Aisuru Botnet Shatters DDoS Records with 29.7 Tbps Attack

A massive botnet dubbed Aisuru has set a new record for distributed denial-of-service attacks, reaching 29.7 terabits per second (Tbps) in peak traffic volume. The attack, which lasted only 69 seconds, demonstrates how compromised IoT devices and routers can be weaponized to generate unprecedented levels of malicious network traffic.
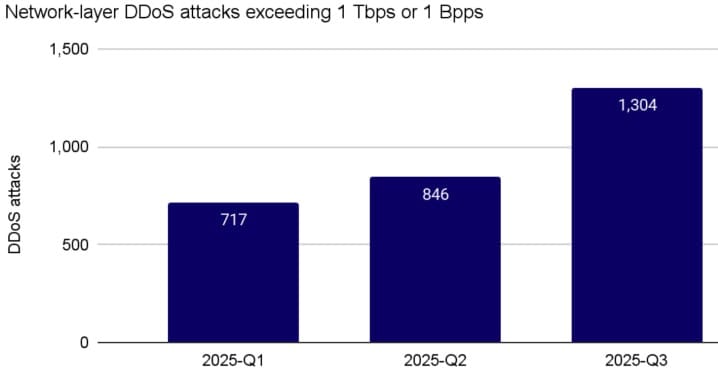
Per Cloudflare, Aisuru operators control between one and four million infected devices worldwide. The botnet has launched over 1,300 DDoS attacks in just three months, with nearly 45% classified as "hyper-volumetric"—attacks exceeding 1 Tbps or 1 billion packets per second.
Record-Breaking Attack Details
The 29.7 Tbps attack occurred in the third quarter of 2024 and targeted infrastructure protected by Cloudflare's network. Despite its brief 69-second duration, the assault used UDP flooding techniques to bombard an average of 15,000 ports per second with junk traffic.
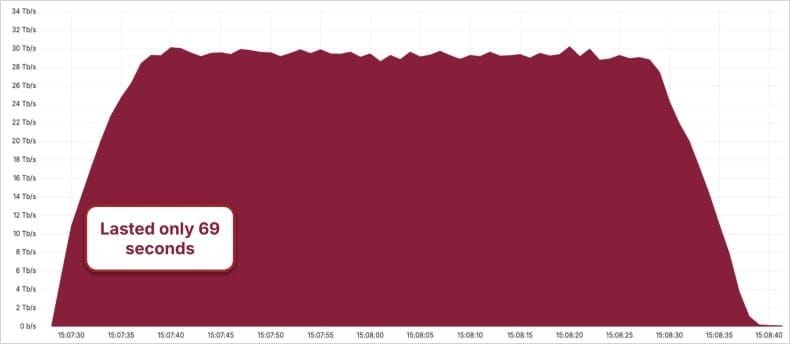
Cloudflare successfully mitigated the attack, but the scale raises serious concerns about network infrastructure vulnerability. The company warns that even internet service providers not directly targeted by Aisuru attacks may experience operational disruptions due to network congestion from traffic volume alone.
"If an Aisuru attack can disrupt the internet infrastructure of the United States (even though providers were not the direct target of the attackers), imagine what would happen if this power were directed at unprotected critical infrastructure, healthcare, emergency services, or military systems," Cloudflare researchers wrote in their analysis.
Botnet Operations and Targets
Aisuru operates on a "botnet-for-hire" model where criminals rent portions of compromised devices to attack competitor websites and services. The botnet primarily consists of hacked routers and IoT devices, exploited through known vulnerabilities or simple brute-force credential attacks.
Aisuru targets span multiple industries:
- Gaming services
- Hosting providers
- Telecommunications companies
- Financial sector organizations
Per Cloudflare's data, the company has mitigated 2,867 Aisuru attacks since the beginning of 2024, demonstrating the botnet's sustained operational tempo.
Previous Records and Comparative Context
The 29.7 Tbps attack surpasses Aisuru's previous record of 22.2 Tbps, which Cloudflare also successfully blocked. Microsoft reported separately that Aisuru targeted Azure with a 15.72 Tbps DDoS attack originating from 500,000 IP addresses simultaneously.
These figures represent a significant escalation from historical DDoS attack volumes. The record-breaking nature of Aisuru's capabilities highlights how botnet operators continue to scale their operations by compromising additional devices and refining attack techniques.
Rising Trend in Hyper-Volumetric Attacks
Aisuru's activities reflect a broader industry trend toward more powerful DDoS attacks. Per Cloudflare statistics for the third quarter of 2024:
- 1,304 hyper-volumetric attacks recorded (exceeding 1 Tbps or 1 billion packets per second)
- 189% increase in attacks exceeding 100 million packets per second compared to the previous quarter
- 227% increase in attacks exceeding 1 Tbps
- 3,780 DDoS attacks per hour mitigated on average by Cloudflare
Despite this escalation in attack power, most DDoS attacks remain brief—lasting less than ten minutes. However, short duration does not minimize impact.
"An attack may last only a few seconds, but the consequences can be devastating, and recovery takes much longer," Cloudflare explained. "Engineering teams have to undertake a complex, multi-stage process: bringing critical systems back online, checking data integrity in distributed systems, and restoring secure and stable service for customers."
Geographic Distribution
Per Cloudflare's analysis, DDoS attacks in the third quarter originated primarily from:
- Indonesia
- Thailand
- Bangladesh
- Ecuador
Primary targets included organizations in:
- China
- Turkey
- Germany
- Brazil
- United States
This geographic distribution reflects both the global nature of compromised IoT device networks and the international scope of cybercriminal operations.
Implications for Organizations
The emergence of Aisuru and similar botnets capable of multi-terabit attacks presents challenges for organizations of all sizes. Traditional DDoS mitigation strategies designed for attacks in the gigabit range may prove inadequate against hyper-volumetric assaults.
"We have entered an era where the complexity and scale of DDoS attacks have rapidly evolved, surpassing what we could have imagined just a few years ago. As a result, many organizations are struggling to keep up with this changing threat landscape," Cloudflare concluded.
Recommendations
Organizations should consider the following measures to protect against hyper-volumetric DDoS attacks:
- Deploy cloud-based DDoS mitigation - On-premises solutions cannot handle terabit-scale attacks; cloud-based services with massive bandwidth capacity are necessary
- Implement rate limiting - Configure network infrastructure to limit traffic from individual sources and protocols
- Secure IoT devices - Change default credentials, apply firmware updates, and segment IoT devices from critical networks to prevent botnet recruitment
- Monitor traffic patterns - Establish baseline network behavior to detect anomalous traffic spikes quickly
- Develop incident response procedures - Prepare engineering teams for rapid recovery processes, including system restoration and data integrity verification
- Consider redundancy - Distribute services across multiple providers and geographic regions to maintain availability during attacks
The Aisuru botnet demonstrates that DDoS attacks have evolved from nuisance-level disruptions to potential threats against critical infrastructure. Organizations relying on internet-facing services must reassess their defensive capabilities against attacks measured in terabits rather than gigabits.
Technical Summary:
- Peak Attack Volume: 29.7 Tbps
- Attack Duration: 69 seconds
- Attack Method: UDP flooding
- Ports Targeted: Average 15,000 per second
- Botnet Size: 1-4 million compromised devices
- Primary Device Types: Routers, IoT devices
- Attack Model: Botnet-for-hire
- Total Aisuru Attacks (2024): 2,867 mitigated by Cloudflare
- Hyper-Volumetric Rate: 45% of Aisuru attacks exceed 1 Tbps


