Android Spyware “ClayRat” Targets Russian Users While Masquerading as WhatsApp, TikTok, and YouTube

A new strain of Android spyware called ClayRat is impersonating popular apps such as WhatsApp, Google Photos, TikTok, and YouTube to infect users in Russia. The malware is distributed through Telegram channels and phishing sites, stealing SMS messages, call logs, notifications, photos, and even placing calls on the victim’s behalf.
Researchers from Zimperium reported finding over 600 samples and 50 distinct droppers within just three months, pointing to an active and fast-evolving campaign.
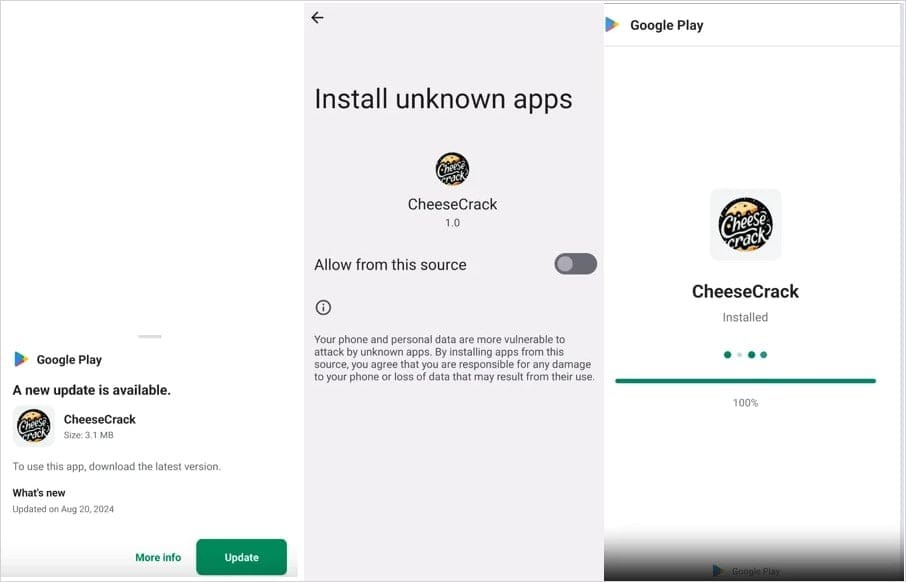
Fake Play Store Pages and Telegram Channels
Attackers behind ClayRat set up phishing websites and register domains that closely mimic legitimate ones. These sites either host the malicious APK files directly or redirect users to Telegram channels, where victims are prompted to download the fake applications.
To make the campaign appear authentic, the operators inflate download counters, post fake reviews, and replicate the Google Play Store interface, complete with detailed installation instructions that walk users through bypassing Android’s built-in security warnings.
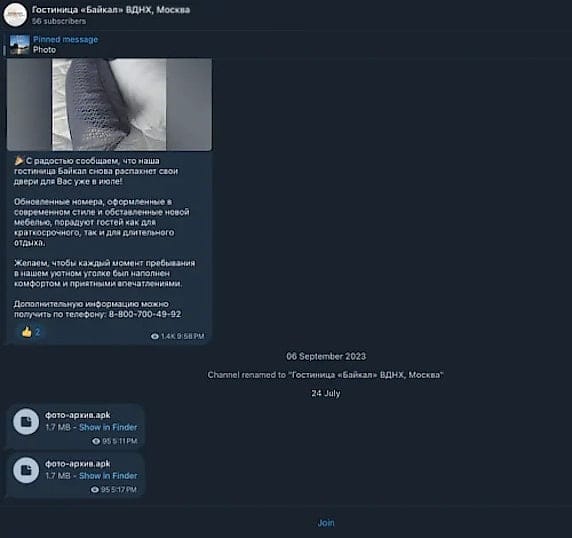
Advanced Dropper and Installation Tactics
Several ClayRat variants act as droppers. When opened, users see a fake Play Store update screen, while the malware secretly extracts and decrypts a hidden payload from the app’s resources.
ClayRat persists using a session-based installation method, which helps it evade restrictions on Android 13 and newer versions. This technique, first documented by ThreatFabric researchers in 2023 during analysis of the SecuriDropper malware, exploits how Android installs applications.
Normally, Android apps use a simple, single-session installation process that hands an APK directly to the system installer. ClayRat instead uses the session-based method — the same one used by Play Store apps to install multiple “split” APKs at once. Because this method mimics legitimate system behavior, it bypasses the Restricted Settings protection designed to block unverified installations.
From Spyware to Spammer
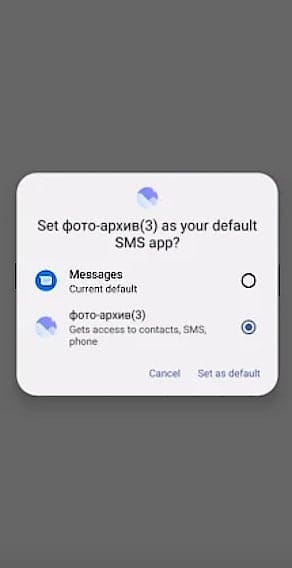
Once installed, ClayRat immediately requests permissions to access messages, contacts, and notifications. It then sets itself as the default SMS handler, gaining complete control of all messages. The spyware can intercept SMS, modify message databases, and send malicious links to every contact in the victim’s address book — turning each device into a new distribution point.
Command-and-Control Functions
ClayRat communicates with its command-and-control (C&C) server using AES-GCM–encrypted traffic and supports at least twelve remote commands, including:
get_apps_list— list installed appsget_calls— extract call logsget_camera— take a photo with the front cameraget_sms_list— exfiltrate SMS messagesmesssms— mass-send SMS to contactssend_sms/make_call— send messages or place callsnotifications/get_push_notifications— intercept alertsget_device_info— collect device identifiersget_proxy_data— configure a proxy WebSocket and schedule tasksretransmishion— forward SMS to attacker-controlled numbers
This wide range of commands makes ClayRat capable of full surveillance, credential theft, and worm-like propagation.
Detection and Mitigation
Zimperium has shared indicators of compromise (IOCs) with Google. Play Protect now detects and blocks both known and emerging variants of ClayRat, though users who sideload APKs from untrusted sources remain at risk.
Security researchers warn that the campaign demonstrates how threat actors continue to exploit social engineering and Android installation loopholes despite Google’s ongoing efforts to tighten mobile security.
Final Paragraph (Flow & Closure)
ClayRat’s sophistication highlights the resurgence of localized Android spyware targeting specific regions. By combining fake app stores, Telegram distribution, and installation methods once thought limited to legitimate channels, attackers are blurring the line between user trust and exploitation — once again reminding Android users that “Install from unknown sources” remains one of the most dangerous settings on any device.


