DeliveryRAT Android Trojan Now Launches DDoS Attacks

Security researchers at F6 have analyzed an updated version of DeliveryRAT, an Android Trojan that continues to expand its capabilities. This malware disguises itself as legitimate applications—food delivery services, online marketplaces, banking apps, and package tracking tools. The latest version, which appeared in the second half of 2025, added several dangerous features. The Trojan now conducts DDoS attacks and deploys fake interface screens to steal additional data from victims.
Three Major Capability Additions
The updated DeliveryRAT builds on its original data-stealing functions with three significant upgrades. Each addition makes the malware more dangerous and versatile.
DDoS Attack Module
First, the Trojan now includes a module dedicated to DDoS attacks. Here's how it works: The command server sends the infected device a target URL, specifies the number of requests to make, and provides parameters for those requests. The compromised device then bombards the target with traffic. After completing the attack, the malware reports back to its operators. This report includes the count of successful requests and failed attempts.
This capability transforms DeliveryRAT from a simple data stealer into a tool for disrupting online services. Infected devices become part of a mobile botnet, participating in attacks without their owners knowing.
Dynamic Activity System
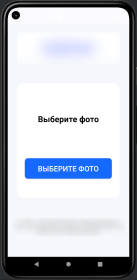
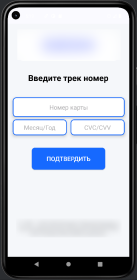
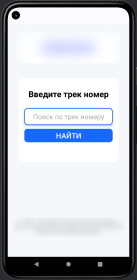
Second, the malware operators can now remotely launch five types of fake interface screens on the victim's device:
- Card: A form requesting bank card details
- Custom: Forms designed to collect arbitrary information based on the attack scenario
- Photo: An upload interface that tricks users into submitting photos
- QR: A display showing QR codes with customizable text fields
- Text: Simple text messages that appear legitimate
These interfaces mimic the look and feel of genuine application screens. Users believe they're interacting with a legitimate app, but they're actually sending data directly to the attackers.
The QR code activity deserves special attention. It includes two configurable elements: a text field (which defaults to "Enter tracking number") and a path pointing to a QR code image. The screen also contains a confirmation button. When users click this button, the Trojan launches an activity showing a loading animation. The researchers didn't identify the exact purpose of this module, but it likely supports social engineering schemes. Attackers could use it to redirect victims to phishing sites or trick them into making payments.
Mass SMS Distribution
Third, DeliveryRAT can now send mass SMS messages to all contacts in the victim's phone. The process follows these steps:
- The Trojan collects the complete contact list
- It transmits this list to the attackers' server
- On command, it sends a malicious message to every unique number in the list
This feature lets attackers spread the malware through trusted contacts. Recipients receive messages from people they know, making them more likely to click malicious links or download infected files.
Original Capabilities Remain Intact
The first version of DeliveryRAT already included several powerful features. The updated version keeps all of these:
- Intercepting SMS messages and push notifications, then hiding them from users
- Executing arbitrary USSD requests (the codes that start with * and # on phones)
- Sending SMS messages without user knowledge
- Hiding or displaying the application icon as needed
These functions support the Trojan's primary goal: stealing data while avoiding detection.
Technical Infrastructure and Communication
DeliveryRAT uses two communication methods to maintain control and extract data. The malware establishes a WebSocket connection with its command server. This connection allows operators to send commands in real-time, giving them immediate control over infected devices.
For data exfiltration, the Trojan uses HTTP requests. This method transfers stolen information—SMS messages, contact lists, banking credentials, and other sensitive data—back to the attackers' infrastructure.
The malware ensures it survives device restarts through a boot event handler called BootReceiver. When the device powers on, this handler activates the Trojan automatically. DeliveryRAT also creates periodic tasks that maintain communication with its command-and-control infrastructure. These tasks check in regularly, ensuring the attackers can always reach compromised devices.
