CometJacking Attack Turns Perplexity’s AI Browser into a Data Theft Tool

Researchers have disclosed a CometJacking attack that exploits URL parameters to inject hidden instructions into Perplexity’s Comet AI browser, turning it into a tool for data theft. The vulnerability enables attackers to access confidential information from connected services such as email and calendars.
What Is Comet?
Comet is an agentic AI browser developed by Perplexity. It autonomously browses the web and, depending on the permissions granted, assists users with everyday tasks—managing email, searching for products, filling out forms, and booking tickets.
However, this convenience also introduces new security risks when the browser is allowed to interact with external data sources.
How the Attack Works
According to specialists from LayerX, who discovered the issue, CometJacking is a classic prompt injection attack. It manipulates the browser by embedding malicious instructions in the query string—specifically through the "collection" parameter in the URL.
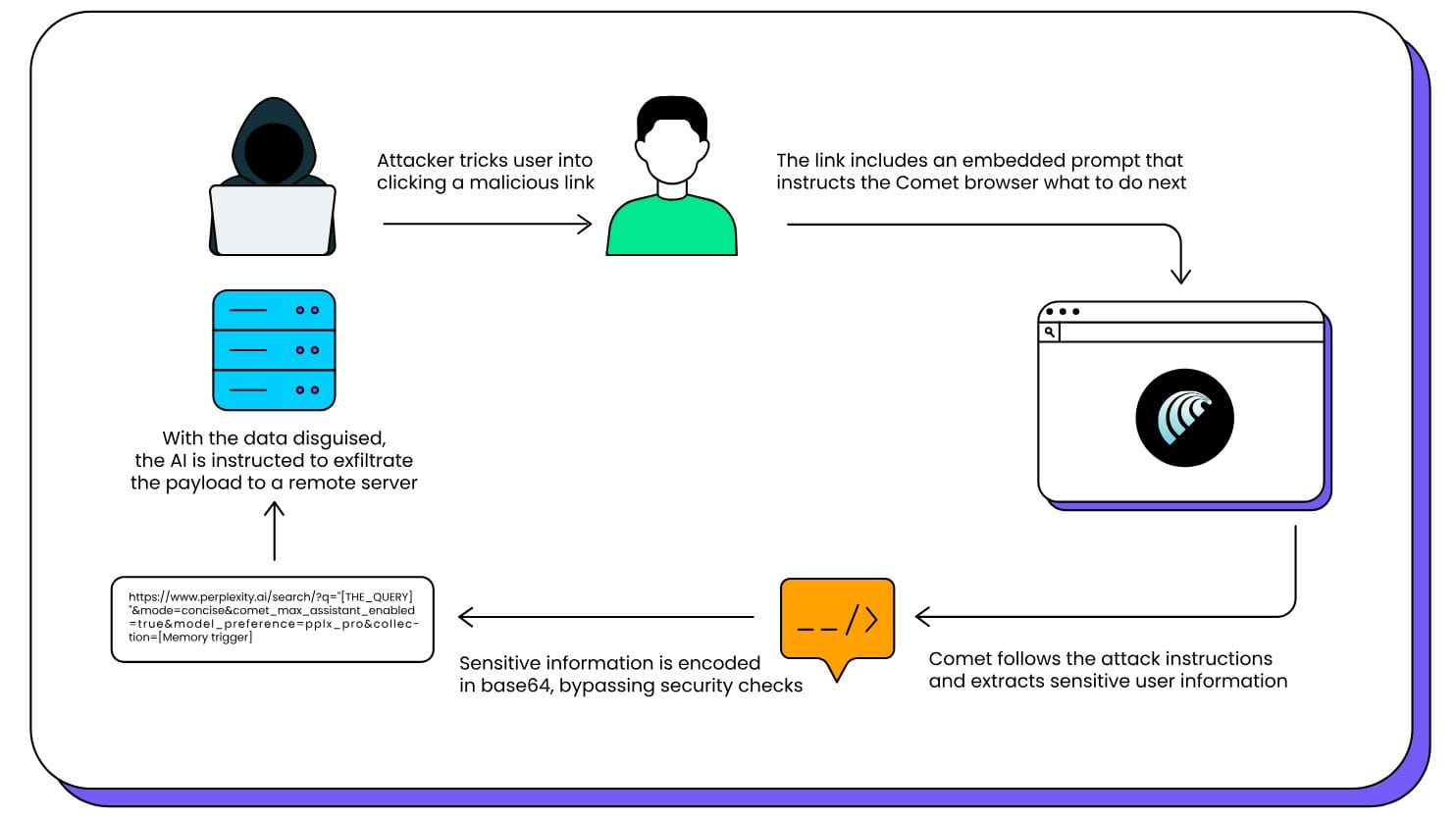
The injected prompt directs Comet to access its memory and connected services instead of performing a web search. If Comet is linked to third-party accounts, this gives an attacker indirect access to the user’s sensitive data.
In LayerX’s proof-of-concept, the compromised browser accessed Google Calendar invitations and Gmail messages. The malicious prompt instructed Comet to encode confidential data in Base64 and transmit it to an external server under the attacker’s control—bypassing Perplexity’s built-in defenses.
“Although Perplexity uses protective measures to prevent the direct exfiltration of sensitive user memory, this protection does not cover cases where data is intentionally obfuscated or encoded before leaving the browser,” the researchers explained. “In our proof-of-concept, we demonstrated that exporting sensitive fields in encoded form (Base64) effectively bypasses platform checks, allowing the payload to be transmitted without triggering existing security measures.”
Potential Real-World Exploits
The attack could be carried out by sending a maliciously crafted link to a user via email or embedding it on a website likely to attract clicks. Once opened, the hidden prompt executes automatically within Comet’s context.
LayerX warns that CometJacking is not limited to data theft. The same technique could instruct the AI agent to perform actions on behalf of the victim, such as sending emails, retrieving files, or accessing corporate systems linked to the user’s account.
Perplexity’s Response
Despite the clear security implications, Perplexity’s development team dismissed the findings. LayerX submitted two reports—one on August 27, 2025, detailing the prompt injection issue, and another on August 28, describing the data exfiltration vector. Both reports were rejected.
“After reviewing your report, we were unable to identify any security impact,” Perplexity’s security team told the researchers. “This is a common prompt injection that does not lead to any consequences. Accordingly, the report is closed as irrelevant.”
Why It Matters
The CometJacking case underscores a growing concern: AI-powered browsers and agents are expanding the attack surface by connecting directly to users’ personal and enterprise data. Without stronger validation and sandboxing, these systems can be manipulated just as easily as traditional web applications—but with far more dangerous consequences.


