CAPI Backdoor Targets Russian Automotive and E-Commerce Sectors

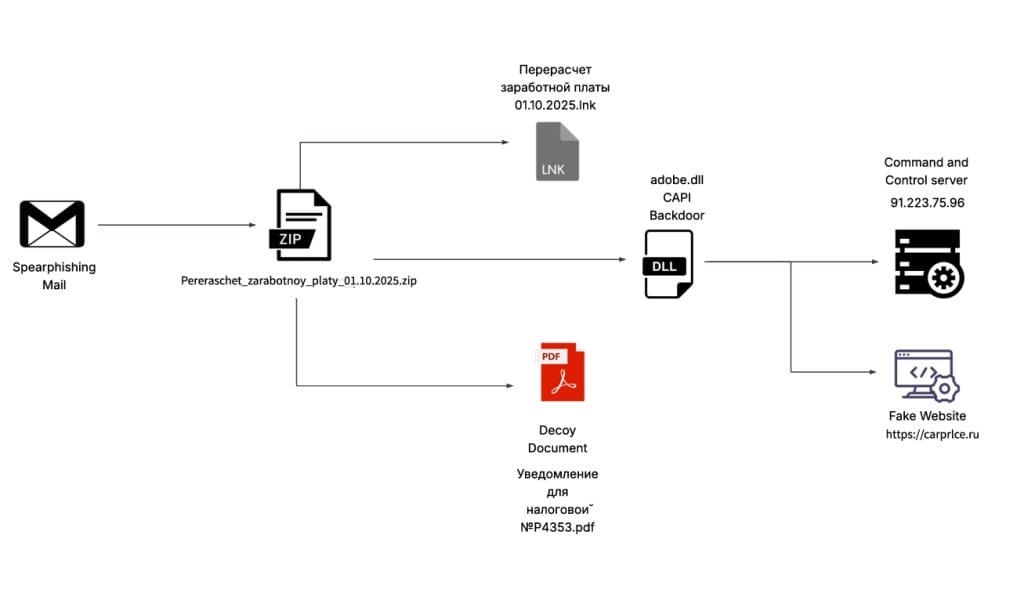
Researchers from Seqrite Labs have uncovered a new malicious campaign believed to target the Russian automotive industry and e-commerce platforms. The attackers are deploying a previously unknown .NET-based backdoor named CAPI to conduct data theft and system reconnaissance.
Infection Vector: Phishing with a Tax-Themed Decoy
According to the researchers, the attack begins with phishing emails carrying a malicious ZIP archive, one of which was uploaded to VirusTotal on October 3, 2025.
The archive contains two files:
- A decoy document in Russian, posing as a notification about personal income tax (NDFL) changes.
- A Windows shortcut (LNK) file, designed to launch the main payload.
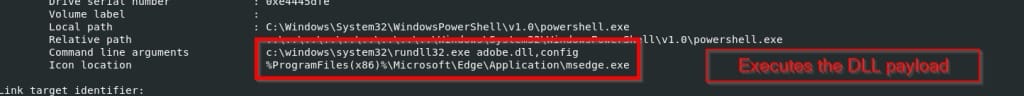
The LNK file—named “Pereraschot zarabotnoy platy 01.10.2025” (“Salary Recalculation 01.10.2025”)—executes the adobe.dll implant using rundll32.exe, a legitimate Windows utility. This execution chain leverages the Living-off-the-Land (LotL) technique to blend malicious activity with trusted system processes.
Payload Behavior and Capabilities
Once executed, CAPI performs several checks to determine whether it has administrator privileges and to enumerate antivirus software on the host.
To distract the victim, the malware opens the decoy document while quietly contacting its command-and-control (C&C) server at 91.223.75[.]96.
After establishing a connection, the backdoor can:
- Steal data from browsers such as Google Chrome, Microsoft Edge, and Mozilla Firefox
- Capture screenshots
- Collect system and directory information
- Send exfiltrated data back to the attacker’s infrastructure
Seqrite notes that the payload is a .NET DLL that functions both as a stealer and a persistent implant for future malicious operations.
Persistence and Anti-Analysis Techniques
To ensure persistence, CAPI employs two methods:
- Creating a scheduled task for periodic execution
- Adding an LNK file to the Windows Startup folder, pointing to a copy of the backdoor stored in the Roaming directory
The malware also performs extensive anti-virtualization checks to avoid running in sandboxed or research environments.
Attribution and Targeting
While the exact identity of the threat actor remains unknown, Seqrite analysts suggest a Russia-focused targeting pattern. One of the domains linked to the campaign, carprlce[.]ru, mimics the legitimate automotive platform carprice[.]ru, hinting at spear-phishing or credential theft operations aimed at the automotive sector.
In summary:
The discovery of CAPI adds to a growing list of region-specific backdoors built on the .NET framework and deployed through phishing campaigns. Its use of LotL execution, multi-layer persistence, and careful domain impersonation underscores how even localized threat actors are adopting advanced tradecraft once reserved for global cybercrime groups.


