Chinese Hackers Exploit Critical React2Shell Bug Within Hours of Disclosure

Over 30 organizations confirmed compromised. More than 77,000 servers remain vulnerable.
Hours after security researchers disclosed the React2Shell vulnerability, malicious actors began exploiting the flaw in active attacks. Cybersecurity firms have confirmed breaches at more than 30 organizations across multiple sectors, while researchers estimate over 77,000 servers remain vulnerable.
The Vulnerability
React2Shell (CVE-2025-55182) represents a critical security flaw in React, Meta's widely-used JavaScript library. The vulnerability scored a perfect 10 out of 10 on the CVSS severity scale.
The flaw stems from unsafe data deserialization in React Server Components. Attackers can execute remote code on target servers using standard HTTP requests—no authentication or special privileges required.
Affected versions include React 19.0, 19.1.0, 19.1.1, and 19.2.0 in default configurations, plus the popular Next.js framework.
Patches are available in React versions 19.0.1, 19.1.2, and 19.2.1, along with corresponding Next.js releases.
Security experts warn that similar vulnerabilities may exist in other libraries with React Server implementations, including Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, and Waku.
Attack Activity Confirmed
Analysts from GreyNoise detected exploitation attempts from 181 unique IP addresses. Most attacks appear automated, with malicious traffic originating primarily from the Netherlands, China, the United States, Hong Kong, and other countries.
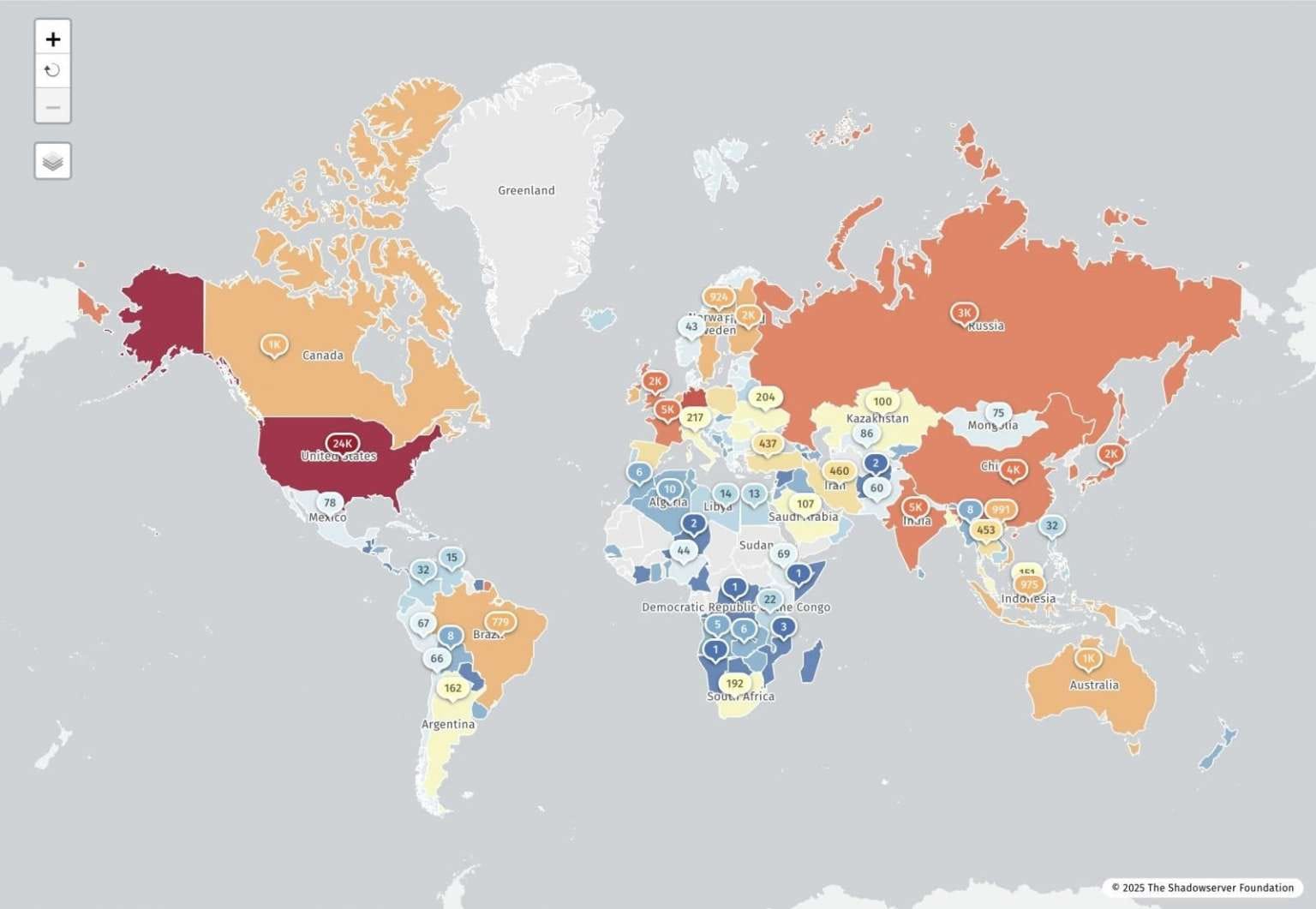
Shadowserver researchers identified 77,664 vulnerable IP addresses globally, including approximately 3,000 in Russia. They used a methodology from Searchlight Cyber and Assetnote that sends specific HTTP requests to servers and confirms vulnerabilities based on the response.
How Attackers Operate
Initial exploitation follows a predictable pattern. Attackers test the vulnerability by executing simple PowerShell commands, such as basic mathematical operations like powershell -c "40138*41979". These tests confirm remote code execution capability while producing predictable results and leaving minimal traces.
Once exploitation is confirmed, attackers escalate to base64-encoded PowerShell commands and load additional scripts directly into memory. GreyNoise researchers observed one attack loading a script from external server 23[.]235[.]188[.]3, which disabled Windows AMSI (Antimalware Scan Interface) to bypass protection systems before delivering the next payload stage.
