ChimeraWire Trojan Manipulates Search Rankings Through Browser Automation

Security researchers at Doctor Web discovered a trojan that mimics human browsing behavior to artificially inflate website traffic and manipulate search engine rankings. The malware, named ChimeraWire, targets Windows systems and represents a financially-motivated attack that monetizes infected machines through search engine optimization fraud.
ChimeraWire builds on open-source projects zlsgo and Rod, legitimate browser automation frameworks typically used for web application testing and development. The malware repurposes these tools to control browsers on infected systems, executing scripted browsing patterns that appear organic to tracking systems.
How Browser Automation Becomes Weaponized
Traditional click fraud bots generate obviously artificial traffic—identical timing patterns, unrealistic mouse movements, and behavior that analytics systems easily flag as non-human. ChimeraWire attempts to bypass these detection methods by using actual browser instances and introducing randomization that mimics human behavior variability.
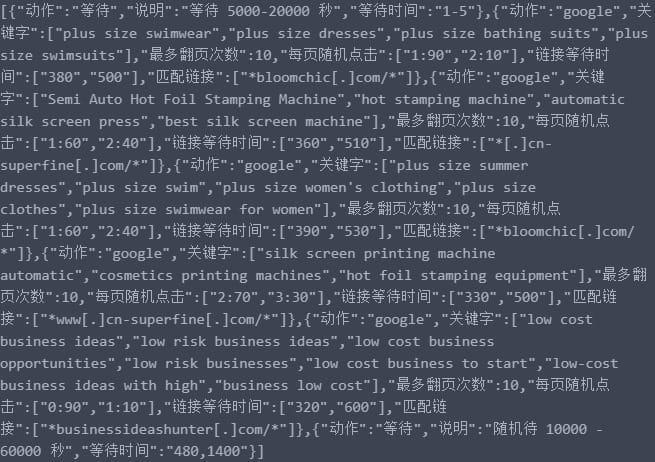
The trojan opens real browser sessions, navigates to target websites, scrolls through pages, clicks links, and generates engagement metrics that search engines interpret as genuine user interest. This manufactured engagement can influence search rankings, particularly for sites competing in lower-traffic niches where smaller traffic volumes significantly impact positioning.
The Business Model Behind Traffic Manipulation
Someone profits from ChimeraWire infections, though Doctor Web's report doesn't specify the exact monetization mechanism. Several business models could apply:
Black-hat SEO services sell artificial traffic and engagement to clients wanting improved search rankings. These services operate in gray markets, promising results through methods that violate search engine terms of service. ChimeraWire-infected machines become involuntary participants in these manipulation campaigns.
Alternatively, attackers could target their own websites, using compromised machines to boost their own search visibility for affiliate marketing, advertising revenue, or lead generation businesses that profit from increased organic traffic.
A third possibility involves selling the botnet's traffic generation capacity to multiple clients, rotating infected machines through different campaigns to maximize revenue from the compromised infrastructure.
Technical Implementation
ChimeraWire's use of zlsgo and Rod indicates relatively sophisticated implementation. These frameworks provide robust browser control capabilities, handling complex interactions that simple HTTP request bots cannot replicate. The malware essentially weaponizes quality assurance tools designed for legitimate web testing.
Rod specifically offers Chrome DevTools Protocol integration, allowing programmatic control of Chrome browsers with capabilities matching those available to human users. This includes JavaScript execution, cookie handling, and interaction with dynamic page elements—all necessary for convincing traffic simulation.
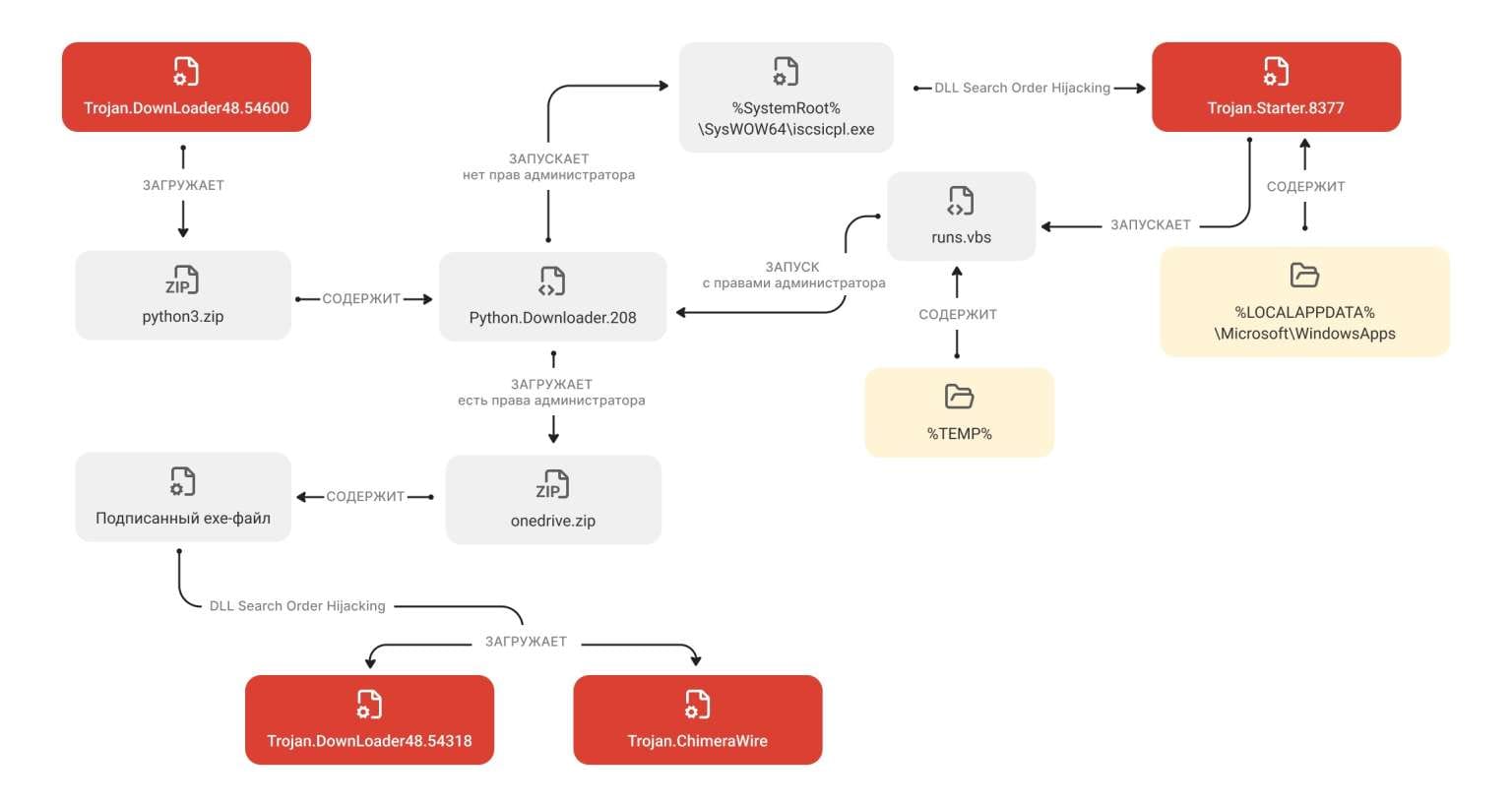
Doctor Web hasn't disclosed ChimeraWire's distribution method. Typical trojan delivery mechanisms include malicious email attachments, compromised software downloads, exploit kits targeting browser vulnerabilities, or bundling with pirated software. Without distribution details, the infection scale and target demographics remain unclear.
Search Engine Implications
Search engines invest heavily in distinguishing genuine user engagement from artificial manipulation. Algorithms consider factors like traffic sources, user behavior patterns, engagement duration, and bounce rates when determining content quality and ranking.
