40 Million Downloads: How Malicious Apps Flooded Google Play in One Year
Google Play hosted 239 malicious applications over the past year. Users downloaded them more than 42 million times.
Zscaler, a cybersecurity firm, tracked these threats between June 2024 and May 2025. Their findings show attacks on mobile devices increased 67% year-over-year. The primary threats: banking trojans, spyware, and adware.
Why Mobile Attacks Are Growing
Hackers are changing tactics. They're moving away from counterfeit bank cards and focusing on mobile payments instead. The shift makes sense—more people use their phones for banking and purchases.
Their methods include phishing, smishing (SMS phishing), SIM swapping, and other payment fraud schemes. All of them rely on social engineering rather than technical exploits.
Last year, Zscaler found about 200 malware samples in Google Play. This year, that number jumped to 239.
What's Getting Through
Adware dominated the threat landscape at 69% of all cases. The Joker info-stealer came in second at 23%.
Spyware saw the most dramatic increase—220% more common than the previous year. The most prevalent families remain SpyNote, SpyLoan, and BadBazaar. These tools conduct surveillance, enable blackmail, and steal personal data.
Who's Getting Hit
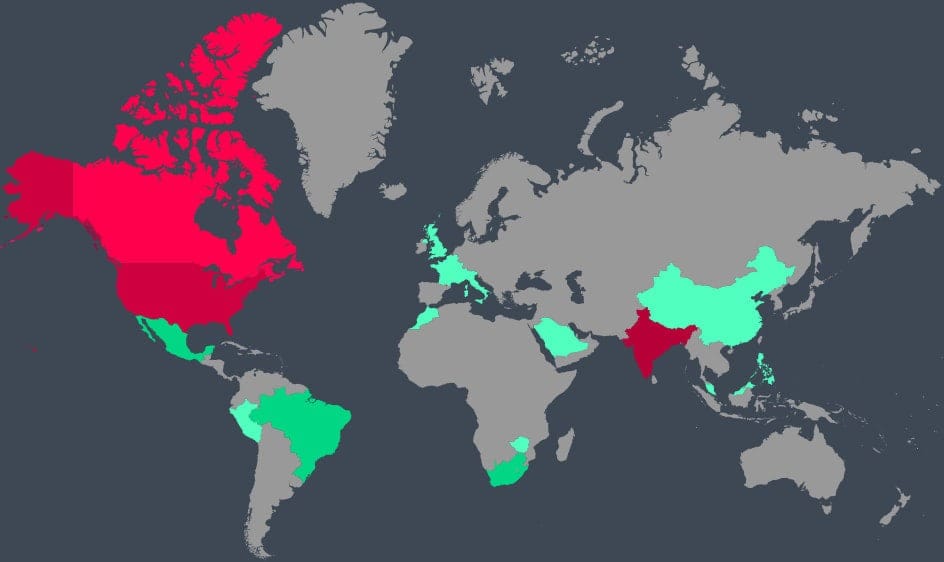
Users in India, the United States, and Canada faced the most attacks—55% of the total. But the growth rates in Italy and Israel are alarming: infections increased between 800% and 4,000% year-over-year in those countries.
Three Malware Families to Watch
Zscaler's annual report highlights three particularly dangerous threats:
Anatsa — A banking trojan that repeatedly sneaks onto Google Play disguised as useful utilities. It targets over 830 banks and cryptocurrency platforms, stealing login credentials and financial data.
Android Void (Vo1d) — A backdoor that infects TV set-top boxes running outdated versions of Android Open Source Project (AOSP). It has compromised at least 1.6 million devices. These boxes often run old software that never receives security updates.
Xnotice — A Remote Access Trojan (RAT) targeting job seekers in the oil and gas industry, particularly in Iran and Arabic-speaking regions. It steals banking details, two-factor authentication codes, and SMS messages.
How to Protect Yourself
The basic security practices still work:
Install updates as soon as they're available. Outdated software is the easiest target.
Avoid applications that request access to Accessibility services unless absolutely necessary. Malware uses these permissions to monitor everything you do on your device.
Run Google Play Protect scans regularly. It's built into your device—use it.
Don't download applications you don't need. Every app is a potential entry point.
Beyond Phones
Researchers also noted a rise in attacks on Internet of Things (IoT) devices, especially routers. Attackers exploit vulnerabilities to infect these devices, then add them to botnets or use them as proxy servers for delivering malware.
Your router is as much a target as your phone. Check for firmware updates and change default passwords.
The Bigger Picture
Forty-two million downloads of malicious apps from an official store is a failure of vetting processes. Google has detection systems in place, but malware developers keep finding ways around them.
In my opinion, the problem isn't just technical—it's economic. Malware authors can make money faster than platform operators can detect and remove threats. Until the economic incentives change, this pattern will continue.
For users, the lesson is clear: official stores are safer than alternatives, but they're not perfectly safe. You still need to practice basic security hygiene. Read permissions carefully, check reviews, and question whether you really need that app.
The 67% increase in mobile attacks tells us where criminals are focusing their efforts. They go where the money is, and right now, that's mobile payments and personal data on smartphones.


