Akira Ransomware Gang's Apache OpenOffice Claims Don't Add Up
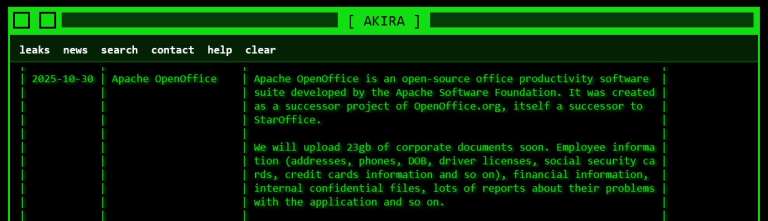
The Akira ransomware group posted a bold claim on October 30, 2025: they'd breached Apache OpenOffice and stolen 23 GB of sensitive data. According to their darknet announcement, the haul includes employee personal information—home addresses, phone numbers, birth dates, driver's license copies, social security numbers, and bank card details. They also mentioned financial documents, internal confidential data, and application issue reports.
There's one problem. Apache Software Foundation representatives say the hackers are bluffing. The organization doesn't have that data because it doesn't exist in the first place.
Understanding Apache OpenOffice's Structure
Apache OpenOffice is a popular open-source office suite that serves as a free alternative to Microsoft Office. The software includes tools for documents, spreadsheets, presentations, databases, and vector graphics. It supports Word and Excel formats and runs on all major platforms—factors that contribute to its widespread adoption in organizations looking to reduce software costs.
However, OpenOffice's development model differs significantly from commercial software companies. This difference matters when evaluating Akira's claims.
Why the Claims Fall Apart
ASF representatives addressed the allegations directly: "Apache OpenOffice is an open-source project where all contributors work on a voluntary basis. We do not have salaried employees. Accordingly, the set of data described by the hackers simply does not exist."
In addition, the foundation confirmed they're investigating the claims but emphasized they haven't received any ransom demands from the attackers. This absence is notable—ransomware groups typically contact victims with payment instructions before going public.
The nature of OpenOffice's development process makes Akira's claims even more questionable. The project operates entirely through public developer mailing lists. Bug reports, feature requests, and problem discussions are inherently public and accessible to anyone. Per the foundation's statement, there are no private employee databases or confidential financial records to steal.
What This Means for Threat Analysis
This situation highlights an important pattern in ransomware operations: not every claim on a leak site represents a genuine breach. Ransomware groups sometimes post false claims to maintain their reputation, pressure other victims, or create confusion in the security community.
In my opinion, security teams should verify breach claims through multiple sources before taking action. ASF's transparent response—explaining their organizational structure and why the claimed data couldn't exist—provides a model for how organizations should address questionable breach allegations.
Furthermore, this incident reminds us that understanding an organization's operational structure is essential for both attackers and defenders. Akira's operators either failed to research their target properly or deliberately posted false claims knowing the information would eventually be disputed.
The foundation continues to investigate how Akira gained enough access to make these claims, even if the specific data doesn't exist. Organizations should remember that even unsuccessful attack attempts reveal information about threat actor tactics and targeting patterns worth analyzing.


