Android Malware "Albiriox" Targets Over 400 Banking and Cryptocurrency Apps

Cybersecurity researchers at Cleafy identified a new Android banking Trojan called Albiriox that targets more than 400 applications worldwide—including banking, financial, cryptocurrency, trading, payment, investment, and gaming platforms. Russian-speaking hackers are distributing the malware using a "malware-as-a-service" (MaaS) model.
Albiriox gives attackers complete control over infected smartphones, allowing them to conduct fraudulent transactions directly from the victim's device through banking and cryptocurrency applications.
The malware first appeared on hacker forums in late September 2025. By October, the developers launched commercial distribution, charging $720 per month for access to the Trojan.
Attack Distribution Methods
Attackers spread Albiriox through fake dropper applications using social engineering tactics. The first major campaign targeted Austrian residents with SMS messages in German, containing links to fraudulent Google Play Store pages that mimicked the Penny supermarket chain application.
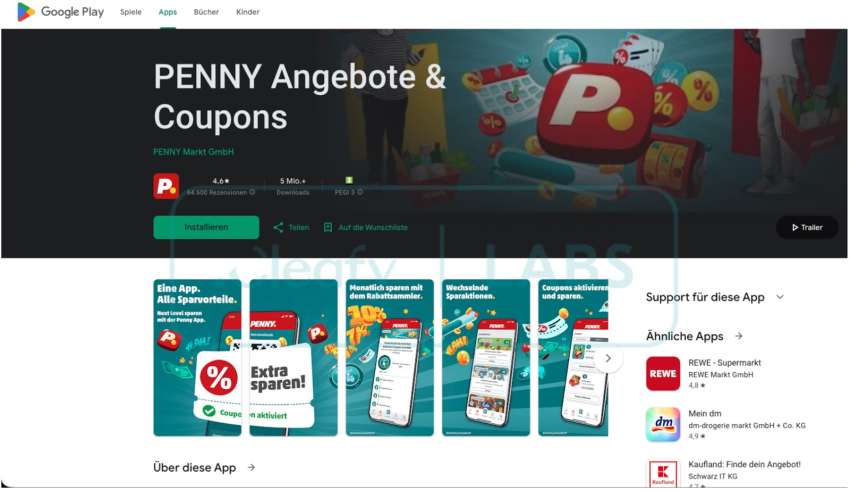
The APK file downloaded directly from attacker-controlled infrastructure, bypassing Google Play Store security. After the initial attack wave, the phishing operation evolved: landing pages no longer offered direct APK downloads. Instead, victims were prompted to enter mobile phone numbers, with attackers claiming the app download link would arrive via WhatsApp.
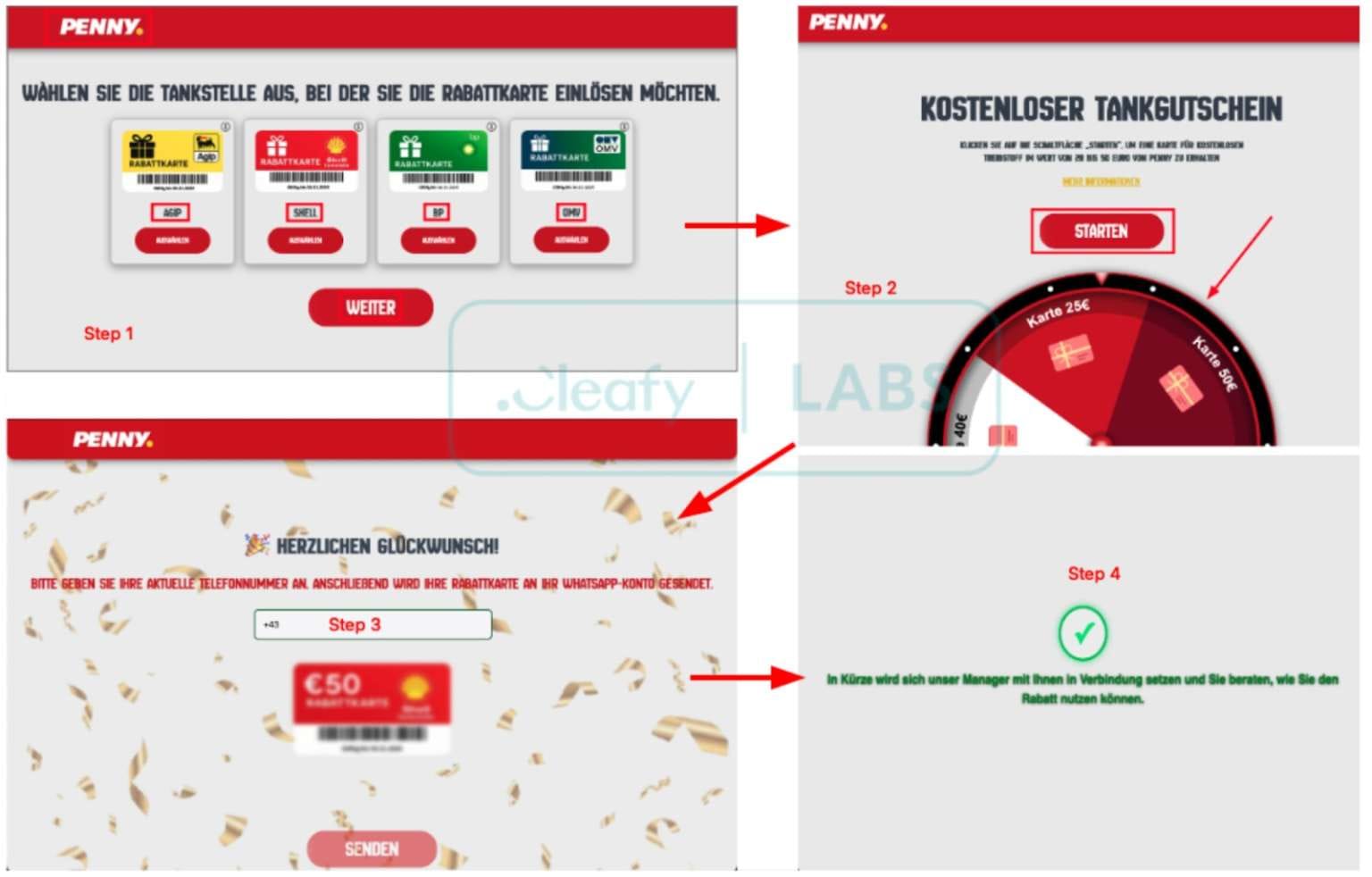
The campaign specifically targeted Austrian users—only Austrian phone numbers were accepted—and victim data was transmitted to the attackers' Telegram bot. After installation, the malicious application disguised itself as a system update and requested permissions to install additional apps, ultimately downloading the malware's main module.
