Chinese Hackers Exploit Unpatched Windows Vulnerability to Target European Diplomats

The China-linked hacker group UNC6384, also tracked as Mustang Panda, is conducting a widespread cyber-espionage campaign targeting European diplomatic and government organizations. Research from Arctic Wolf and StrikeReady reveals that the hackers are exploiting an unpatched Windows vulnerability related to LNK shortcuts—a flaw that has existed since at least 2017 and affects how Windows processes shortcut files.
Attacks occurred in Hungary, Belgium, Italy, the Netherlands, and Serbia during September and October 2025. The targeting of European diplomatic structures suggests intelligence collection objectives focused on foreign policy, defense procurement, and border control initiatives.
The Attack Method
The campaign begins with targeted phishing emails sent to specific individuals within diplomatic and government organizations. These emails contain URL links that download malicious LNK files when clicked. LNK files are Windows shortcuts—small files that point to programs, documents, or other resources on the system.
The email themes demonstrate careful research into legitimate diplomatic activities. Messages reference:
- NATO workshops on defense procurement
- European Commission meetings on simplifying border control procedures
- Other multilateral diplomatic events
These themes provide plausible reasons for recipients to open attached files or click links. A diplomatic official who recently attended or plans to attend a NATO workshop might naturally click a link promising related materials.
CVE-2025-9491: The Unpatched Vulnerability
The attacks exploit CVE-2025-9491, a vulnerability in how Windows processes LNK shortcut files. The flaw carries a CVSS score of 7.0, placing it in the "high severity" category but not quite reaching "critical" status.
The vulnerability arises from how Windows handles the COMMAND_LINE_ARGUMENTS structure within LNK files. Attackers can hide malicious command-line arguments using whitespace indentation in this structure. Windows processes these hidden commands without displaying them to users or triggering obvious warnings.
This technique allows arbitrary code execution on vulnerable devices without the user's knowledge. When someone opens what appears to be a harmless shortcut file, hidden commands execute in the background while Windows displays expected behavior to avoid raising suspicion.
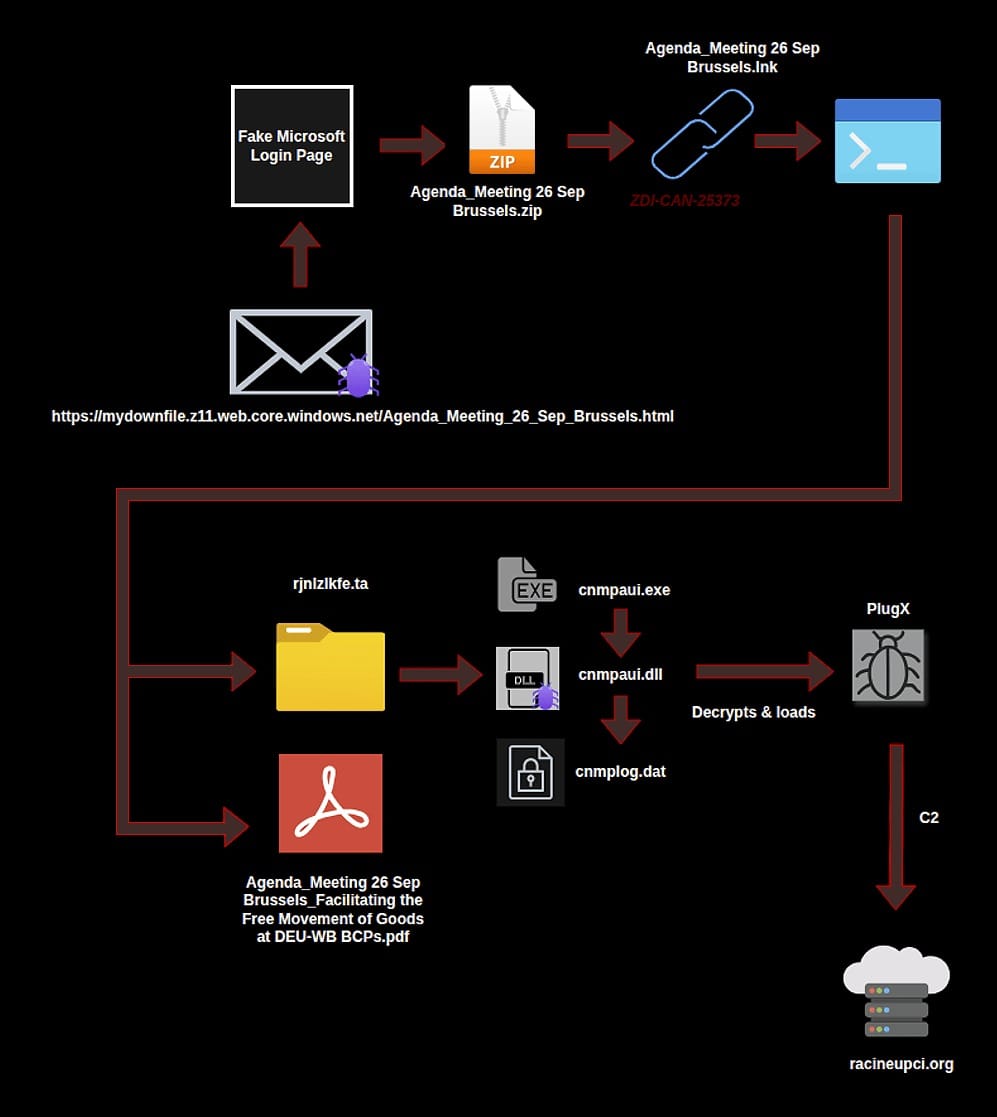
The Infection Chain
Once a victim opens the malicious LNK file, a carefully orchestrated infection sequence begins:
Step 1: PowerShell Execution
The hidden commands launch PowerShell, Microsoft's scripting environment. The PowerShell command performs two simultaneous actions:
- Decodes and extracts contents from a TAR archive (a compressed file format)
- Displays a decoy PDF document to the victim
The decoy PDF maintains the illusion that the victim opened a legitimate document. They see expected content—perhaps information about a NATO workshop or European Commission meeting—while malicious activity proceeds invisibly.
Step 2: DLL Side-Loading
The extracted TAR archive contains three components:
- Legitimate Canon printer utility: A genuine program from Canon that victims have no reason to suspect
- CanonStager DLL: A malicious library file designed to mimic a legitimate Canon component
- Encrypted PlugX payload (cnmplog.dat): The actual malware, encrypted to avoid detection
