Atroposia MaaS Platform Offers Subscription-Based RAT with Integrated Vulnerability Scanner
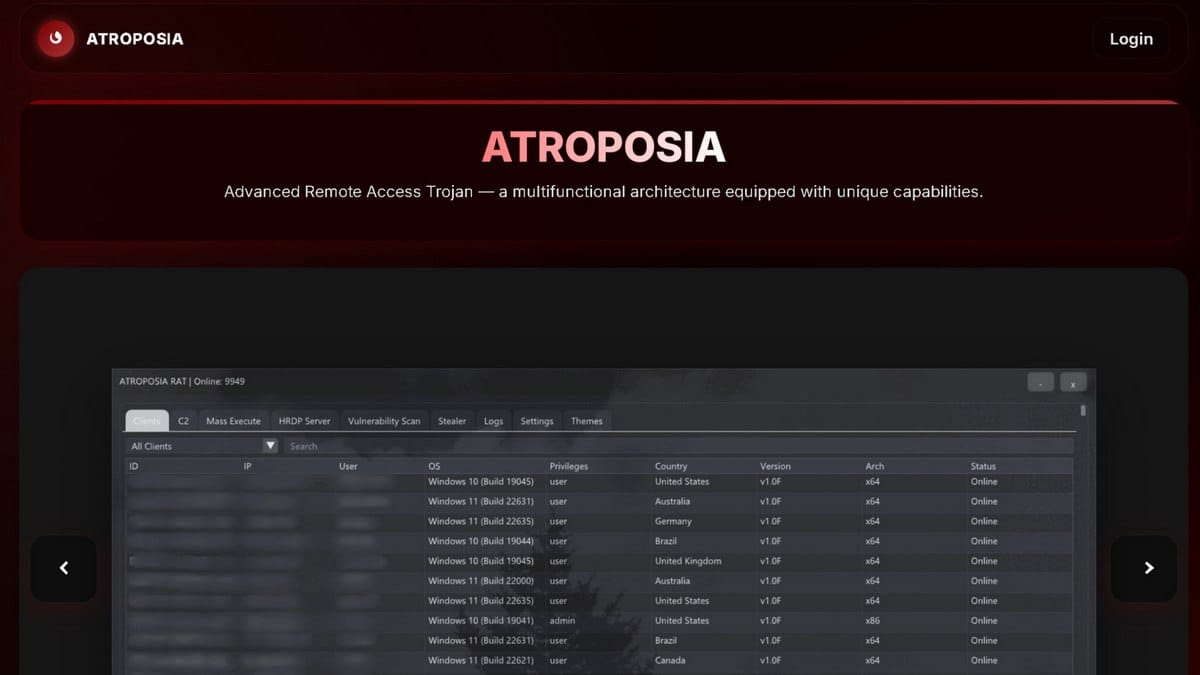
A new Malware-as-a-Service platform is democratizing sophisticated cyberattacks by offering a feature-rich remote access trojan for just $200 per month, complete with built-in vulnerability scanning capabilities that enable attackers to identify and exploit weaknesses across enterprise networks.
Varonis Threat Labs researchers have uncovered Atroposia, a subscription-based malware platform that packages advanced intrusion tools into an accessible service requiring minimal technical expertise. The platform exemplifies the continuing industrialization of cybercrime, where complex attack capabilities are commoditized and sold to low-skilled threat actors.
Modular Architecture and Evasion Capabilities
Atroposia employs a modular design that communicates with command-and-control (C&C) infrastructure over encrypted channels. The malware incorporates User Account Control (UAC) bypass techniques to escalate privileges on Windows systems, establishing persistent and stealthy access that resists detection.
For the monthly subscription fee, customers receive a comprehensive remote access trojan with the following core modules:
HRDP Connect: Invisible Remote Desktop Access
This module launches hidden remote desktop sessions that operate entirely in the background, enabling attackers to control infected systems without visible indicators. Threat actors can open applications, access documents and email, and interact with the system as if physically present at the keyboard—all while remaining invisible to the victim.
Varonis researchers emphasize that standard remote access monitoring tools may fail to detect these covert sessions, as the module is specifically designed to evade conventional security controls.
File Manager and Data Exfiltration
Functioning like Windows File Explorer, the File Manager module grants attackers complete file system access. Operators can view directory structures, copy files, delete evidence, and execute arbitrary programs.
The integrated "grabber" component automates data theft by searching for target files based on extensions or keywords. Once identified, sensitive data is packaged into password-protected ZIP archives and exfiltrated to C&C servers using in-memory techniques that minimize forensic artifacts on the compromised system.
