Android-Based Digital Photo Frames Load Malware During Startup

Security researchers have discovered that Uhale digital photo frames running Android contain multiple critical vulnerabilities. Even more concerning, some models automatically download and execute malware during the boot process.
Discovery and Disclosure Attempt
Researchers from Quokka, a mobile security firm, analyzed the Uhale application and identified activity linked to two malware families: Mezmess and Vo1d.
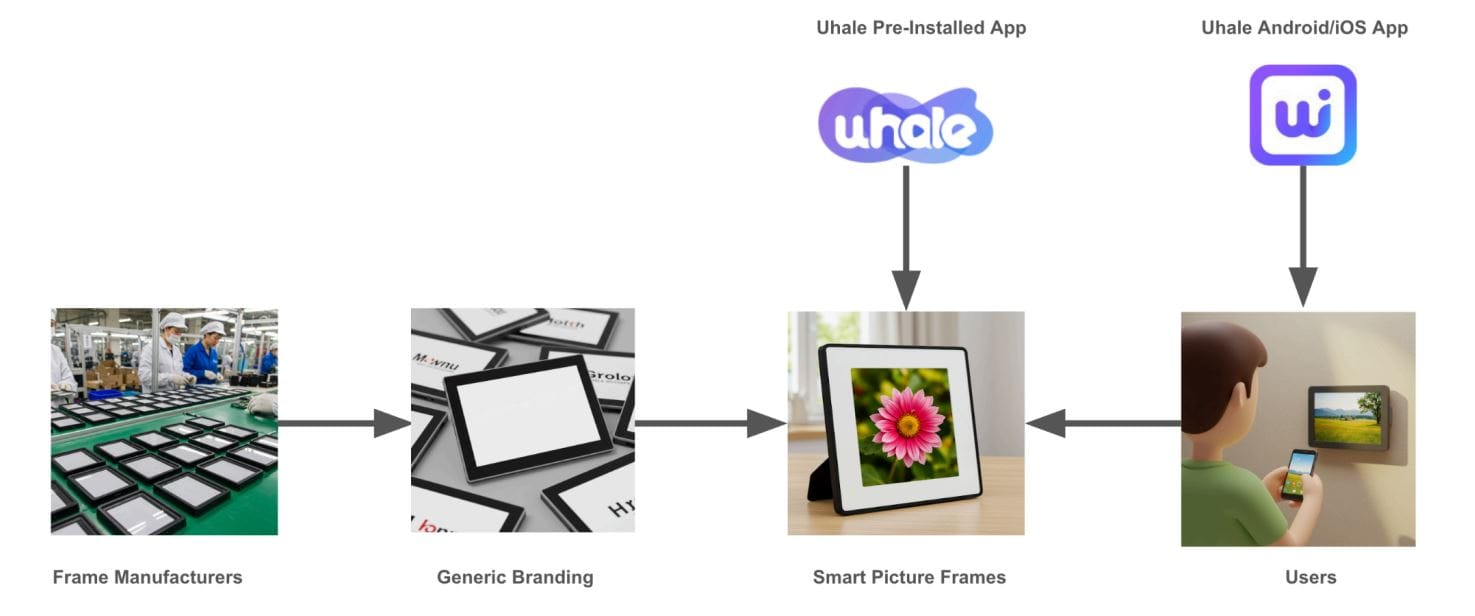
In May 2025, the team attempted to notify ZEASN—the Chinese company behind the Uhale platform (now operating as Whale TV)—about these security issues. The developers never responded. ZEASN's platform powers digital photo frames sold under numerous brand names.

The Malware Delivery Process
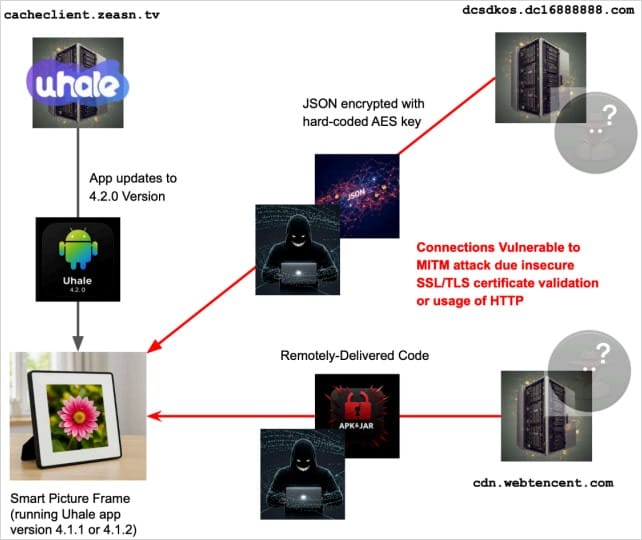
Immediately after powering on, many of the tested photo frame models download malicious payloads from Chinese servers. Here's how the infection occurs:
- During boot, the device checks for Uhale application updates
- The device updates to version 4.2.0 and reboots
- After restarting, the updated application downloads and executes malware
- The malicious JAR/DEX file saves to the Uhale application directory
- The malware loads and executes on every subsequent boot
It remains unclear whether version 4.2.0 became malicious through intentional developer action or because ZEASN's update infrastructure was compromised. The malware has been linked to the Vo1d botnet—which includes millions of infected devices—and the Mzmess malware family. Researchers confirmed these connections through package prefixes, string names, endpoints, delivery mechanisms, and other technical artifacts.
Critical Vulnerabilities Discovered
Beyond the automatic malware installation (which didn't occur on all tested devices), researchers found numerous security flaws. Quokka's report details 17 vulnerabilities, 11 of which have received CVE identifiers. The most serious include:
CVE-2025-58392 and CVE-2025-58397: An insecure TrustManager implementation allows man-in-the-middle attacks to inject fake encrypted responses, leading to remote code execution with root privileges.
CVE-2025-58388: During application updates, unprocessed filenames pass directly to shell commands, enabling command injection and remote installation of arbitrary APKs.
CVE-2025-58394: All tested photo frames shipped with SELinux disabled, root access enabled by default, and public AOSP test keys—meaning the devices are fully compromised out of the box.
CVE-2025-58396: The pre-installed application runs a file server on TCP port 17802 that accepts unauthenticated file uploads. Any device on the local network can write or delete arbitrary files.
CVE-2025-58390: The application's WebView ignores SSL/TLS errors and allows mixed content, enabling attackers to inject or intercept displayed data for phishing and content spoofing attacks.
Additional Security Weaknesses
The researchers also identified:
- A hardcoded AES key used to decrypt sdkbin responses
- Adups update components in several photo frame models
- Outdated libraries with known vulnerabilities
- Weak cryptographic patterns and hardcoded keys throughout the application
Scale of the Problem
Determining the exact number of affected devices is difficult because most vulnerable photo frames are sold under different brand names without mentioning the Uhale platform. However, available metrics suggest widespread adoption:
- The Uhale application has over 500,000 downloads from Google Play
- More than 11,000 App Store reviews
- Approximately 1,000 reviews for Uhale-branded photo frames on Amazon
Recommendations
Quokka researchers recommend purchasing smart devices only from verified manufacturers that:
- Use official Android images without firmware modifications
- Support Google services
- Include built-in malware protection
- Provide regular security updates
For users who already own these devices, the safest option is to stop using them until patches become available—if they ever do.