The attackers use a technique called DLL side-loading. When the legitimate Canon utility runs, it expects to load specific library files. The attackers place their malicious CanonStager DLL in a location where the Canon program will load it instead of the legitimate library. Since the Canon utility is legitimately signed, security software may not flag this activity as suspicious.
Step 3: PlugX Deployment
CanonStager decrypts and deploys the PlugX malware. PlugX, also known by aliases including Destroy RAT, Kaba, Korplug, SOGU, and TIGERPLUG, is a remote access trojan that provides extensive control over infected systems.
PlugX Capabilities
Once installed, PlugX provides attackers with comprehensive access:
Command Execution: Attackers can run any command on the infected system as if they were sitting at the keyboard. This includes launching programs, modifying files, or executing scripts.
Keystroke Capture: The malware records everything victims type, including passwords, confidential communications, and document content.
File Operations: Attackers can upload new files to the system or download existing files. This enables both data theft and deployment of additional tools.
Persistence Mechanisms: PlugX modifies Windows registry settings to ensure it automatically runs when the system starts. This persistence survives reboots and makes removal more difficult.
System Reconnaissance: The malware gathers detailed information about the infected system—installed software, network configuration, security products, user accounts, and system architecture.
Modular Architecture: PlugX's design allows operators to extend functionality through plugins. If attackers need capabilities beyond the base malware, they can load specialized modules for specific tasks without replacing the entire payload.
Anti-Analysis Features: The malware implements techniques to detect when it's being analyzed by security researchers or running in virtual machine environments. When it detects analysis attempts, it can alter behavior or cease operations to avoid revealing its capabilities.
Evolution of the Attack Toolkit
Arctic Wolf researchers documented changes in the attackers' tools over time. The CanonStager DLL artifacts have evolved significantly—from 700 KB in earlier versions to just 4 KB in recent samples. This size reduction of more than 99% indicates active development focused on minimizing digital footprints.
Smaller files provide several advantages for attackers:
- Faster downloads that reduce detection windows
- Lower likelihood of triggering size-based security alerts
- Easier to hide within legitimate network traffic
- Less storage space consumed on compromised systems
In early September 2025, the group added a new technique to their arsenal. They began using HTML Application (HTA) files to load JavaScript code. This JavaScript fetches payloads from a subdomain on cloudfront[.]net, Amazon's content delivery network. Using legitimate cloud infrastructure helps attacks blend with normal business traffic, since many organizations regularly access CloudFront for legitimate purposes.
The Vulnerability's Long History
The CVE-2025-9491 vulnerability has a troubling history. The flaw has existed since at least 2017—eight years before the current diplomatic targeting campaign. Public discussion of its exploitation began in March 2025, when Trend Micro analysts published research documenting widespread abuse.
