Astaroth Banker Uses GitHub to Evade Blocking

McAfee Labs has uncovered a new campaign distributing the Astaroth banking trojan, which now leverages GitHub as part of its command infrastructure to evade takedowns and remain operational even when its servers are blocked.
“Instead of relying solely on traditional command-and-control (C2) servers, which can be shut down, the attackers are using GitHub repositories to host malware configurations,” the researchers explained. “When defenders disrupt their infrastructure, Astaroth simply downloads new configurations from GitHub and continues operating.”
Campaign Activity and Geographic Focus
According to McAfee, Astaroth’s activity is concentrated in Brazil, but recent attacks have also been observed in Mexico, Uruguay, Argentina, Paraguay, Chile, Bolivia, Peru, Ecuador, Colombia, Venezuela, and Panama. The trojan is primarily designed to steal credentials from users of banking and cryptocurrency platforms across Latin America.
Infection Chain and Execution
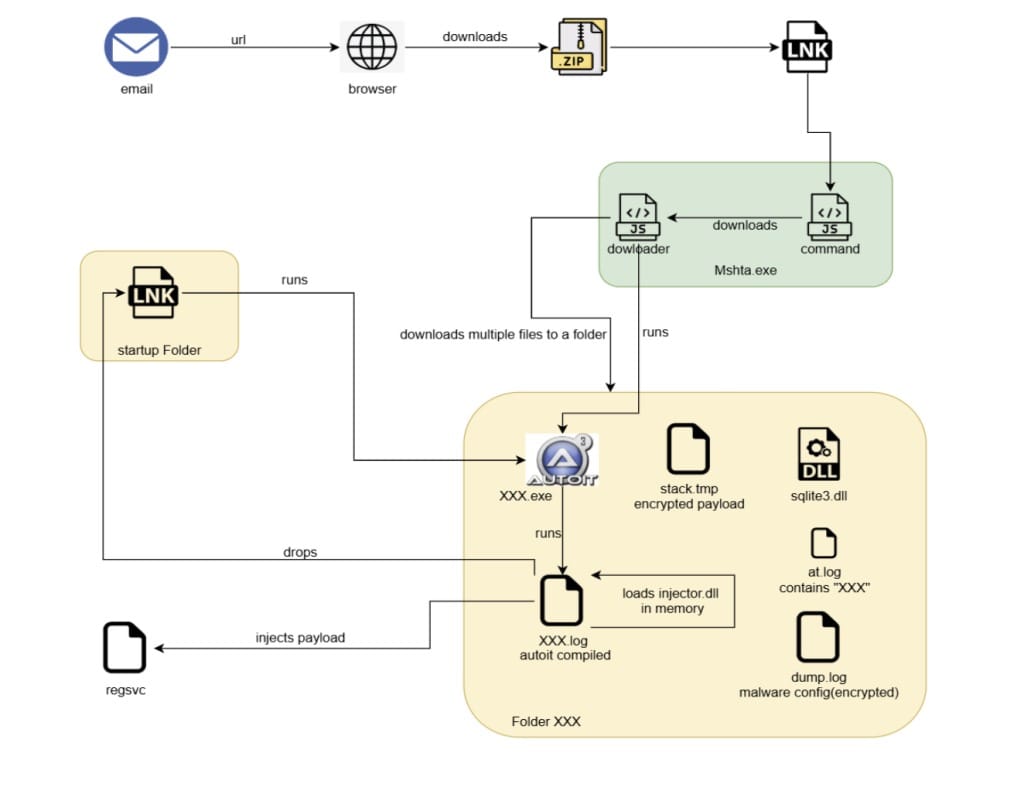
The latest attacks follow Astaroth’s familiar playbook. The campaign begins with a phishing email disguised as a DocuSign notification, which lures victims into downloading a compressed Windows shortcut file (.LNK).
When executed, the LNK file launches obfuscated JavaScript that retrieves additional scripts from an external server. These scripts then download a set of payloads, including an AutoIt script responsible for executing embedded shellcode. The shellcode injects a Delphi DLL into a new RegSvc.exe process — the stage where the Astaroth trojan becomes active.
