A Vulnerability in Figma MCP Allowed Remote Code Execution Overview
Researchers from Imperva have disclosed details about a now-patched vulnerability in the Figma developer MCP (Model Context Protocol) server. The flaw allowed remote attackers to execute arbitrary code and was assigned CVE-2025-53967 with a CVSS score of 7.5.
Technical Details
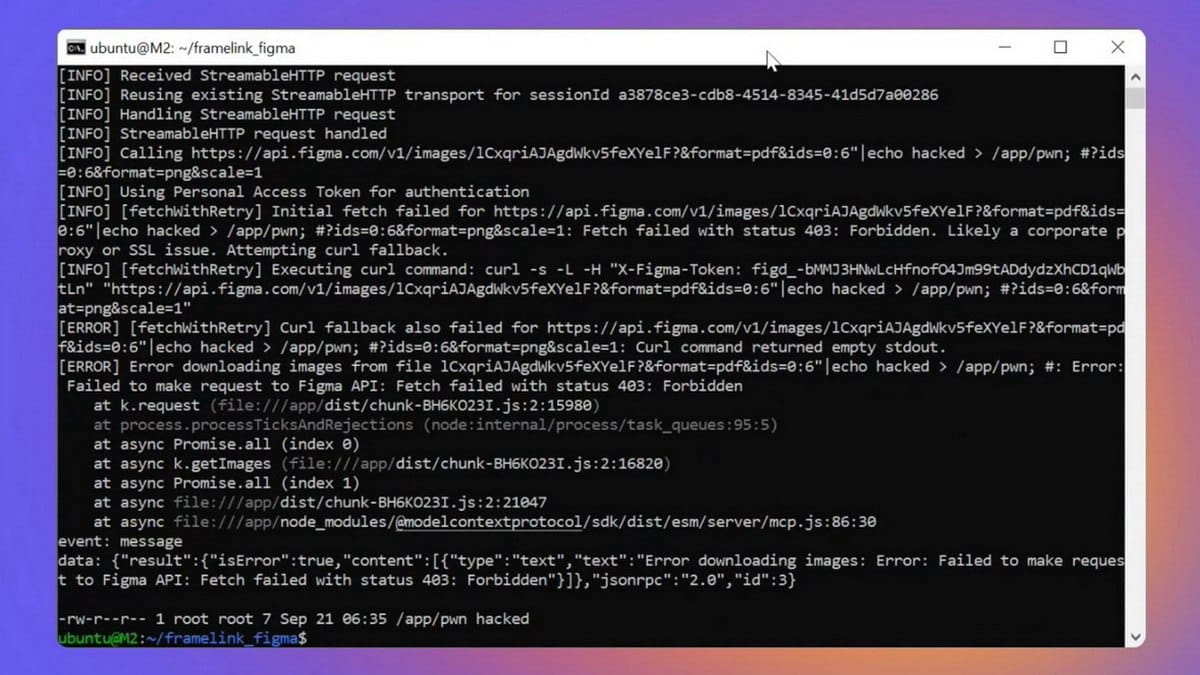
The issue stemmed from unsanitized user input, resulting in a command injection vulnerability.
According to the GitHub advisory, “The server forms and executes shell commands by directly inserting unvalidated user data into the command line, creating a risk of shell metacharacter injection (|, >, &&, and others).”
Successful exploitation could lead to remote code execution with the privileges of the affected process.
Exploitation Scenario
Framelink’s Figma MCP enables AI agents such as Cursor to interact with Figma via automation tools. Attackers could exploit this by tricking an MCP client into performing unwanted actions through an indirect prompt injection.
Imperva researchers, who discovered the flaw in July 2025, called it an “architectural miscalculation” within a fallback mechanism that allowed remote code execution and exposed developers to possible data leakage.
Root Cause
The vulnerability originated in the file src/utils/fetch-with-retry.ts.
When a standard API fetch request failed, the system executed a curl command via child_process.exec, enabling shell injection.
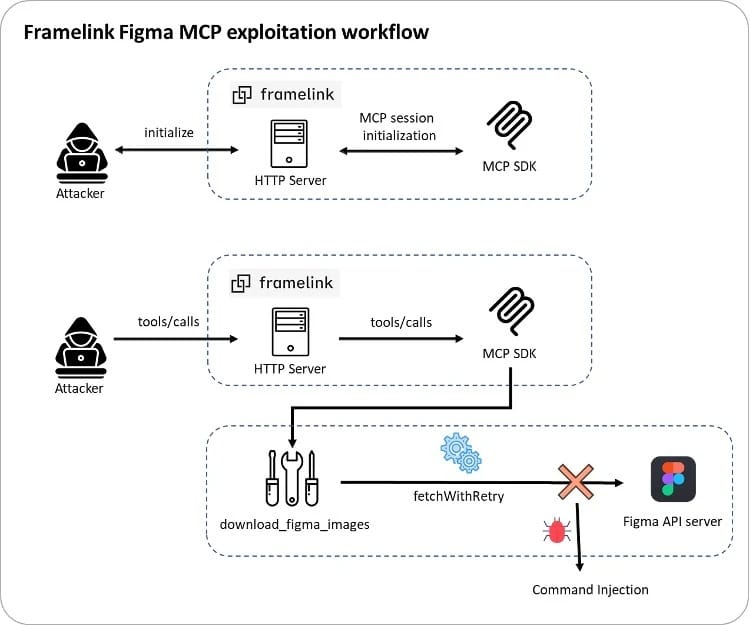
The attack chain unfolds as follows:
- The MCP client sends an Initialize request to the MCP endpoint to obtain a session ID.
- The client then issues a JSONRPC request using the
tools/callmethod to invoke functions such asget_figma_dataordownload_figma_images. - If the standard fetch request fails, the fallback curl command is executed with untrusted input — leading to command injection.
Potential Impact
An attacker on the same network — such as on public Wi-Fi or a compromised corporate LAN — could exploit CVE-2025-53967 by sending crafted requests to the vulnerable MCP server.
Alternatively, a user could be lured into visiting a malicious site that triggers the exploit through a DNS rebinding attack.
Patch and Recommendations
The vulnerability was patched in Figma developer MCP version 0.6.3, released on September 29, 2025.
Imperva advises avoiding child_process.exec with untrusted data and replacing it with child_process.execFile, which mitigates injection vectors.
“As AI development tools evolve and become more widespread, it is crucial that security keeps pace with innovation,” Imperva’s researchers concluded. “This bug serves as a reminder that even local tools can become a convenient entry point for attackers.”


