Chrome Zero-Day Exploit Linked to Hacking Team's Dante Spyware in Russian Espionage Campaign

Kaspersky Lab researchers have documented the first real-world deployment of Dante, commercial spyware developed by Italian firm Memento Labs—the rebranded successor to the notorious Hacking Team. The discovery emerged from analysis of "Operation Forum Troll," a sophisticated cyber-espionage campaign targeting Russian organizations.
From Scandal to Rebranding: Hacking Team's Legacy
Founded in 2003, Hacking Team built its reputation selling "lawful intercept" spyware to government agencies worldwide. Its flagship product, Remote Control Systems (RCS), offered extensive surveillance capabilities including file exfiltration, communications interception, and remote control of webcams and microphones.
The company's fortunes changed dramatically in 2015 when hackers breached Hacking Team itself, leaking over 400 GB of data including RCS source code and internal documents. The breach forced the company to ask clients to suspend RCS operations.
InTheCyber Group acquired the struggling firm in 2019, rebranding it as Memento Labs. At the ISS World MEA 2023 conference for law enforcement and intelligence services, the company unveiled Dante, its next-generation spyware platform. Until now, no security researchers had encountered Dante in active operations.
Operation Forum Troll: Zero-Day Espionage
In March 2025, Kaspersky discovered a targeted campaign leveraging a zero-day vulnerability in Chrome (CVE-2025-2783). Attackers sent personalized phishing emails to employees at Russian media outlets, government agencies, educational institutions, and financial organizations, inviting them to participate in the "Primakov Readings" scientific forum.

Victims who clicked the malicious links were compromised simply by opening Chrome—no additional user interaction required. The campaign deployed LeetAgent, a distinctive spyware variant whose commands are written in leetspeak, an unusual choice for advanced persistent threat operations.
Tracing LeetAgent's infrastructure back to 2022, researchers identified additional attacks by the same threat actor targeting organizations and individuals across Russia and Belarus. Within this operational toolkit, they discovered an unknown malware sample that would prove to be Dante.

Identifying Dante: From Code Strings to Commercial Spyware
Attribution came from multiple technical indicators. Beyond finding the literal string "Dante" in the code, researchers identified references to version 2.0—matching Memento Labs' conference presentation. Comparative analysis revealed code similarities between Dante and other tools used in Operation Forum Troll, confirming shared development origins.
Technical Sophistication: Evasion by Design
Dante employs VMProtect packing to obfuscate control flow, conceal imported functions, and detect debugging environments. To thwart dynamic analysis, the malware uses hash-based API resolution, extracts system call numbers directly from function code, then constructs new system call functions to bypass standard hooking mechanisms.

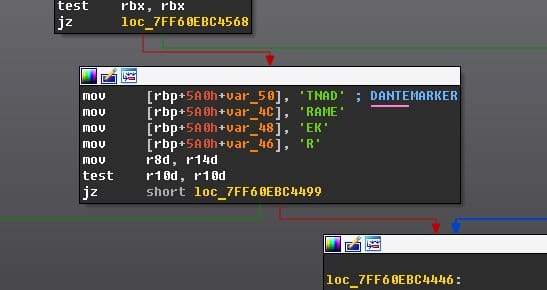
Beyond VMProtect's built-in protections, Dante implements multiple anti-analysis techniques:
- Monitors debug registers (Dr0–Dr7) via NtGetContextThread
- Checks the KdDebuggerEnabled field in KUSER_SHARED_DATA
- Queries ProcessDebugFlags, ProcessDebugPort, ProcessDebugObjectHandle, and ProcessTlsInformation through NtQueryInformationProcess
- Searches Windows event logs for indicators of analysis tools or virtual machines
- Detects sandbox environments by identifying suspicious libraries, measuring sleep() and cpuid execution times, and inspecting the file system
Once environment checks pass, Dante decrypts its configuration using XOR encryption and loads the orchestrator component from the resources section, where it masquerades as a font file. Updated orchestrators can also be loaded from the file system.
Architecture: Modular Design for Persistent Surveillance
The orchestrator—which Kaspersky analysts describe as commercially polished code—handles core functions including HTTPS-based command-and-control communications, module management, configuration updates, and self-protection mechanisms.
Modules can be stored on disk or loaded directly into memory. File paths for modules and registry-based configuration settings are derived from Base64-encoded infection identifiers (GUIDs), adding an additional obfuscation layer.
If Dante receives no commands within a configured timeframe, it automatically removes itself and all forensic traces—a fail-safe against long-term detection.
At publication time, Kaspersky had not recovered additional Dante modules, as no active infections existed within their user telemetry.

The Complexity of Attribution
"The creators of this spyware are well-known to cybersecurity experts. However, malicious programs can be difficult to identify and attribute to a specific group, especially in targeted attacks," said Boris Larin, Lead Security Expert at Kaspersky GReAT. "To determine Dante's origin, we had to unravel several layers of convoluted code, track clear signs of its use over several years, and correlate them with potential creators. It seems the malware's developers didn't choose the name 'Dante' for nothing, as anyone trying to understand its origin faces a difficult journey."
The reference appears deliberate—just as Dante's Inferno describes a descent through increasingly complex circles of hell, analyzing this spyware requires navigating progressively sophisticated layers of obfuscation.