Disguises and Distribution Methods
Researchers discovered DeliveryRAT samples masquerading as numerous legitimate services. The list of impersonated applications includes:
- Delivery Club (food delivery)
- Ozon (online marketplace)
- Sberbank Online (banking)
- Postal tracking services
- Platforms for finding specialists and travel companions
- Classified advertisement sites
- Ticket booking services
The attackers also created samples imitating government service applications. In one particularly brazen case, they distributed a modified version of Telegram branded as "Oniongram," supposedly offering anonymity features.
The Loader Application Tactic
In some distribution campaigns, attackers used a loader application identified as com.harry.loader. This loader displays a fake update notification to victims. The message appears legitimate, prompting users to install what they believe is a necessary update. Instead, the loader installs DeliveryRAT from its own resources. This technique bypasses some security measures because the installation doesn't require downloading files from external sources.
My Analysis of This Threat
In my opinion, DeliveryRAT's evolution represents a troubling shift in mobile malware development. The combination of data theft, social engineering interfaces, and DDoS capabilities creates a multi-purpose threat. Attackers can monetize infections through stolen financial data while simultaneously using the same devices as weapons for disrupting services.
Per the F6 research, the Trojan remains under active development. Its operators continue expanding functionality beyond simple data theft. This progression indicates a professional operation with resources to maintain and improve their malware over time.
Practical Implications for Users and Organizations
The dynamic activity system poses particular risks. Users can't easily distinguish between legitimate app interfaces and the fake screens DeliveryRAT generates. The interfaces look authentic because they're displayed within what appears to be a trusted application.
The mass SMS distribution feature exploits trust relationships. When someone receives a message from a contact they know, they're more likely to act on it without scrutiny. This turns every infected device into a distribution point for spreading the malware further.
The DDoS capability adds another dimension to the threat. Organizations face potential attacks not just from traditional botnets, but from networks of compromised mobile devices. These attacks can target business services, competitors, or any entity the operators choose.
Detection and Prevention Steps
Protecting against DeliveryRAT requires several approaches:
- Download apps only from official stores: Google Play Store has security screening, though not perfect. Third-party app stores and direct APK downloads carry higher risks.
- Review app permissions carefully: Food delivery apps don't need permission to send SMS to all your contacts. Banking apps don't need to execute USSD codes. Question any permission that seems unrelated to the app's stated purpose.
- Watch for unusual behavior: Fake update notifications, unexpected interface screens requesting sensitive data, or apps asking for information they shouldn't need all indicate potential compromise.
- Keep devices updated: Android security patches address vulnerabilities that malware exploits. Enable automatic updates when possible.
- Use mobile security software: Reputable security apps can detect known malware signatures and suspicious behavior patterns.
- Monitor network activity: Unusual data usage or network connections might indicate malware communication with command servers.
For Organizations
Companies should implement mobile device management (MDM) solutions for employee devices accessing corporate resources. These systems can:
- Enforce security policies
- Detect and block malicious applications
- Monitor for signs of compromise
- Isolate infected devices from corporate networks
Organizations should also educate employees about mobile threats. Many people don't realize their phones face the same malware risks as their computers.
The Bigger Picture
DeliveryRAT's development shows how mobile malware continues maturing. Attackers invest time and resources into creating sophisticated tools that serve multiple purposes. A single infection now provides data theft opportunities, social engineering capabilities, and attack infrastructure.
Furthermore, the impersonation of government services and popular applications demonstrates the attackers' understanding of their targets. They choose disguises that people trust and use regularly, increasing the likelihood of successful infections.
The researchers' findings suggest we'll see continued evolution in DeliveryRAT's capabilities. Operators who actively develop and expand their malware typically have successful operations generating revenue. That success funds further development, creating a cycle that makes the threat more dangerous over time.
Mobile security can no longer be an afterthought. Devices that handle banking, communications, and sensitive personal data need the same security attention we give to desktop computers and servers. DeliveryRAT proves that mobile threats now match traditional malware in sophistication and potential impact.


