Chainalysis: In 2025, Hackers Stole $3.41 Billion in Cryptocurrency

Blockchain analysts from Chainalysis released their annual report showing that malicious actors stole $3.41 billion in cryptocurrency over the past year. North Korean hackers accounted for more than $2.02 billion of that total, with nearly $1.5 billion coming from a single attack on the Bybit cryptocurrency exchange.
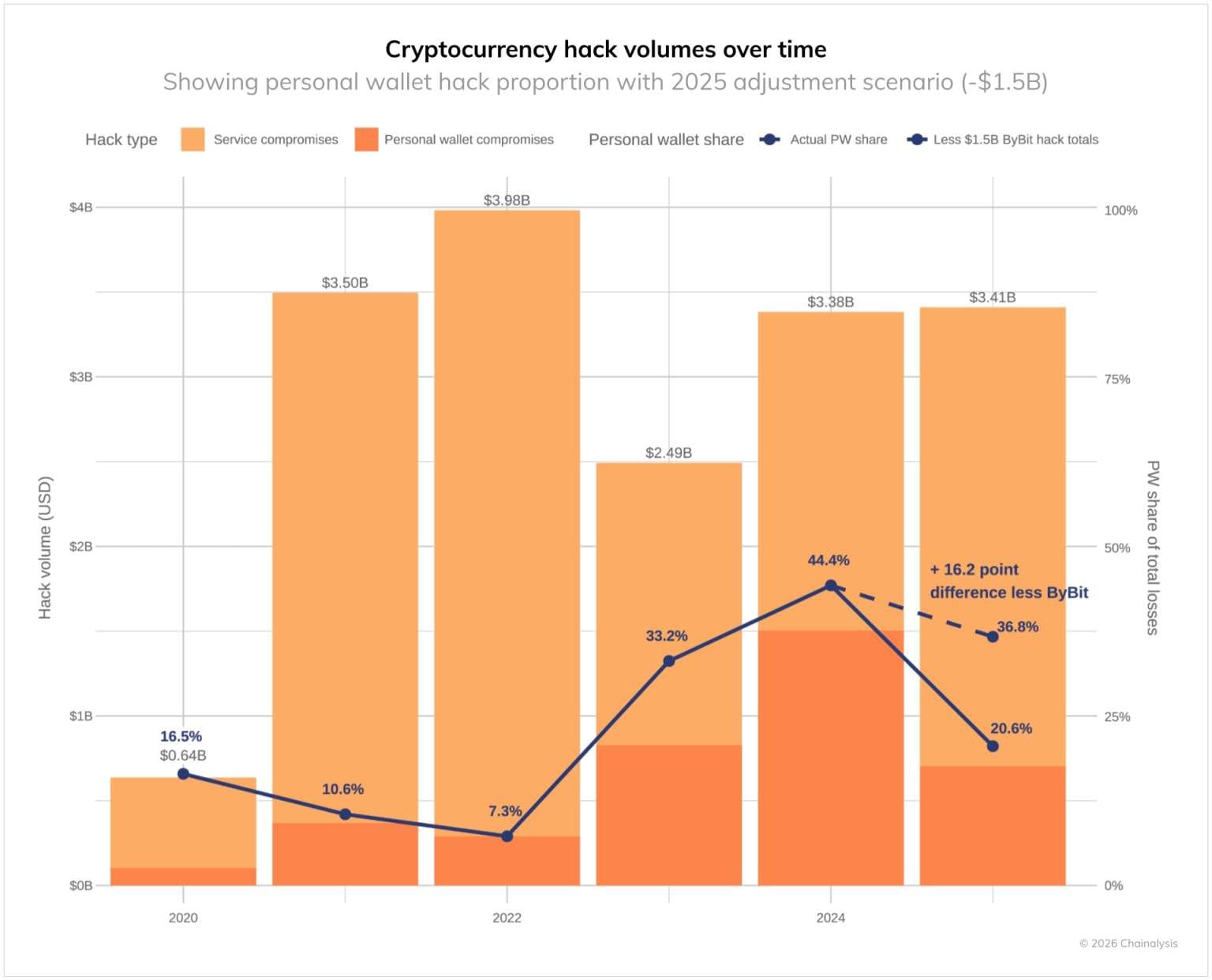
Per Chainalysis, the $2.02 billion figure represents only a lower-bound estimate. This marks a 51% increase from last year's theft of $1.3 billion by DPRK criminals. Over the past five years, North Korean hackers have stolen at least $6.75 billion in cryptocurrency.
The February hack and robbery of Bybit represents more than half of this year's stolen funds. Security researchers linked this attack to TraderTraitor (also known as Jade Sleet and Slow Pisces), a hacker group affiliated with Lazarus. The Bybit incident stands as the largest cryptocurrency robbery in history.