Trend Micro's investigation revealed that eleven different "state-sponsored" hacker groups were actively exploiting the vulnerability, along with various cybercriminal organizations. The list of groups using this technique includes:
- Evil Corp: Russian cybercriminal group known for banking trojans and ransomware
- APT43 (Kimsuky): North Korean threat group focused on intelligence collection
- Bitter: South Asian threat group targeting government and defense sectors
- APT37: North Korean group conducting espionage operations
- Mustang Panda: Chinese threat group (the focus of this article)
- SideWinder: South Asian group targeting military and government organizations
- RedHotel: Chinese threat group focused on Southeast Asian targets
- Konni: North Korean group conducting campaigns against South Korean targets
This diverse list of threat actors from multiple countries demonstrates the vulnerability's value for espionage operations. When this many sophisticated groups adopt the same technique, it indicates a highly effective exploitation method.
Microsoft's Response—Or Lack Thereof
Despite the vulnerability's eight-year history and exploitation by at least eleven nation-state groups, Microsoft has not released a patch for CVE-2025-9491. This represents a significant failure in vulnerability management.
In March 2025, when Trend Micro published their research documenting widespread exploitation, Microsoft representatives stated they would "consider addressing the issue." However, the company noted that the vulnerability was not considered to require immediate intervention.
Microsoft's justification for not patching this flaw rests on two points:
- Defender Detection: Microsoft claims its Defender antivirus has detection capabilities to block exploitation attempts
- Smart App Control: This Windows security feature provides additional protection against malicious applications
In my opinion, this response is inadequate. Per industry best practices, vulnerabilities actively exploited by multiple nation-state threat groups should receive urgent attention and patches. Relying on antivirus detection rather than fixing the underlying flaw leaves users vulnerable to attacks that evade or disable security software.
Why Antivirus Detection Is Insufficient
Microsoft's argument that Defender can detect exploitation attempts has several problems:
Evasion Techniques: Sophisticated threat groups regularly develop methods to evade antivirus detection. The evolution of CanonStager from 700 KB to 4 KB demonstrates active development likely including detection evasion improvements.
Zero-Day Variants: Attackers can modify their exploitation techniques to create new variants that haven't yet been added to detection signatures.
Disabled Security Software: Many successful intrusions involve disabling security software early in the attack chain. Once disabled, Defender provides no protection.
Non-Windows Defender Users: Organizations using third-party security solutions instead of Microsoft Defender cannot benefit from whatever detection capabilities Microsoft has implemented.
Detection Lag: Even with good detection, there's typically a window between when an attack begins and when security software identifies and blocks it. During this window, malware can establish persistence or exfiltrate data.
Patches, by contrast, eliminate the vulnerability entirely. Once a system is patched, the specific exploitation technique no longer works, regardless of what security software is running or whether attackers develop new variants.
Recommended Protective Measures
Since Microsoft has not provided an official patch, Arctic Wolf specialists recommend several defensive measures for organizations concerned about this threat:
Restrict LNK File Usage
Organizations can block or restrict the use of LNK files within their Windows environments. This can be accomplished through:
- Group Policy settings that prevent LNK files from executing
- Email gateway filters that block messages containing LNK attachments
- Web proxy rules that prevent downloading LNK files from the internet
This approach has trade-offs. LNK files serve legitimate purposes in Windows environments, so blocking them entirely may affect normal operations. Organizations should test restrictions carefully to identify which workflows depend on LNK files.
Block Command-and-Control Infrastructure
The researchers identified specific command-and-control servers and domains used by the attackers. Organizations should block network connections to these identified threats. This prevents already-infected systems from receiving commands or exfiltrating data.
However, this approach only addresses known infrastructure. Attackers regularly establish new command-and-control servers. Blocking identified infrastructure helps but doesn't provide complete protection.
Enhanced Network Monitoring
Organizations should implement monitoring for suspicious activity patterns associated with these attacks:
- Unusual PowerShell execution, particularly spawned by unexpected processes
- TAR archive extractions in uncommon locations
- DLL side-loading behavior involving printer utilities or other unexpected programs
- Network connections to CloudFront subdomains from systems that don't normally access cloud services
- Registry modifications associated with persistence mechanisms
- Processes that exhibit anti-analysis behaviors
Security information and event management (SIEM) systems can correlate these indicators to identify potential compromises even when individual indicators might appear benign.
Additional Protective Layers
Beyond the researchers' specific recommendations, organizations can implement several additional controls:
Application Whitelisting: Allow only approved applications to execute. This prevents malicious executables from running even if they reach user systems.
PowerShell Logging and Restrictions: Enable comprehensive PowerShell logging to capture commands executed on systems. Configure PowerShell execution policies to require signed scripts.
Email Security: Deploy advanced email security solutions that analyze attachments and links for malicious behavior rather than relying solely on signature-based detection.
User Training: Educate diplomatic and government personnel about targeted phishing techniques. Train them to verify unexpected messages, especially those referencing diplomatic events, before clicking links or opening attachments.