Stealer and Clipboard Monitoring
The Stealer module harvests stored credentials, cryptocurrency wallet data, and messaging application files. Concurrently, a real-time clipboard manager intercepts everything users copy—including passwords, API keys, and cryptocurrency addresses—capturing sensitive information the moment it enters the clipboard.
This dual approach ensures attackers obtain both stored credentials and transient secrets that might otherwise evade detection.
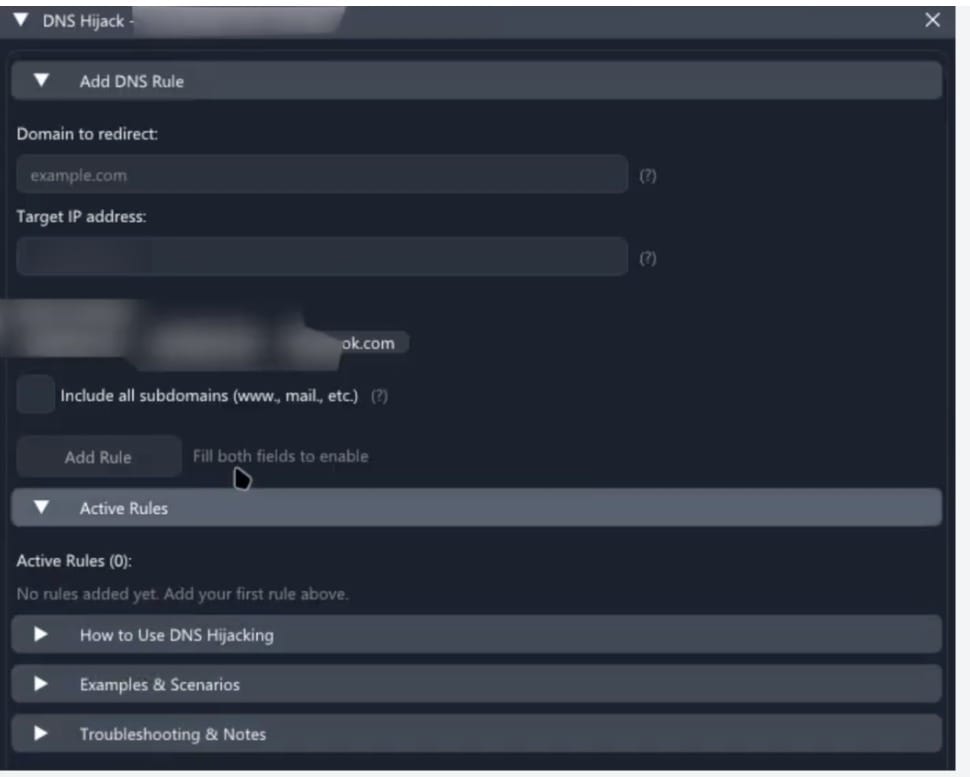
DNS Hijacking for Traffic Redirection
Atroposia's DNS hijacking module modifies host-level domain name resolution, replacing legitimate domains with attacker-controlled IP addresses. Victims are silently redirected to malicious infrastructure while believing they're accessing legitimate services.
This capability enables multiple attack vectors:
- Credential harvesting through convincing phishing pages
- Man-in-the-Middle (MitM) attacks intercepting sensitive communications
- Distribution of trojanized software updates
- Malicious advertisement injection
- Data exfiltration via specially crafted DNS requests
The host-level manipulation is particularly effective because it occurs before browser-based security controls can intervene.
