131 Chrome Extensions Used to Spam WhatsApp Users in Brazil

Researchers have identified 131 extensions in the official Chrome Web Store that automate actions on WhatsApp Web and were used to send mass spam to Brazilian users. The cluster shares a single codebase, identical design patterns, and common infrastructure, and it currently accounts for roughly 20,905 active users, according to analysts at security firm Socket.
One codebase, many clones
Socket’s analysis shows the extensions are essentially clones: same scripts, same backend, same messaging workflow. Although they appear under different names and logos, most are published by developer accounts using the labels WL Extensão and WLExtensao. Researchers observed uploads and updates to the extensions as recently as October 17, 2025, and estimate the campaign has been active for at least nine months.
“This is not classic malware; it is high-risk spam automation that violates platform policies,” says Kirill Boychenko, a Socket specialist. “The code is injected directly into the WhatsApp Web page, operating alongside WhatsApp’s own scripts, and automates mass messaging and scheduling in a way that bypasses anti-spam protections.”
How the abuse works
The extensions inject JavaScript into web.whatsapp.com, automating tasks that normally require user interaction: composing messages, scheduling sends, and batching contacts. By mimicking legitimate client-side behavior and doing much of the work inside the user’s browser, the extensions attempt to circumvent WhatsApp’s built-in rate limits and anti-spam measures. The result: large-scale unsolicited message campaigns that appear to originate from valid user sessions.
A franchised operation and a white-label offer
Although names and icons vary, researchers link the proliferation to an apparent franchising model built on an original product, ZapVende, developed by DBX Tecnologia. ZapVende is advertised as a CRM-style tool for WhatsApp Web — “message automation, bulk messaging, a visual sales funnel,” the store listings promise — and DBX reportedly markets a white-label reseller program.
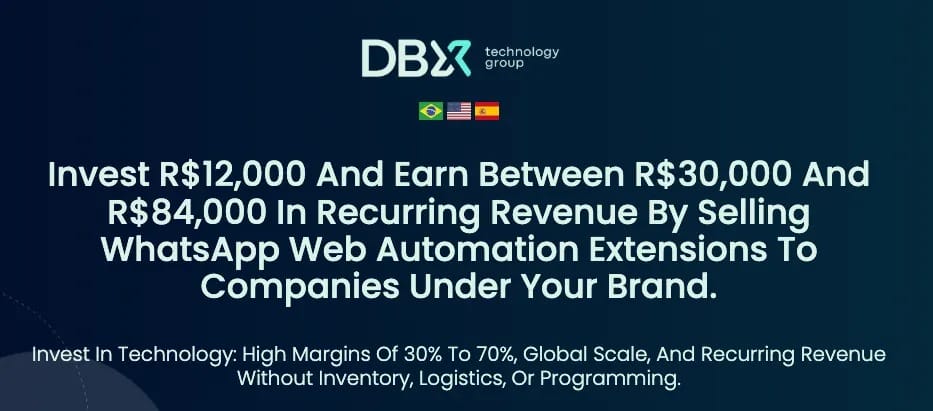
Socket found marketing material that positions the product for resellers: operators are offered the ability to rebrand the extension and sell it under new names, while DBX allegedly advertises potential monthly returns between 30,000 and 84,000 BRL (≈ $5,550–$15,540 USD) for an initial investment of 12,000 BRL (≈ $2,220 USD). Researchers also discovered YouTube videos from DBX that explain methods to bypass WhatsApp’s anti-spam controls.
Spam at scale, policies ignored
Socket emphasizes that the extensions violate Chrome Web Store rules on spam and abusive behavior — for example, the store forbids publishing multiple extensions with duplicative functionality. Yet the ecosystem persists because of the clone-and-republish approach and the commercial incentives for resellers.
“The cluster consists of virtually identical copies distributed across different developer accounts. They are sold for mass unsolicited messaging and automate sending messages via web.whatsapp.com without user confirmation,” Boychenko says. “The goal is to sustain mass spam campaigns while bypassing anti-spam systems.”
What users and platform owners should do
- Users: Remove any untrusted WhatsApp-related extensions and audit browser extensions for unfamiliar entries. If in doubt, disable extensions and sign out of WhatsApp Web sessions.
- Enterprises: Block or monitor browser extension installs via group policy and endpoint controls; consider restricting access to web.whatsapp.com from managed devices.
- Platform owners: The Chrome Web Store should enforce duplicative-functionality rules more aggressively and accelerate takedowns where white-label abuse is evident. WhatsApp should continue to harden Web client telemetry and rate-limit heuristics used to detect automation originating from injected scripts.