Data Theft and Stealth Mechanisms
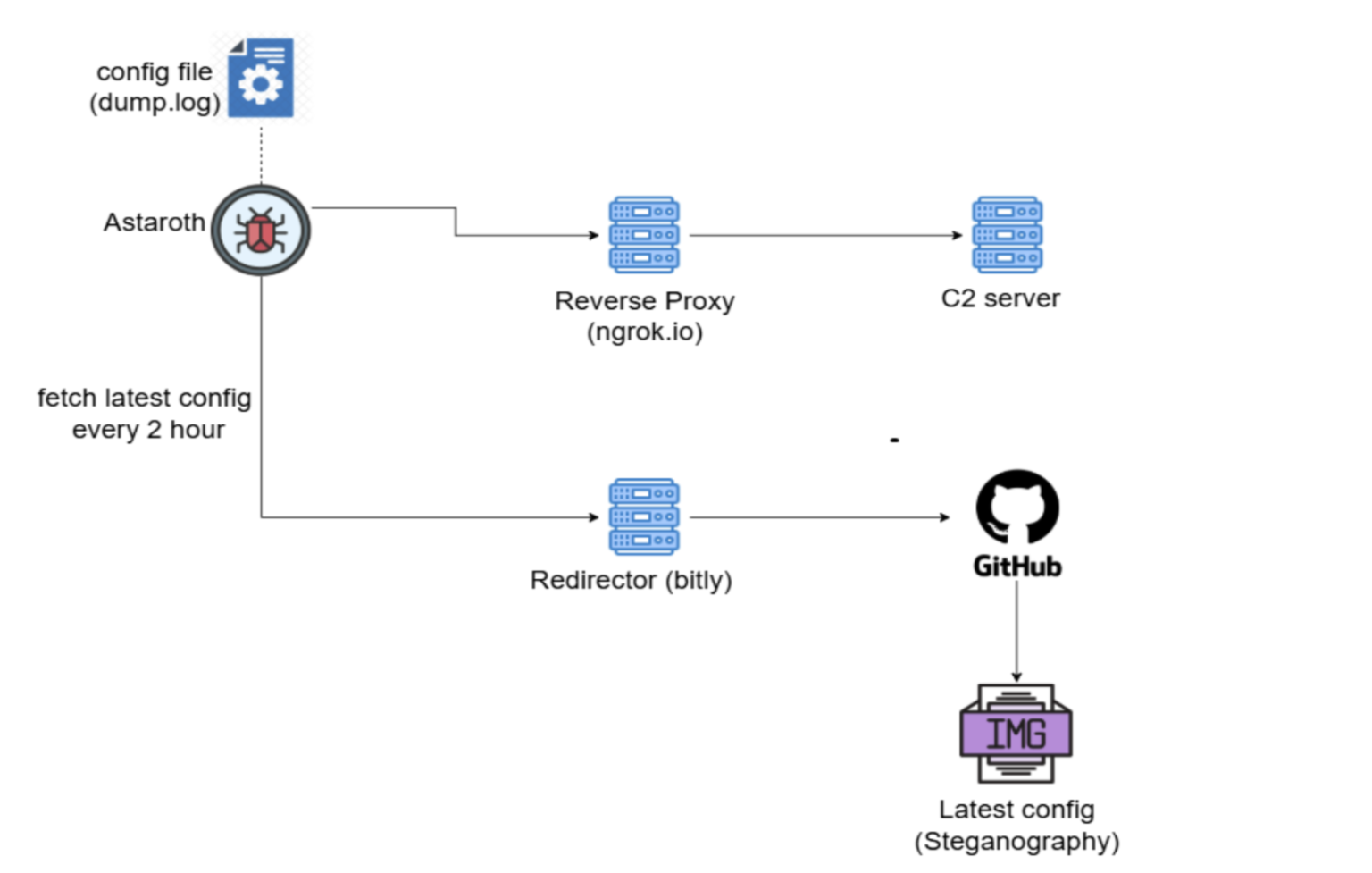
Written in Delphi, Astaroth monitors browser sessions and captures credentials when users visit banking or cryptocurrency websites. Stolen data is exfiltrated through the Ngrok reverse proxy, a legitimate tunneling service often abused by cybercriminals.
The malware’s targets include major Brazilian financial institutions such as caixa.gov.br, itau.com.br, and santandernet.com.br, along with cryptocurrency sites like binance.com and localbitcoins.com.
To resist analysis, Astaroth automatically terminates itself if it detects emulators, debuggers, or analysis tools such as IDA Pro, Wireshark, or WinDbg. It also ensures persistence by creating an LNK file in the Windows Startup folder, which relaunches the AutoIt loader after reboot.
Abuse of GitHub and Regional Filtering
What makes this campaign distinct is its use of GitHub as a fallback control channel. If Astaroth’s C2 servers are taken offline, it retrieves updated configurations hidden within image files on GitHub using steganography—concealing malicious code in seemingly harmless content.
In addition, the malware employs geofencing, allowing its initial infection URL to be accessed only from specific regions. It checks the system locale and halts execution if the language is English or the region is set to the United States.
Temporary Disruption
McAfee reports that, in coordination with GitHub’s security team, the identified repositories have been removed, temporarily disrupting Astaroth’s operations. However, the use of trusted cloud platforms for malware resilience underscores the growing challenge of detecting malicious activity hidden within legitimate services.