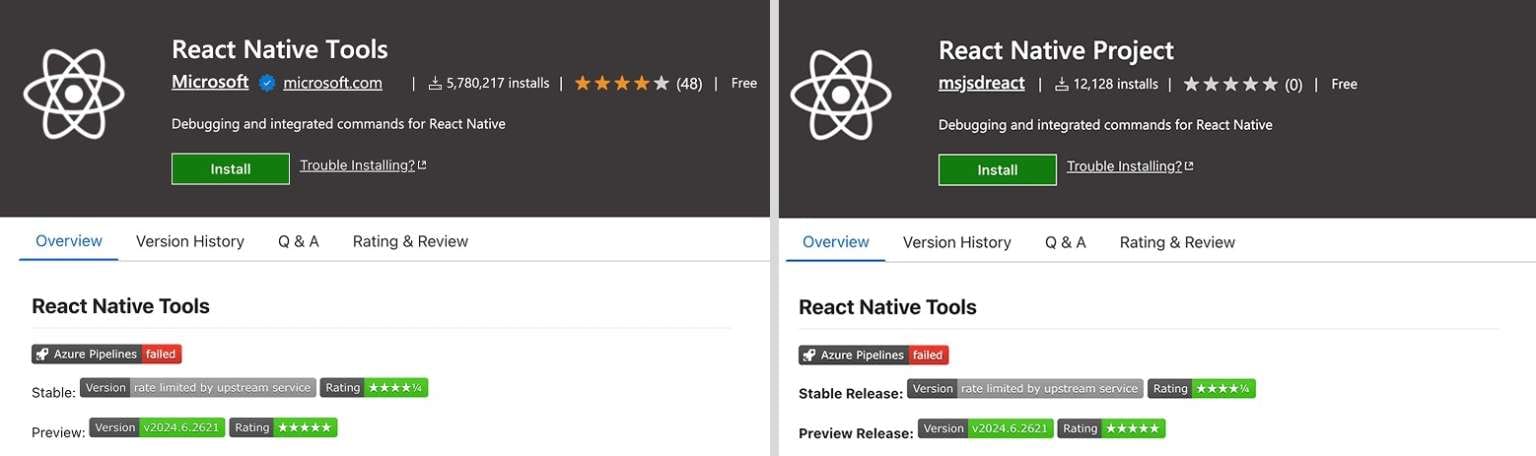
Secure Annex researchers detected the third wave this week. The attackers disguised malicious packages as popular development tools and frameworks, including Flutter, Vim, Yaml, Tailwind, Svelte, React Native, and Vue. Seventeen malicious packages appeared in the Microsoft Visual Studio Marketplace, with seven more on OpenVSX. One package existed on both platforms.
VS Code Marketplace:
- iconkieftwo.icon-theme-materiall (removed December 1, 2025)
- prisma-inc.prisma-studio-assistance (removed December 1, 2025)
- prettier-vsc.vsce-prettier
- flutcode.flutter-extension
- csvmech.csvrainbow
- codevsce.codelddb-vscode
- saoudrizvsce.claude-devsce
- clangdcode.clangd-vsce
- cweijamysq.sync-settings-vscode
- bphpburnsus.iconesvscode
- klustfix.kluster-code-verify
- vims-vsce.vscode-vim
- yamlcode.yaml-vscode-extension
- solblanco.svetle-vsce
- vsceue.volar-vscode
- redmat.vscode-quarkus-pro
- msjsdreact.react-native-vsce
Open VSX:
- bphpburn.icons-vscode
- tailwind-nuxt.tailwindcss-for-react
- flutcode.flutter-extension
- yamlcode.yaml-vscode-extension
- saoudrizvsce.claude-dev
- saoudrizvsce.claude-devsce
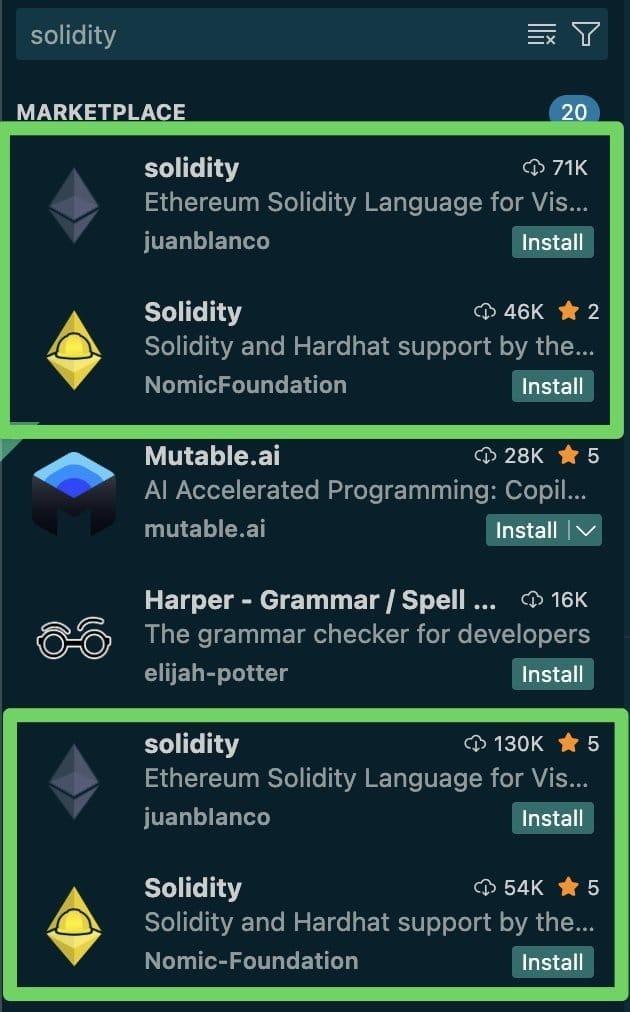
- vitalik.solidity
Attackers upload packages to marketplaces in a benign state, then release malicious updates later. They artificially inflate download counters to establish perceived legitimacy and trust. Higher download counts improve search rankings, placing the malware near legitimate projects it impersonates.
GlassWorm has evolved technically. The malware now deploys a Rust-based implant packed inside extensions, though some variants still use invisible Unicode characters to hide malicious code.
Bleeping Computer contacted OpenVSX and Microsoft for comment on why GlassWorm continues bypassing platform defenses. OpenVSX did not respond. Microsoft stated:
"We continue to improve our scanning and detection systems to prevent abuse. Microsoft encourages users to report suspicious content via the Report Abuse link available on every extension page."