Analysis via VirusTotal revealed the PowerShell script installs a Cobalt Strike beacon on target devices, establishing persistent attacker access to compromised networks.
Chinese APT Group Attribution
Amazon AWS cybersecurity analysts warned that React2Shell exploitation began within hours of public vulnerability disclosure. The attacks trace back to infrastructure previously associated with Chinese APT groups, including Earth Lamia and Jackpot Panda.
Attackers conduct reconnaissance on vulnerable servers using commands like whoami and id, attempt file writing operations, and read /etc/passwd for system information.
Palo Alto Networks attributes specific attack campaigns to UNC5174, a state-sponsored Chinese threat group (also tracked as CL-STA-1015). Researchers observed this group deploying two pieces of malware:
- Snowlight: A dropper that enables remote delivery of additional payloads to compromised devices
- Vshell: A backdoor frequently used by Chinese groups for remote access, post-exploitation, and lateral movement within compromised networks
Attackers execute commands, gather system information, and attempt to steal configuration files and AWS credentials from breached organizations.
Government Response
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2025-55182 to the Known Exploited Vulnerabilities (KEV) catalog. All federal agencies must apply patches no later than December 26, 2025.
The Cloudflare Connection
The global Cloudflare outage that occurred over the past weekend was also linked to React2Shell—specifically, to patching the critical vulnerability. Cloudflare developers explained the incident occurred while deploying emergency protective measures in the company's Web Application Firewall (WAF).
The incident affected approximately 28% of all HTTP traffic passing through Cloudflare. The company emphasized the outage was not related to a cyberattack.
Immediate Actions Required
Organizations using affected React and Next.js versions should:
- Apply patches immediately to React versions 19.0.1, 19.1.2, or 19.2.1
- Update Next.js to patched releases
- Audit systems for signs of compromise, particularly PowerShell activity and unusual network connections
- Review other React Server implementations for similar vulnerabilities
- Monitor systems for reconnaissance activity (
whoami,idcommands,/etc/passwdaccess attempts)
The speed of exploitation—moving from disclosure to confirmed breaches within hours—demonstrates how quickly threat actors capitalize on critical vulnerabilities. Organizations running React-based applications should treat this as a high-priority patching emergency.


