A Critical Bug in Redis Threatens Thousands of Servers

The Redis security team has released patches for a critical vulnerability that allows attackers to remotely execute arbitrary code an issue that has existed unnoticed for nearly 13 years.
The flaw, tracked as CVE-2025-49844 and rated 10.0 (Critical) on the CVSS scale, is a use-after-free vulnerability exploitable by authenticated attackers through specially crafted Lua scripts — a feature enabled by default in Redis.
From Lua Sandboxes to Full Compromise
Successful exploitation of the bug allows attackers to escape the Lua sandbox, trigger a use-after-free condition, establish a reverse shell for persistent access, and ultimately achieve remote code execution (RCE) on the targeted Redis host.
Once compromised, attackers could:
- Steal credentials
- Deploy malware or backdoors
- Extract sensitive data from Redis memory
- Move laterally across connected systems
- Leverage stolen information to access cloud environments
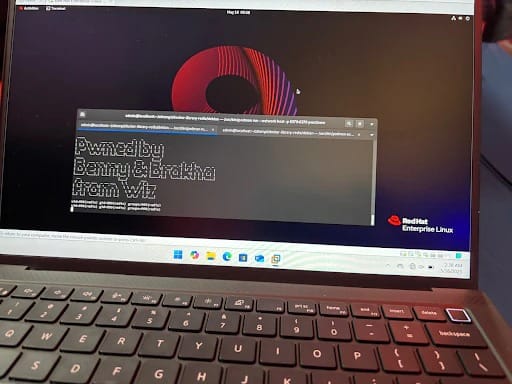
“This gives the attacker full access to the host system, allowing them to extract, destroy, or encrypt sensitive data, seize resources, and facilitate lateral movement in cloud environments,” explained researchers from Wiz, who demonstrated the vulnerability — dubbed RediShell — at the Pwn2Own Berlin competition in May 2025.
Scope of Exposure
While exploitation requires some level of authenticated access, Wiz analysts identified approximately 330,000 publicly accessible Redis instances, including at least 60,000 that do not require authentication.
This means that, in practice, a significant portion of Redis deployments remain directly exposed to the internet, dramatically increasing the risk of widespread compromise.
Mitigation and Recommendations
Both Redis and Wiz have urged administrators to apply the latest patches immediately, especially for internet-facing servers.
Administrators should also harden their environments by:
- Enabling authentication and disabling unauthenticated access
- Turning off Lua scripting and other unnecessary features
- Running Redis under a non-root user
- Enabling detailed logging and monitoring
- Restricting network access to authorized IPs or subnets only
- Implementing firewall or VPC-level access controls
A Persistent Threat Across All Versions
“RediShell (CVE-2025-49844) is a critical vulnerability affecting all versions of Redis, as the root cause lies within the underlying Lua interpreter,” Wiz specialists warned. “Given the hundreds of thousands of internet-exposed instances, this issue represents a serious risk to organizations across all industries.”
Summary
Redis, one of the most popular in-memory databases, has become an attractive target due to its integration into modern cloud and microservice architectures.
The RediShell vulnerability underscores the importance of not only patching promptly but also re-evaluating exposure levels and security configurations — especially in production systems that were never meant to be directly accessible from the open internet.


