GlassWorm Malware Breaches OpenVSX Again

The hackers operating GlassWorm malware have breached OpenVSX for a second time, uploading three malicious Visual Studio Code extensions. This happened despite security improvements the platform implemented after the first attack. The infected extensions accumulated over 10,000 downloads before detection.
Background: The October 2025 Discovery
Security researchers first identified GlassWorm in October 2025. The malware targets developer credentials from GitHub, npm, and OpenVSX platforms. It also steals cryptocurrency wallet data from infected systems.
GlassWorm's design includes two notable features. First, it hides malicious JavaScript code using invisible Unicode characters, making detection difficult. Second, it operates as a worm—it spreads automatically by using stolen credentials to infect other extensions the compromised accounts can access.
The attackers manage their botnet through the Solana blockchain, with Google Calendar serving as a backup command channel.
The First Wave
During the October campaign, hackers planted 12 infected extensions across OpenVSX and the Visual Studio Code Marketplace. Official statistics showed approximately 35,800 downloads. However, security experts suspect the attackers artificially inflated these numbers, so the actual victim count remains unknown.
After researchers exposed the campaign, OpenVSX developers revoked access tokens for compromised accounts and added new security measures.
The Second Breach
Researchers from Koi Security, who monitor GlassWorm activity, discovered three new malicious extensions in OpenVSX:
- ai-driven-dev.ai-driven-dev — 3,400 downloads
- history-in-sublime-merge — 4,000 downloads
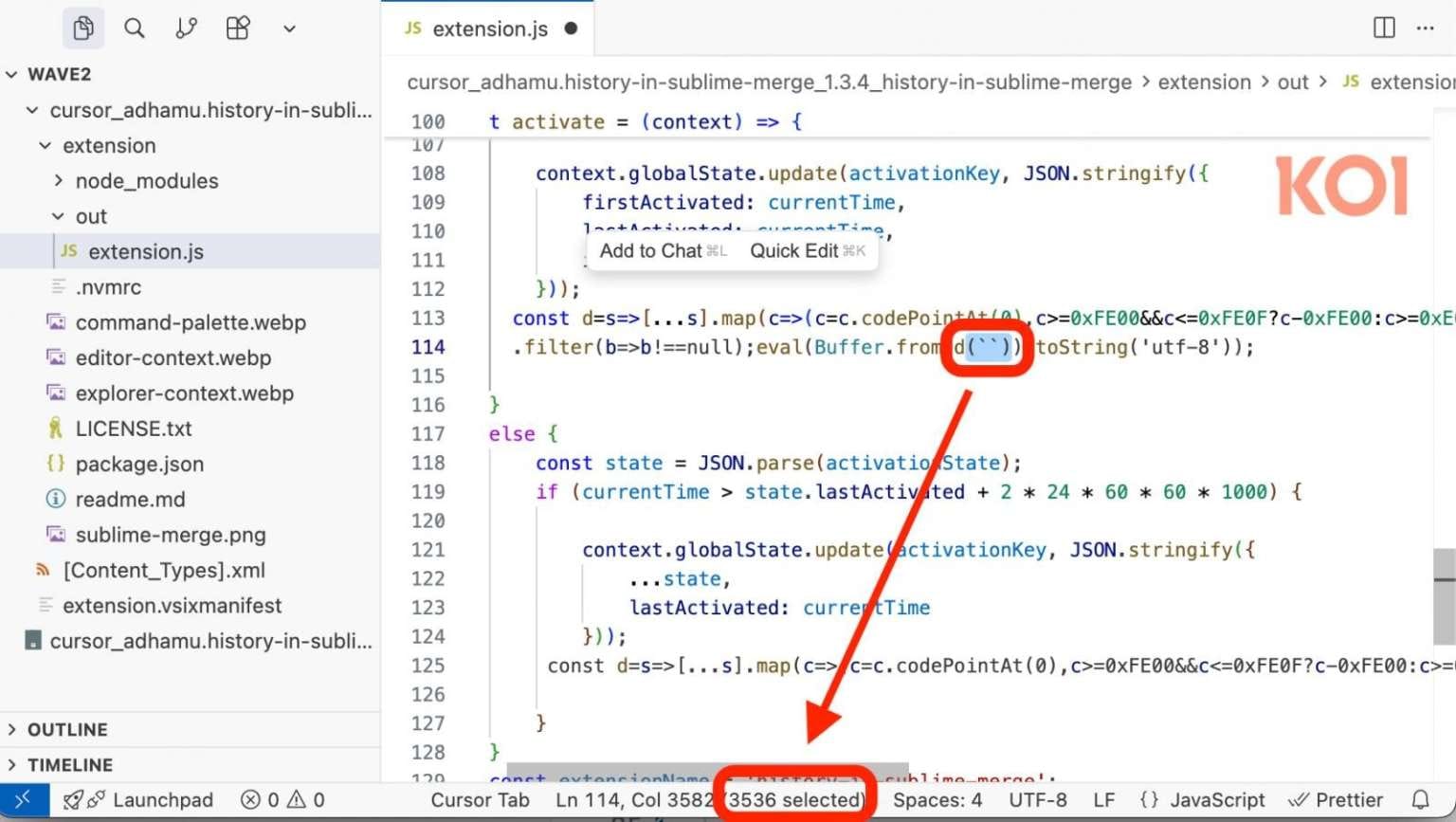
- transient-emacs — 2,400 downloads
All three extensions use the same Unicode character obfuscation technique, demonstrating that OpenVSX's new protection measures failed to block this attack method.