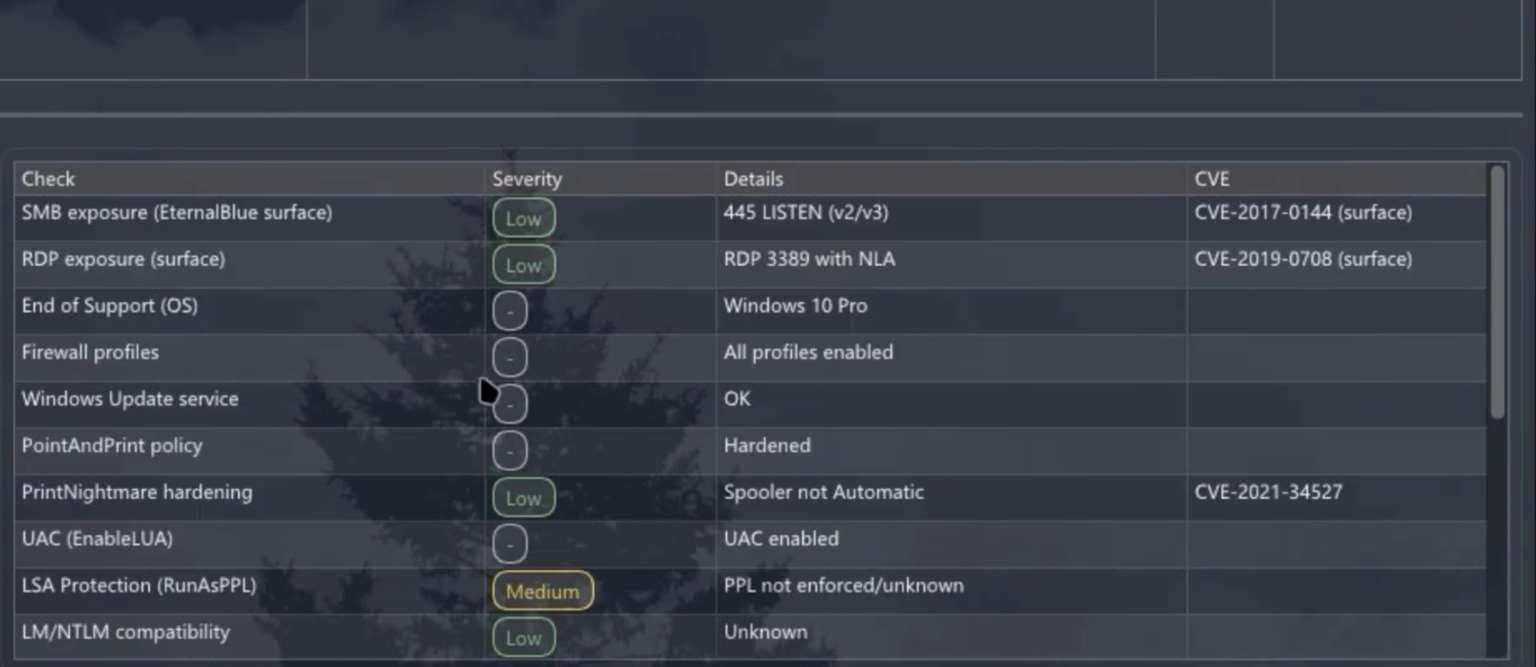
Built-in Vulnerability Scanner: The Enterprise Threat
Perhaps most concerning is Atroposia's integrated vulnerability scanner, which conducts automated reconnaissance on compromised systems.
The scanner identifies:
- Unpatched security vulnerabilities
- Insecure system configurations
- Outdated software versions
- Vulnerable network services
Results are compiled into reports delivered to malware operators, providing actionable intelligence for privilege escalation and lateral movement. In corporate environments, this functionality transforms a single compromised workstation into a beachhead for broader network penetration.
"This module is particularly dangerous in corporate environments," Varonis researchers warned. "The malware can detect an outdated VPN client or a privilege escalation vulnerability, which could ultimately be used to penetrate deeper into the victim's infrastructure."
The scanner doesn't limit its reconnaissance to the infected host—it actively probes the local network for additional vulnerable systems, mapping potential lateral movement pathways across the enterprise.
The Democratization of Cybercrime
Varonis positions Atroposia within a broader trend of cybercrime commoditization. Like similar platforms including SpamGPT (AI-powered phishing generation) and MatrixPDF (PDF-based malware delivery), Atroposia dramatically lowers the technical barrier to conducting sophisticated attacks.
For a modest monthly subscription comparable to streaming services, threat actors with minimal technical skills gain access to capabilities previously reserved for advanced persistent threat groups. This "attacks-by-subscription" model fundamentally changes the threat landscape by enabling volume-based attacks from a wider pool of adversaries.
Implications and Defenses
The emergence of platforms like Atroposia necessitates a reassessment of enterprise security strategies. Organizations can no longer assume that sophisticated multi-stage attacks require equally sophisticated adversaries—the MaaS model has decoupled attack complexity from attacker skill.
Recommended Defensive Measures:
- Implement advanced endpoint detection and response (EDR) solutions capable of identifying anomalous behavior patterns rather than relying solely on signature-based detection
- Monitor for hidden remote desktop sessions using specialized tools that detect background RDP connections
- Deploy network segmentation to limit lateral movement opportunities
- Maintain aggressive patch management to eliminate vulnerabilities before they're discovered by automated scanners
- Implement DNS security with monitoring for host file modifications and suspicious resolution patterns
- Conduct regular vulnerability assessments to identify weaknesses before attackers do
- Enable multi-factor authentication across all services to mitigate credential theft impact
- Monitor clipboard activity for unusual patterns, particularly in privileged user sessions
The Atroposia platform underscores an uncomfortable reality: as cybercrime continues industrializing, organizations face an expanding threat from a growing population of subscription-armed adversaries. Defensive strategies must evolve accordingly, prioritizing behavioral detection and defense-in-depth architectures over perimeter-focused security models.