Network Segmentation: Isolate systems handling sensitive diplomatic communications from general-purpose networks. This limits how far attackers can move laterally even if they compromise initial systems.
Endpoint Detection and Response: Deploy EDR solutions that monitor for suspicious behavior patterns rather than known malware signatures. EDR tools can identify the behavioral characteristics of PlugX even when the specific sample hasn't been seen before.
The Diplomatic Targeting Context
The targeting of European diplomatic structures fits Mustang Panda's established intelligence collection priorities. The group has historically focused on:
- Foreign policy decision-making processes
- Defense procurement and military capabilities
- International negotiations and diplomatic initiatives
- European Union policy development
- NATO operations and planning
The email themes used in this campaign—NATO defense procurement workshops and European Commission border control meetings—align with these intelligence priorities. China has clear interest in:
Defense Procurement: Understanding European defense acquisition plans helps China anticipate military capability developments and identify opportunities to influence procurement decisions or exploit supply chains.
Border Control: European Union border control policies affect Chinese citizens traveling to Europe, trade flows, and law enforcement cooperation. Intelligence on simplification efforts could inform Chinese diplomatic strategies.
NATO Activities: NATO represents the primary military alliance potentially opposing Chinese interests. Intelligence on NATO workshops and planning provides visibility into alliance priorities and capabilities.
European Commission Decisions: EU policy decisions affect Chinese economic interests, trade relationships, and diplomatic positioning. Early knowledge of policy discussions provides advantages in negotiations and strategic planning.
The Broader Threat Landscape
This campaign represents one piece of sustained Chinese intelligence collection targeting Western diplomatic and government organizations. Similar operations have targeted:
- U.S. State Department personnel
- European Union institutions
- Individual European national governments
- Think tanks and policy research organizations
- Defense contractors
- Academic institutions with government research contracts
The consistent exploitation of CVE-2025-9491 across multiple campaigns demonstrates that successful techniques persist until victims implement effective defenses or vendors patch underlying vulnerabilities. Microsoft's failure to patch this eight-year-old vulnerability actively used by eleven nation-state groups creates ongoing risk.
Implications for Affected Organizations
Diplomatic personnel and government organizations in the targeted countries should assume compromise attempts have occurred. Recommended actions include:
Incident Response Reviews: Examine logs and forensic data for indicators of compromise associated with this campaign. Look for the specific artifacts and behaviors researchers documented.
Credential Resets: Consider resetting credentials for users who may have been targeted, particularly those working on NATO defense procurement or European Commission border control initiatives.
Communication Security: Review what sensitive communications may have occurred on potentially compromised systems. Assess whether information discussed in emails, documents, or meetings requires damage control.
Counterintelligence Considerations: Evaluate what intelligence Chinese services may have gained through successful compromises. This assessment informs diplomatic strategies and negotiations.
Long-Term Security Improvements: Use this incident as motivation to implement more robust security controls that would prevent similar attacks in the future.
The Patch That Isn't Coming
Microsoft's decision not to patch CVE-2025-9491 leaves organizations in a difficult position. They face active exploitation by sophisticated threat groups but cannot deploy the most effective defense—a patch that eliminates the vulnerability.
This situation raises questions about Microsoft's vulnerability management priorities. When do vulnerabilities warrant immediate patching? How many nation-state groups must exploit a flaw before Microsoft considers it worthy of urgent attention? What criteria determine whether vulnerabilities require "immediate intervention"?
Eight years of exploitation by eleven nation-state groups apparently doesn't meet Microsoft's threshold. This decision places the burden of defense entirely on organizations and users rather than addressing the root cause in the operating system.
Looking Ahead
Mustang Panda and other groups exploiting CVE-2025-9491 will continue their campaigns as long as the vulnerability remains unpatched and organizations remain vulnerable. The evolution of the CanonStager artifacts and addition of new delivery techniques demonstrate active development of the attack toolkit.
Organizations cannot wait for Microsoft to patch this vulnerability. They must implement the defensive measures Arctic Wolf and other security researchers recommend. This includes restricting LNK file usage, blocking known malicious infrastructure, enhancing monitoring, and deploying multiple defensive layers that make exploitation more difficult even when the underlying vulnerability persists.
European diplomatic and government organizations face sustained targeting by sophisticated Chinese intelligence operations. This campaign represents one visible example of ongoing collection efforts. Defensive measures implemented in response to this specific threat will provide benefits against future campaigns using different techniques.
The lesson here extends beyond this particular vulnerability: organizations must defend themselves even when vendors fail to patch known flaws. Microsoft's decision leaves users vulnerable, so users must implement workarounds and compensating controls that mitigate the risk Microsoft declined to address.