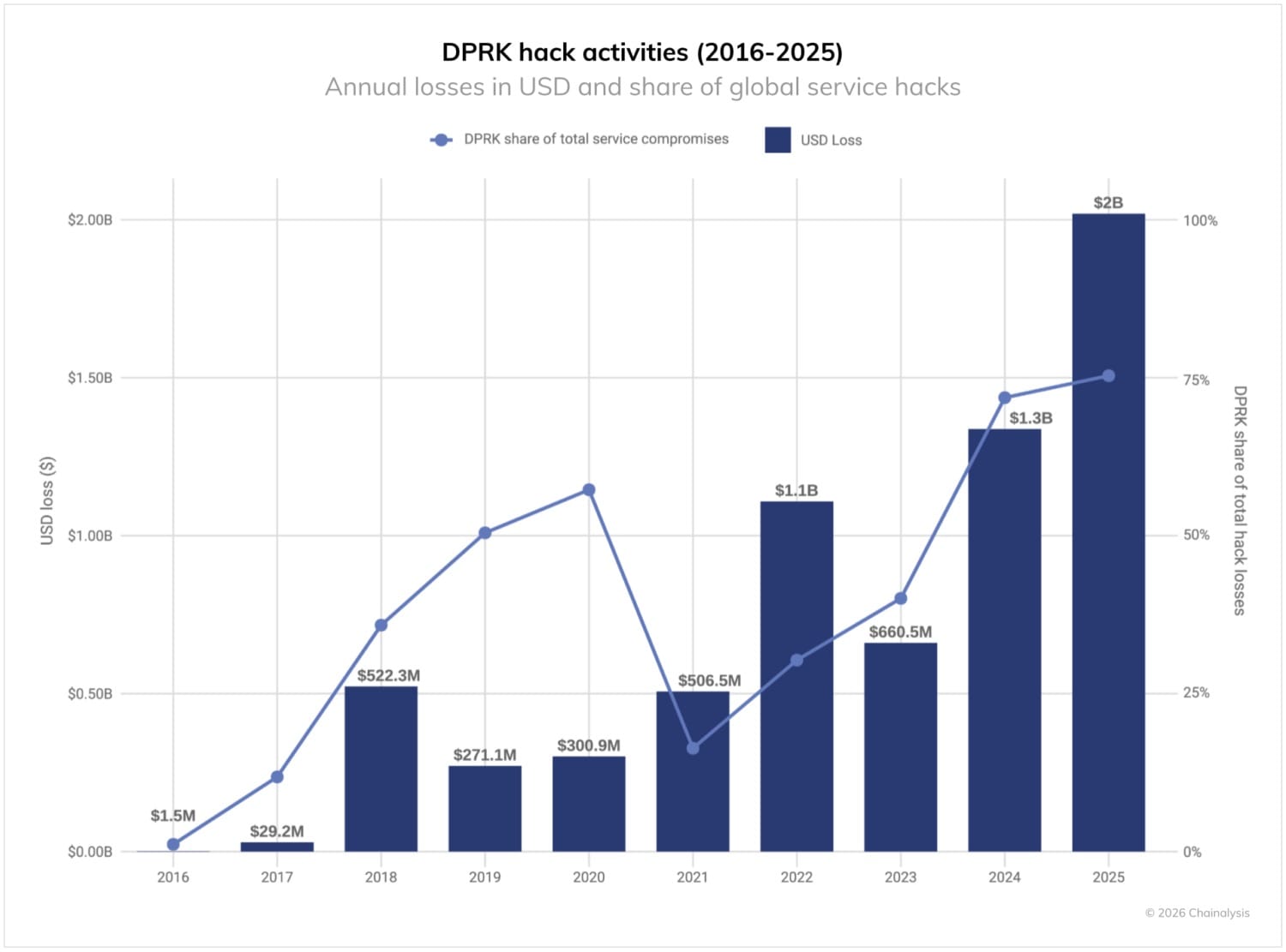
North Korean Attack Methods
Chainalysis experts identified several tactics North Korean hackers use to compromise cryptocurrency platforms.
The first approach, known as "Dream Job," targets individuals through LinkedIn or WhatsApp. Attackers pose as recruiters offering positions at major companies in defense, chemical, aerospace, or technology sectors. When victims respond, hackers convince them to install malware—including BURNBOOK, MISTPEN, or BADCALL—disguised as employment test assignments.
This campaign serves two purposes: stealing confidential data and generating revenue while evading international sanctions.
The second tactic involves infiltrating companies with North Korean IT specialists. These developers obtain positions at companies worldwide, including cryptocurrency exchanges, using forged documents and operating through front companies such as DredSoftLabs and Metamint Studio. Once hired, they gain access to critical systems. Security researchers have code-named this method "Wagemole."
"The increase in thefts in 2025 is likely linked to the expansion of the practice of infiltrating IT workers into exchanges, crypto companies, and Web3 projects," the Chainalysis report states. "This allows hackers to penetrate systems faster and gain privileged access before committing large-scale theft."
The Laundering Process
After stealing funds, DPRK hackers begin the laundering process. Researchers found they primarily operate through Chinese money transfer services, while also using cross-chain bridges, cryptocurrency mixers, and specialized platforms like Huione.
Stolen cryptocurrency typically undergoes a three-stage laundering process lasting approximately 45 days:
Stage 1: Initial Laundering (0-5 days) – Hackers rapidly move funds away from the theft source using DeFi protocols and mixers.
Stage 2: Initial Integration (6-10 days) – Stolen assets transfer to cryptocurrency exchanges, secondary mixers, and cross-chain bridges like XMRt.
Stage 3: Final Integration (20-45 days) – Final conversion into fiat currency or other assets occurs through exchange services.
"The active use of Chinese money laundering services and OTC traders indicates that North Korean groups are deeply integrated with criminal networks in the Asia-Pacific region," Chainalysis notes.