ChimeraWire represents an evolution in manipulation tactics. Rather than generating obviously fake traffic through server requests, it creates browser-based activity that more closely resembles real users. This challenges detection systems that rely on identifying non-browser traffic or bot-like behavioral patterns.
However, search engines maintain sophisticated fraud detection capabilities. Google, Bing, and other platforms analyze vast datasets to identify manipulation attempts. Even sophisticated bots typically reveal patterns when examined at scale—identical browsing sequences, timing correlations across infected machines, or traffic sources concentrated in botnets.
The arms race continues. Attackers develop more convincing simulation methods while search engines refine detection algorithms. ChimeraWire represents one iteration in this ongoing competition.
In My Opinion
ChimeraWire illustrates how legitimate automation tools become attack vectors when repurposed for malicious use. The frameworks it exploits—zlsgo and Rod—serve valuable purposes in web development and testing. Yet their capabilities make them attractive building blocks for fraud infrastructure.
Per the research findings from Doctor Web, the malware specifically targets Windows systems, suggesting the attackers prioritized the largest desktop operating system installed base. This maximizes potential botnet size and therefore traffic generation capacity.
The click fraud and SEO manipulation market creates financial incentives that drive trojan development like ChimeraWire. As long as artificially inflated search rankings generate monetary returns—through advertising revenue, lead generation, or direct sales—attackers will continue developing methods to create convincing fake engagement.
For website owners, this creates a problematic dynamic. Legitimate sites compete against others potentially using artificial traffic to gain ranking advantages. Search engines attempt to level the playing field through fraud detection, but sophisticated manipulation tools like ChimeraWire make detection harder.
Organizations should approach sudden traffic increases or unexpected search ranking improvements with skepticism. While organic growth occurs, dramatic changes might indicate competitors using artificial manipulation. More concerning, if your own systems become infected with trojans like ChimeraWire, your infrastructure could be generating fraudulent traffic to other sites without your knowledge.
The broader challenge involves distinguishing automation-assisted legitimate activity from malicious automation. Browser automation tools serve essential purposes—accessibility technologies, productivity tools, and development workflows all depend on programmatic browser control. ChimeraWire exploits these same capabilities for fraud, making blanket restrictions on browser automation impractical.
Search engines must continuously adapt ranking algorithms to identify and discount artificial engagement while preserving the value of genuine user signals. Website owners need to protect systems from trojan infections that turn machines into unwitting participants in fraud networks. Users should recognize that malware infections increasingly serve purposes beyond data theft—compromised systems become resources in various monetization schemes.
ChimeraWire represents a specific implementation, but the underlying approach—using real browsers controlled by automation frameworks to simulate human behavior—will likely appear in future malware variants regardless of what happens to this particular trojan family.


