Austrian Researchers Collected Personal Data of 3.5 Billion WhatsApp Users

Researchers from the University of Vienna announced that they discovered a vulnerability in WhatsApp that allowed them to collect data on more than 3.5 billion users. In their assessment, this could represent the largest data leak in history.
Exploitation Methodology
The report's authors note that WhatsApp allows users to be searched by phone number, a feature that has existed for many years. The researchers exploited this feature for large-scale data scraping: using a tool based on the Google libphonenumber library, they generated 63 billion phone numbers and checked them at a rate of 7,000 per second.
To the researchers' surprise, WhatsApp did not block their IP addresses and accounts, nor did it apply effective rate limiting. As a result, the team collected data at a rate exceeding 100 million accounts per hour, ultimately confirming the existence of 3.5 billion registered numbers—substantially more than the officially stated 2 billion WhatsApp users.
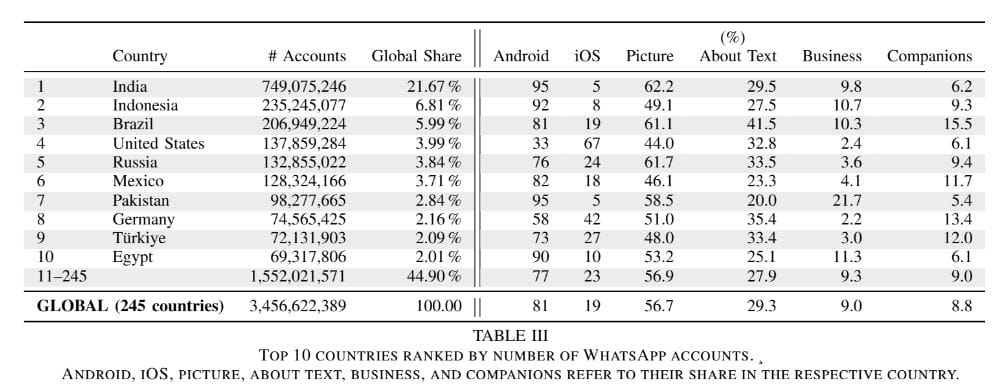
Data Exposure
Over 57% of the collected accounts had a profile photo, with two-thirds containing recognizable faces. Another 29% had text in their profile, sometimes containing sensitive information about sexual orientation and political views, links to LinkedIn and Tinder, work email addresses, and similar details.
The researchers managed to link some phone numbers to government officials and representatives of military departments.
Regional Security Implications
WhatsApp is banned in China, Myanmar, North Korea, and several other countries. Nevertheless, the researchers discovered millions of active accounts linked to numbers from these regions. In some of these countries, bypassing blocks can lead to arrest and punishment. Furthermore, databases of active numbers provide ready-made targeting lists for spammers, phishers, and robocall operators.
Disclosure Timeline and Response
The researchers reported the problem to Meta developers through the bug bounty program, but received a response only a year later—after the team sent Meta a preprint of their article and notified the company of their intention to publish the research.
Nitin Gupta, Vice President of Engineering at WhatsApp, thanked the researchers for their "responsible partnership" and told the media that work was already in progress on systems to protect against scraping. He stated that the research helped stress-test new protective mechanisms.
The study's authors confirm that after countermeasures were implemented, the methods they used no longer work—accounts are now blocked in case of mass scraping attempts.
Data Handling and Limitations
The researchers emphasize that they have deleted all collected data. Meta representatives state that they found no evidence of this attack vector being used by malicious actors. It should be noted that user messages are protected by end-to-end encryption and were not accessible to the researchers.