Approximately 50,000 Asus Routers Compromised in WrtHug Campaign

Researchers at SecurityScorecard have uncovered a large-scale malicious campaign called WrtHug, which has compromised approximately 50,000 Asus routers worldwide. Attackers are exploiting six known vulnerabilities, primarily targeting older models from the AC and AX series.
Geographic Distribution and Attribution
The majority of infected devices are located in Taiwan, with the remainder distributed across Southeast Asia, Russia, Central Europe, and the United States. Notably, no infections have been detected in China—suggesting a possible Chinese origin for the attackers, though insufficient evidence exists for definitive attribution.
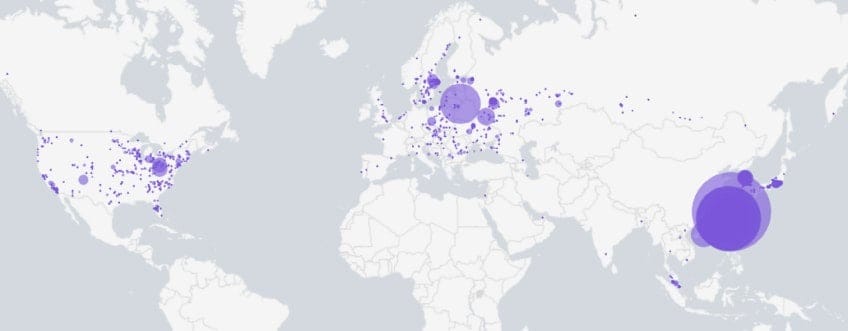
WrtHug bears significant similarities to the AyySSHush campaign that GreyNoise analysts documented in May 2025.
Attack Methodology
The attacks begin by exploiting command injection vulnerabilities and other known flaws:
- CVE-2023-41345 through CVE-2023-41348: OS command injection via token modules
- CVE-2023-39780: Command injection (also used in AyySSHush)
- CVE-2024-12912: Arbitrary command execution
- CVE-2025-2492: Authentication bypass on routers with AiCloud enabled (critical severity)
The last vulnerability is the most dangerous. In April, Asus warned that this flaw could be exploited remotely via a specially crafted request and requires no authentication on routers with AiCloud enabled.
Per SecurityScorecard's analysis, AiCloud—a built-in feature enabling remote cloud access on many Asus routers, effectively turning them into private cloud servers—has become the primary entry point for attackers.
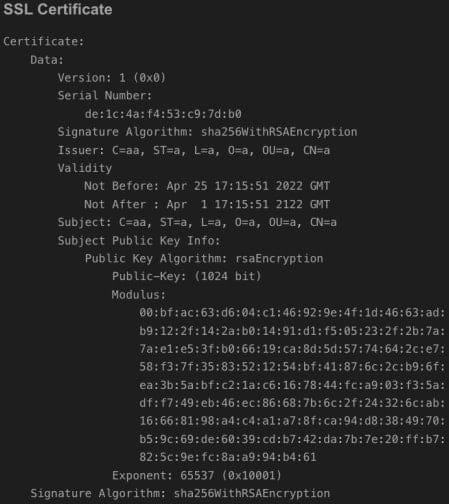
Detection and Indicators of Compromise
The primary indicator of WrtHug compromise is a self-signed TLS certificate installed in AiCloud, replacing the default certificate on 99% of infected devices. This new certificate stands out due to its unusually long validity period: 100 years, compared to the standard 10-year lifespan.
Using this signature, researchers identified approximately 50,000 infected IP addresses. The following Asus router models were found to be affected:
- Asus Wireless Router 4G-AC55U
- Asus Wireless Router 4G-AC860U
- Asus Wireless Router DSL-AC68U
- Asus Wireless Router GT-AC5300
- Asus Wireless Router GT-AX11000
- Asus Wireless Router RT-AC1200HP
- Asus Wireless Router RT-AC1300GPLUS
- Asus Wireless Router RT-AC1300UHP
Post-Compromise Behavior
Similar to the AyySSHush attacks, hackers do not update the firmware on compromised routers, leaving them vulnerable to exploitation by other threat actors.
Researchers believe the compromised routers may serve as an operational relay network for Chinese hacking operations—proxying traffic and obscuring the attackers' command-and-control infrastructure. However, the report contains no specific details regarding the attackers' post-compromise activities.
Recommendations
Since Asus has already released patches for all exploited vulnerabilities, router owners should update their firmware immediately if they have not done so already. If a device is no longer supported, users should replace it or, at minimum, disable remote access features.
In addition, Asus released patches this month for the critical authentication bypass vulnerability CVE-2025-59367, affecting the DSL-AC51, DSL-N16, and DSL-AC750 routers. Although this vulnerability is not currently being exploited, researchers believe it may soon be added to the attackers' arsenal.