BlueNoroff Leverages AI to Target Blockchain Executives in Sophisticated Social Engineering Campaigns

North Korean-linked threat actors are deploying artificial intelligence to enhance cryptocurrency theft operations, using deepfake video calls and AI-generated phishing content to compromise blockchain industry leaders, according to new research from Kaspersky Lab.
Kaspersky's Global Research and Analysis Team (GReAT) has identified two interconnected campaigns—GhostCall and GhostHire—active since April 2025. These operations target cryptocurrency exchanges, Web3 platforms, DeFi services, and blockchain development firms across India, Turkey, Australia, and throughout Europe and Asia.
The BlueNoroff Connection
BlueNoroff, a financially motivated subgroup within North Korea's notorious Lazarus hacking collective, has been expanding its SnatchCrypto campaign to exploit organizations handling cryptocurrencies, smart contracts, and fintech infrastructure. The group's latest operations introduce sophisticated social engineering techniques and specialized malware designed to compromise both blockchain developers and C-suite executives.
GhostCall: Weaponizing Virtual Meetings
The GhostCall campaign represents a particularly brazen evolution in social engineering tactics, targeting macOS users through elaborately staged deception.
Attack Methodology:
Attackers initiate contact via Telegram, masquerading as venture capitalists or angel investors. In some instances, they operate from compromised accounts belonging to legitimate entrepreneurs and startup founders, lending credibility to their approaches.
Victims receive invitations to investment meetings hosted on convincing phishing sites that replicate Zoom or Microsoft Teams interfaces. During these fake video conferences, targets are prompted to download what appears to be a client update to resolve a fabricated audio problem. This "update" is actually a malicious script that infects the device.
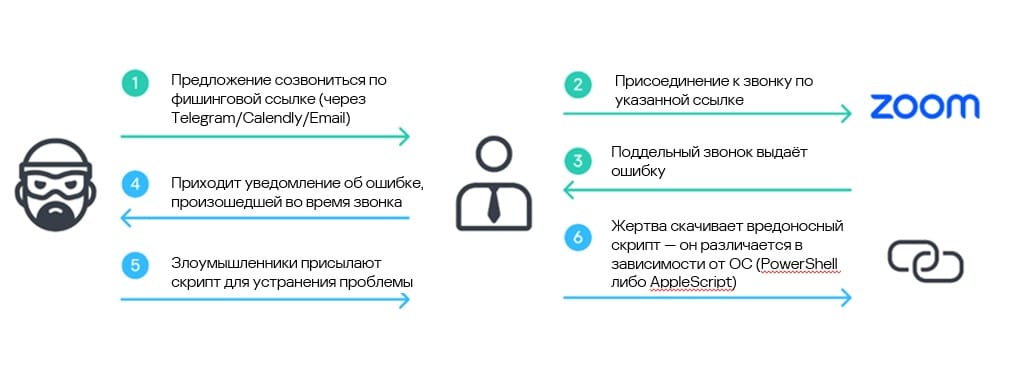
"The campaign was built on carefully planned deception," explains Sojun Ryu, senior security researcher at Kaspersky GReAT. "The attackers played videos recorded with the participation of previous victims during the staged meetings to make them resemble real calls. In this way, they manipulated new potential victims."
This approach represents a disturbing supply chain attack vector. Data harvested from initial victims—including video footage—is weaponized to compromise subsequent targets. The attackers exploit established trust relationships within the blockchain community to expand their reach across interconnected organizations and professional networks.
GhostCall deploys malware through seven distinct multi-stage infection chains, four of which were previously undocumented. The payloads include cryptocurrency stealers, credential harvesters targeting browsers and Telegram, and tools for exfiltrating confidential data.
GhostHire: Fake Recruiters Target Developers
The GhostHire campaign takes a different approach, focusing on blockchain developers through fraudulent recruitment.
Attackers pose as technical recruiters or hiring managers, presenting victims with what appears to be a skills assessment test. Candidates are instructed to download and execute a code repository from GitHub that contains concealed malware.
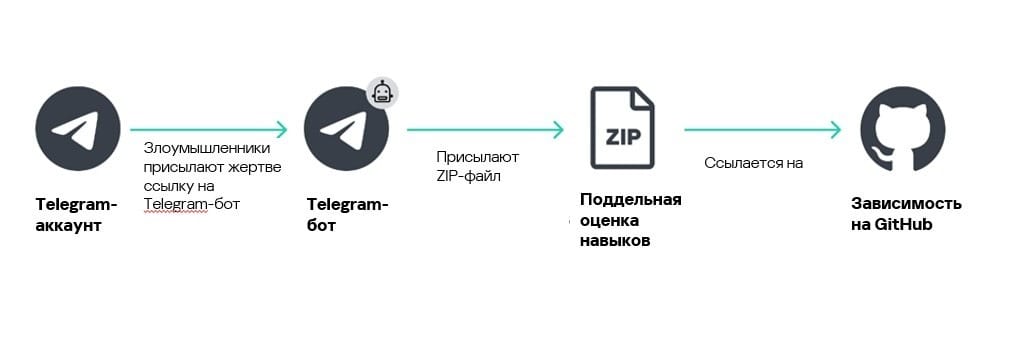
While GhostHire and GhostCall share backend infrastructure and toolsets, the former substitutes video calls with fake job postings distributed through Telegram bots. When developers interact with these bots—linked within the job advertisements—they receive either a malicious ZIP archive or a GitHub repository link.
The attackers employ urgency tactics, artificially pressuring developers to complete the "assessment" quickly, reducing the time available for scrutiny. Once the victim executes the downloaded files, their device becomes compromised.
AI-Enhanced Attack Development
What distinguishes these campaigns from previous BlueNoroff operations is the integration of generative AI throughout the attack lifecycle.
Kaspersky researchers report that AI tools are accelerating BlueNoroff's malware development cycle and enabling rapid refinement of attack techniques. The group has incorporated new programming languages into their arsenal and added layers of functionality that complicate detection and forensic analysis.
"Unlike previous campaigns, this time the attackers are not just stealing cryptocurrency and browser credentials," notes Omar Amin, senior security researcher at Kaspersky GReAT. "Generative AI gives the attackers the ability to obtain and analyze the necessary information faster, resulting in more precise targeting and an expanded attack scale."
This AI-augmented approach allows BlueNoroff to:
- Generate more convincing phishing content and communications
- Analyze victim profiles for personalized social engineering
- Develop malware variants more rapidly
- Scale operations across multiple geographies simultaneously
- Create deepfake video content for staged meetings
Implications for the Blockchain Industry
These campaigns underscore the escalating threat landscape facing cryptocurrency and blockchain organizations. The combination of nation-state resources, financial motivation, and cutting-edge AI capabilities creates an adversary with significant operational advantages.
Security experts recommend that blockchain industry professionals:
- Verify identities through multiple channels before accepting meeting invitations or job opportunities
- Scrutinize unsolicited investment or recruitment offers, especially those creating artificial urgency
- Avoid downloading files or repositories from unverified sources during assessments or meetings
- Implement endpoint detection and response (EDR) solutions on all devices
- Establish clear protocols for verifying the authenticity of business contacts
- Exercise caution with software updates prompted during video calls
"We hope our research will help prevent further damage," Amin concluded, emphasizing the importance of industry awareness in countering these evolving threats.
As AI tools become more accessible to threat actors, the blockchain and cryptocurrency sectors must anticipate increasingly sophisticated social engineering campaigns that blur the line between legitimate business interactions and malicious operations.


