Chinese-Linked Group PlushDaemon Exploits Software Updates in Supply Chain Attacks

A China-linked threat actor known as PlushDaemon is conducting cyber-espionage operations by intercepting software update traffic using malware dubbed EdgeStepper, according to researchers at ESET.
Campaign Overview
ESET reports that PlushDaemon has targeted individuals and organizations in the United States, China, Taiwan, Hong Kong, South Korea, and New Zealand since 2018, deploying custom malware including the SlowStepper backdoor.
Notable victims include electronics manufacturers, universities, and a factory belonging to an unnamed Japanese automaker located in Cambodia.
ESET telemetry data indicates the group has primarily relied on malicious software updates to breach target networks since 2019.
Attack Methodology
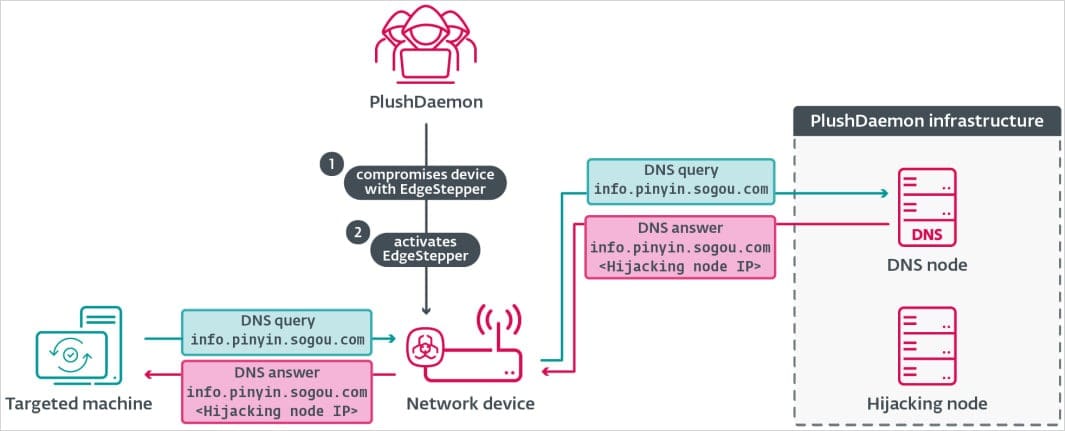
These attacks typically begin when threat actors compromise routers—either through known vulnerabilities or weak passwords—and deploy EdgeStepper malware onto the compromised devices, redirecting software update traffic to attacker-controlled infrastructure.
EdgeStepper, written in Go and compiled as an ELF binary, intercepts DNS queries and reroutes them to a malicious DNS node after verifying the requested domain is used for delivering software updates.
When victims attempt to update their software, they unknowingly download a first-stage malware loader called LittleDaemon, disguised as a legitimate DLL file named popup_4.2.0.2246.dll.
LittleDaemon communicates with the interception node and downloads a second-stage dropper called DaemonicLogistics, which is decrypted and executed entirely in memory. DaemonicLogistics then loads the main payload—the SlowStepper backdoor.
SlowStepper Capabilities
SlowStepper was previously used in attacks targeting users of South Korean VPN service IPany. In that incident, vendor compromise led victims to download a trojanized installer directly from the official website.
Once installed, the SlowStepper backdoor can collect detailed system information, perform file operations, execute arbitrary commands, and deploy Python-based spyware tools to steal browser data, log keystrokes, and harvest credentials.
Scope and Impact
ESET analysts observed PlushDaemon intercepting updates for Sogou Pinyin, a widely used Chinese input method, and detected attempts to intercept updates for other software products.
Researchers emphasize that PlushDaemon's adversary-in-the-middle capabilities are robust enough "to compromise targets anywhere in the world."