ChaosBot Uses Discord Channels to Control Infected Computers
Cybersecurity specialists at eSentire have discovered a new backdoor called ChaosBot, written in Rust, that allows attackers to conduct reconnaissance and execute arbitrary commands on compromised systems. The malware is notable for using Discord as its command-and-control (C2) channel.
Researchers first detected ChaosBot in late September 2025 during an incident response at a client in the financial sector.
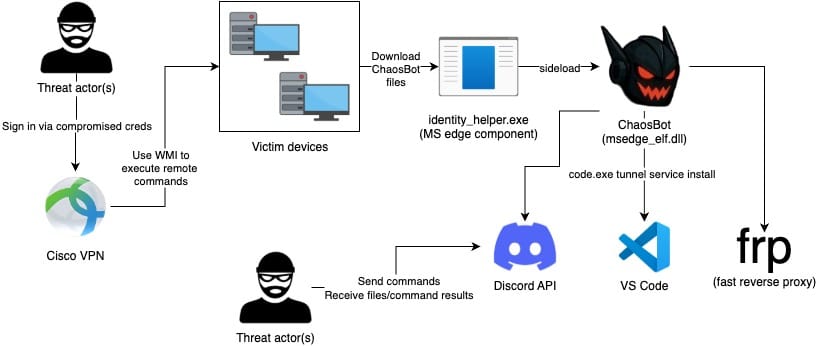
“The attackers used stolen credentials that worked for both Cisco VPN and a privileged Active Directory account named ‘serviceaccount,’” eSentire explained. “Using the compromised account, they leveraged Windows Management Instrumentation (WMI) to execute remote commands across the network, facilitating ChaosBot’s deployment and execution.”
How ChaosBot Spreads
The name ChaosBot comes from a Discord profile used by a threat actor under the handle chaos_00019, which sends remote commands to infected hosts. A second account linked to the malware is lovebb0024.
The backdoor is delivered via phishing emails containing a malicious Windows shortcut (LNK). When opened, the LNK executes a PowerShell script that downloads and runs ChaosBot while showing a fake PDF document to distract the user — in this case, a spoofed letter from the State Bank of Vietnam.
The payload is a malicious DLL (msedge_elf.dll) loaded through the Microsoft Edge executable (identity_helper.exe). After installation, ChaosBot collects system information and deploys a Fast Reverse Proxy (FRP), creating a reverse connection to maintain persistent access.
Command and Control via Discord
ChaosBot communicates through a Discord channel named after the infected device. From there, its operators issue commands such as:
shell— execute PowerShell commands;scr— capture screenshots;download— retrieve files from the victim’s system;upload— exfiltrate files to the Discord channel.
Researchers also observed attempts to install Visual Studio Code Tunnel as an additional backdoor for remote command execution, though these efforts were unsuccessful.
Evasion and Anti-Analysis Techniques
New ChaosBot variants employ anti-detection methods to evade Event Tracing for Windows (ETW) and identify virtualized environments.
- The first method patches the beginning of ntdll!EtwEventWrite (replacing its instructions with
xor eax, eax; ret) to disable event logging. - The second checks MAC address prefixes against known VMware and VirtualBox identifiers; if a match is found, the malware terminates execution.
These techniques help ChaosBot operate stealthily on real systems while avoiding analysis in virtual sandboxes.
Why It Matters
By embedding its command infrastructure inside Discord, ChaosBot leverages a trusted, encrypted platform to mask malicious activity and evade network defenses.
The use of Rust — a secure and efficient language — further complicates detection and analysis, reflecting a broader trend of threat actors adopting modern development stacks and legitimate cloud services for command and control.