Technical Capabilities
Albiriox establishes remote access through VNC (Virtual Network Computing), enabling hackers to control infected devices in real-time, extract confidential information, and display blank screens while muting device audio to hide their activities.
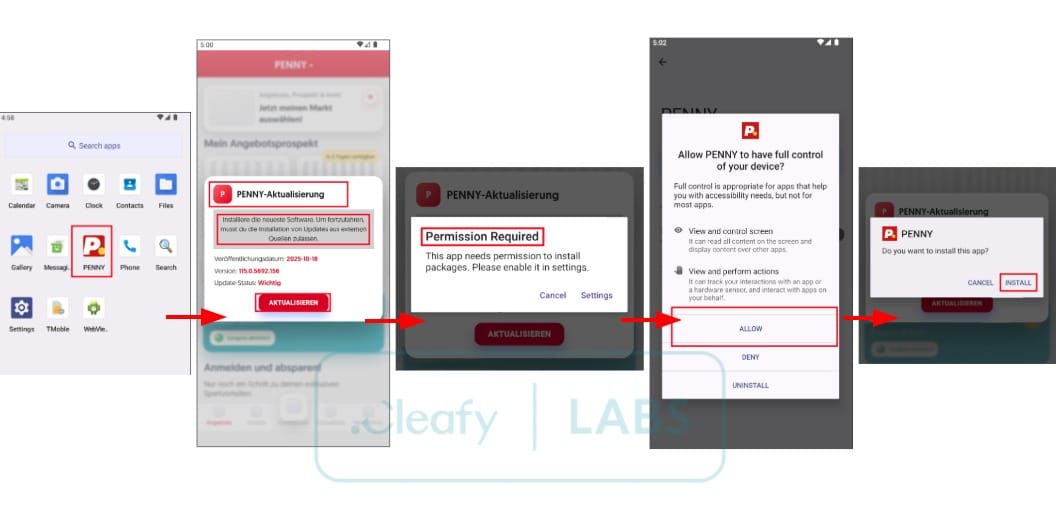
One VNC implementation leverages Android's Accessibility services to capture the complete user interface. This technique bypasses FLAG_SECURE protection—a security feature banking and cryptocurrency applications use to prevent screen recording and data interception.
Like other Android banking Trojans, Albiriox employs overlay attacks, displaying fake screens over legitimate applications to steal login credentials. The malware can imitate system update screens or show a black screen so victims remain unaware of background malicious activity.
Evasion Techniques
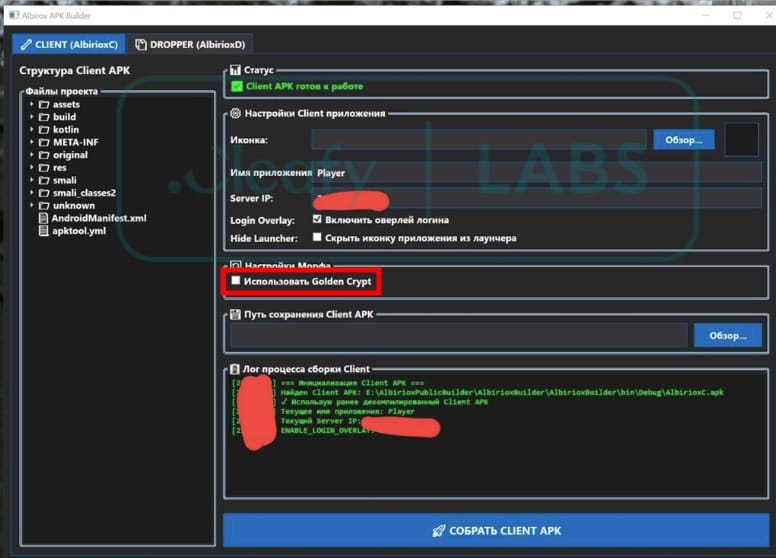
To circumvent security solutions, Albiriox operators receive access to a customizable builder integrated with Golden Crypt, a third-party encryption service. This integration helps the malware evade static threat detection and increases infection success rates.
Cleafy researchers concluded that Albiriox demonstrates all characteristics required for effective on-device fraud: VNC-based remote control, automation through Accessibility services, targeted overlay attacks, and dynamic credential interception. These capabilities allow attackers to bypass traditional authentication and fraud detection systems while operating within the victim's legitimate session.