Analysts from Aikido recently warned that GlassWorm operators have expanded their campaign to GitHub as well.
Inside the Operation
Koi Security specialists gained access to the attackers' server following an anonymous tip. Data from the server revealed the campaign's scope: victims span the United States, South America, Europe, and Asia. The malware has also penetrated government systems in the Middle East.
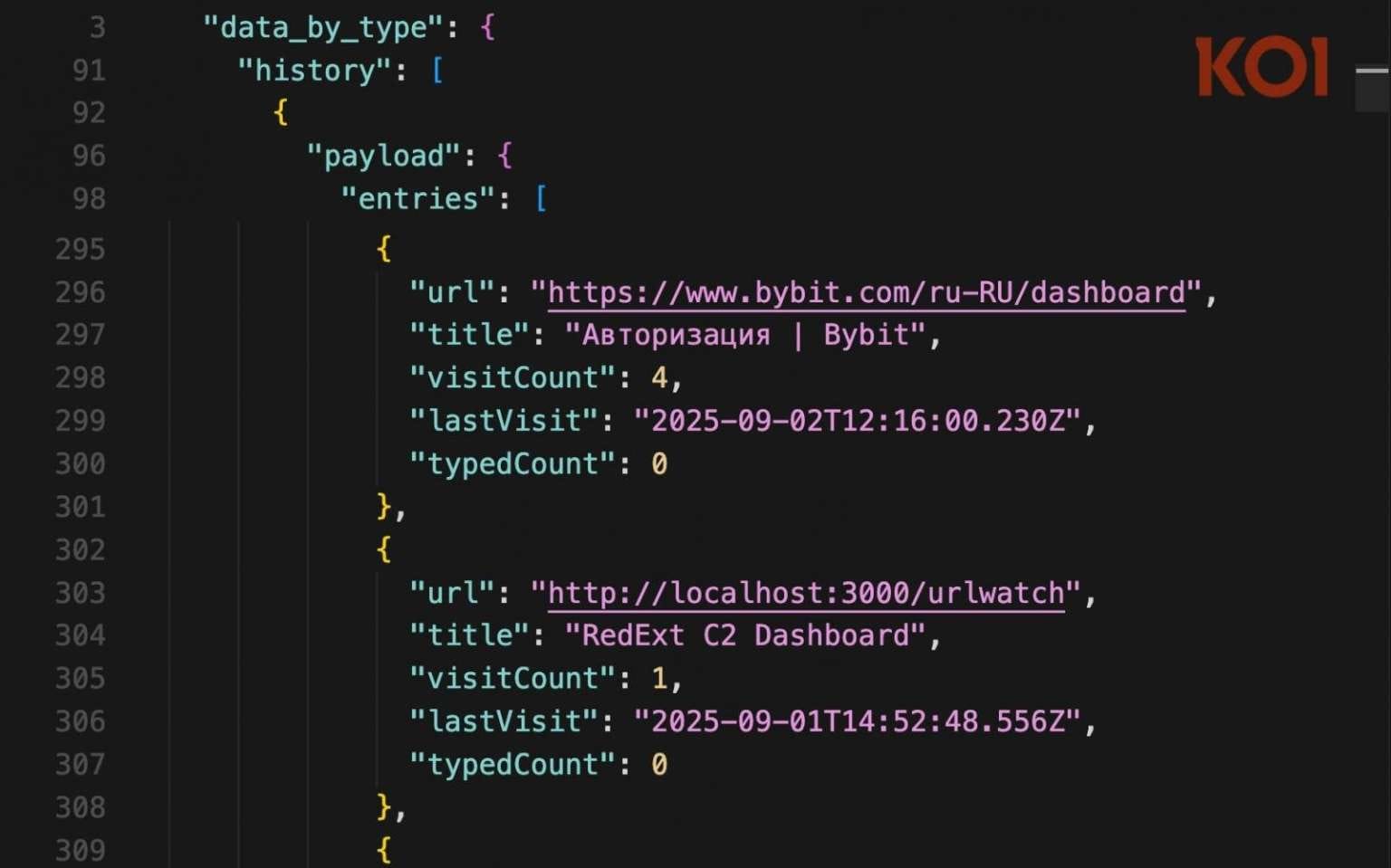
The research team determined the malware operators are Russian-speaking and use the open-source RedExt framework.
Law Enforcement Coordination
Koi Security has provided all collected intelligence to law enforcement agencies, including the operators' identities on cryptocurrency exchanges and messaging platforms. The team is now working with authorities to develop a notification plan for affected organizations.
What This Means
In my opinion, this second breach raises serious questions about extension marketplace security. The attackers defeated enhanced protections using the same obfuscation technique that worked in October. Organizations using Visual Studio Code extensions need to verify their development environments weren't compromised.
Furthermore, the discovery that GlassWorm has penetrated government systems shows this isn't just a developer nuisance—it's become a significant security threat. The combination of credential theft and cryptocurrency wallet targeting suggests financially motivated actors with technical sophistication.
The fact that the same Unicode obfuscation technique succeeded twice indicates marketplace platforms need stronger detection capabilities. Relying on post-breach token revocation isn't sufficient when attackers can repeatedly bypass defenses using known methods.


